Setup Docker for CTF
Overview
I’m using Docker to solve the hackthebox machine. It’s so simple for me to use. Because Ubuntu has been my host machine for several years, and docker supports host networks in linux-based operating systems, but Windows does not. You can also connect the openvpn in docker. If you are using Windows, it will be difficult for you to use because it does not support host networks and you will have some difficulty using the VPN.
Why we need docker for CTF
Docker containers require fewer installations since they share many of their resources with the host system. A container often takes up less space and utilises less RAM and CPU time than a virtual machine. It boot up in a few seconds or less, whereas virtual machines can take several minutes.
Installing the docker for Parrot
sudo apt install docker
sudo apt install docker.ioRemoving a docker image
installed for example with : docker pull bannsec/bloodhound
┌─[✗]─[puck@parrot-lt]─[~/htb/blackfield] └──╼ $sudo docker image rm bannsec/bloodhound --force
Installing the docker for Ubuntu
Setup the repo
Update the apt package index and install packages to allow apt to use a repository over HTTPS:
sudo apt-get update
sudo apt-get install \
ca-certificates \
curl \
gnupg \
lsb-release
Add Docker’s official GPG key:
curl -fsSL https://download.docker.com/linux/ubuntu/gpg | sudo gpg --dearmor -o /usr/share/keyrings/docker-archive-keyring.gpg
Use the following command to set up the stable repository.
echo \
"deb [arch=$(dpkg --print-architecture) signed-by=/usr/share/keyrings/docker-archive-keyring.gpg] https://download.docker.com/linux/ubuntu \
$(lsb_release -cs) stable" | sudo tee /etc/apt/sources.list.d/docker.list > /dev/null
Install Docker Engine
Update the apt package index, and install the latest version of Docker Engine and containerd, or go to the next step to install a specific version:
sudo apt-get update
sudo apt-get install docker-ce docker-ce-cli containerd.io
To run Docker without root
Add your user to the docker group.
sudo usermod -aG docker $USER
Log out and log back in so that your group membership is re-evaluated.
Installation completed now you can run the docker.
reference: https://docs.docker.com/engine/install/ubuntu/
root@speedtest-dr01:~$ sudo docker run -it --rm -v /etc/hosts:/etc/hosts -w /root/htb --network host -v $(pwd):/root/htb --cap-add=NET_ADMIN --device /dev/net/tun --name htb parrotsec/security /bin/bash
┌─[root@speedtest-dr01]─[~/htb]
└──╼ #uname -a
Linux speedtest-dr01 5.15.0-37-generic #39-Ubuntu SMP Wed Jun 1 19:16:45 UTC 2022 x86_64 GNU/Linux
┌─[root@speedtest-dr01]─[~/htb]
└──╼ #msfconsole
######## #
################# #
###################### #
######################### #
############################
##############################
###############################
###############################
##############################
# ######## #
## ### #### ##
### ###
#### ###
msf6 >
####################### ####
#################### ####
################## ####
############ ##
######## ###
######### #####
############ ######
######## #########
##### ########
### #########
###### ############
#######################
# # ### # # ##
########################
## ## ## ##
https://metasploit.com
=[ metasploit v6.1.34-dev ]
+ -- --=[ 2209 exploits - 1171 auxiliary - 395 post ]
+ -- --=[ 615 payloads - 45 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: View advanced module options with
advanced
msf6 >
.
Install the parrot docker image
docker pull parrotsec/security
now you can run the docker container
docker run -it --rm -v /etc/hosts:/etc/hosts -w /root/htb --network host -v $(pwd):/root/htb --cap-add=NET_ADMIN --device /dev/net/tun --name htb parrotsec/security /bin/bash
BusyBox is also available as a Docker container image. But first, ensure that you have already installed Docker.
To pull the BusyBox image, run the command:
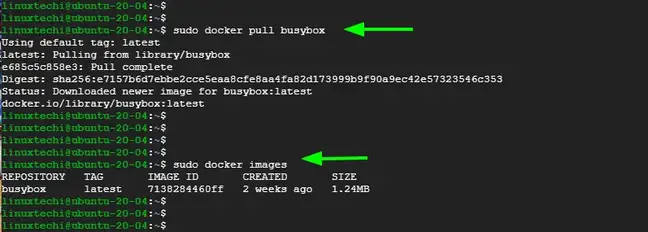
$ sudo docker pull busybox
To confirm the existence of the image, execute:
$ sudo docker images
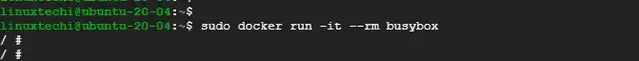
To access the BusyBox shell from the BusyBox container image, simply run the command as follows.
$ sudo docker run -it --rm busybox
From here, you can start running basic Linux commands as you would normally do on a Linux terminal.
That’s IT
.
┌─[puck@parrot-lt]─[/opt]
└──╼ $docker pull byt3bl33d3r/crackmapexec
Using default tag: latest
latest: Pulling from byt3bl33d3r/crackmapexec
42c077c10790: Downloading 4.881MB/31.38MB
42c077c10790: Pull complete
f63e77b7563a: Pull complete
5215613c2da8: Pull complete
9ca2d4523a14: Pull complete
e97cee5830c4: Pull complete
3890a231587c: Pull complete
34672a6043e1: Pull complete
fb64166fca69: Pull complete
ded06f86d72d: Pull complete
Digest: sha256:7d1581f583cdb3d1204ca4ad3a969a5edb7b27e472109c63ec324a1f597ff84f
Status: Downloaded newer image for byt3bl33d3r/crackmapexec:latest
docker.io/byt3bl33d3r/crackmapexec:latest
┌─[puck@parrot-lt]─[/opt]
.
┌─[puck@parrot-lt]─[/opt] └──╼ $sudo docker image list REPOSITORY TAG IMAGE ID CREATED SIZE byt3bl33d3r/crackmapexec latest 6e6c297f0205 14 hours ago 756MB ┌─[puck@parrot-lt]─[/opt] └──╼ $sudo docker run byt3bl33d3r/crackmapexec [*] First time use detected [*] Creating home directory structure [*] Creating default workspace [*] Initializing LDAP protocol database [*] Initializing MSSQL protocol database [*] Initializing RDP protocol database [*] Initializing SMB protocol database [*] Initializing SSH protocol database [*] Initializing WINRM protocol database [*] Copying default configuration file [*] Generating SSL certificate usage: cme [-h] [-t THREADS] [--timeout TIMEOUT] [--jitter INTERVAL] [--darrell] [--verbose] {ldap,mssql,rdp,smb,ssh,winrm} ... ______ .______ ___ ______ __ ___ .___ ___. ___ .______ _______ ___ ___ _______ ______ / || _ \ / \ / || |/ / | \/ | / \ | _ \ | ____|\ \ / / | ____| / | | ,----'| |_) | / ^ \ | ,----'| ' / | \ / | / ^ \ | |_) | | |__ \ V / | |__ | ,----' | | | / / /_\ \ | | | < | |\/| | / /_\ \ | ___/ | __| > < | __| | | | `----.| |\ \----. / _____ \ | `----.| . \ | | | | / _____ \ | | | |____ / . \ | |____ | `----. \______|| _| `._____|/__/ \__\ \______||__|\__\ |__| |__| /__/ \__\ | _| |_______|/__/ \__\ |_______| \______| A swiss army knife for pentesting networks Forged by @byt3bl33d3r and @mpgn_x64 using the powah of dank memes Exclusive release for Porchetta Industries users https://porchetta.industries/ Version : 5.3.0 Codename: Operation C01NS optional arguments: -h, --help show this help message and exit -t THREADS set how many concurrent threads to use (default: 100) --timeout TIMEOUT max timeout in seconds of each thread (default: None) --jitter INTERVAL sets a random delay between each connection (default: None) --darrell give Darrell a hand --verbose enable verbose output protocols: available protocols {ldap,mssql,rdp,smb,ssh,winrm} ldap own stuff using LDAP mssql own stuff using MSSQL rdp own stuff using RDP smb own stuff using SMB ssh own stuff using SSH winrm own stuff using WINRM /usr/local/lib/python3.8/site-packages/requests/__init__.py:109: RequestsDependencyWarning: urllib3 (1.26.9) or chardet (5.0.0)/charset_normalizer (2.0.12) doesn't match a supported version! warnings.warn( ┌─[✗]─[puck@parrot-lt]─[/opt]
We make an alias to run cme easier
┌─[✗]─[puck@parrot-lt]─[/opt]
└──╼ $alias cme='docker run -it --rm --name cme byt3bl33d3r/crackmapexec'
┌─[puck@parrot-lt]─[/opt]
.
┌─[✗]─[puck@parrot-lt]─[/opt]
└──╼ $sudo docker pull cmnatic/rustscan
Using default tag: latest
latest: Pulling from cmnatic/rustscan
df20fa9351a1: Pull complete
a941dc7c08a9: Pull complete
c2f14500ea0b: Pull complete
Digest: sha256:926672637def3162611020f6864d176589a48a2d02e06fbbc61aacf65b8c49fd
Status: Downloaded newer image for cmnatic/rustscan:latest
docker.io/cmnatic/rustscan:latest
┌─[puck@parrot-lt]─[/opt]
.
┌─[puck@parrot-lt]─[/opt]
└──╼ $sudo docker image list
REPOSITORY TAG IMAGE ID CREATED SIZE
byt3bl33d3r/crackmapexec latest 6e6c297f0205 14 hours ago 756MB
cmnatic/rustscan latest 9c545513d6f1 21 months ago 35.3MB
┌─[puck@parrot-lt]─[/opt]
To get started:
Simply run this command against the IP you want to target:
docker run -it --rm --name rustscan rustscan/rustscan:alpine <rustscan arguments here> <ip address to scan>
Note: this will scan the Docker’s localhost, not your own.
Once done, you will no longer need to re-download the image (except when RustScan updates) and can use RustScan like a normal application.
You will have to run this command every time, so we suggest aliasing it to something memorable.
alias rustscan='docker run -it --rm --name rustscan rustscan/rustscan:alpine'
Then we can:
rustscan 127.0.0.1 -t 500 -b 1500 -- -A
┌─[✗]─[puck@parrot-lt]─[/opt] └──╼ $sudo docker pull m4ch1n3s/patator [sudo] password for puck: Using default tag: latest latest: Pulling from m4ch1n3s/patator d519e2592276: Pull complete d22d2dfcfa9c: Pull complete b3afe92c540b: Pull complete b4a142e61dda: Pull complete 7edcdd93e87e: Pull complete 3c5808a393b0: Pull complete 57149c23da8c: Pull complete 0fa50712ae9f: Pull complete 62725c26a7ce: Pull complete 179a19df7234: Pull complete 3d67dd5a5eca: Pull complete beabe7585917: Pull complete cc4e04b7889f: Pull complete d208b74342b9: Pull complete 0cb39c466f0b: Pull complete 01e409349ddf: Pull complete 978ecc442225: Pull complete f1cfa7d6df6a: Pull complete b0b528d2245b: Pull complete Digest: sha256:eea4f4b94553b16f00b6271a172b7175cd0899b77688a9a876f189cf9b9d2e30 Status: Downloaded newer image for m4ch1n3s/patator:latest docker.io/m4ch1n3s/patator:latest ┌─[puck@parrot-lt]─[/opt] └──╼ $sudo docker image list REPOSITORY TAG IMAGE ID CREATED SIZE byt3bl33d3r/crackmapexec latest 6e6c297f0205 18 hours ago 756MB m4ch1n3s/patator latest 7e91f786534f 17 months ago 2.57GB cmnatic/rustscan latest 9c545513d6f1 21 months ago 35.3MB ┌─[puck@parrot-lt]─[/opt]
┌─[✗]─[puck@parrot-lt]─[/opt] └──╼ $docker run -it --rm --name m4ch1n3s/patator "docker run" requires at least 1 argument. See 'docker run --help'. Usage: docker run [OPTIONS] IMAGE [COMMAND] [ARG...] Run a command in a new container ┌─[✗]─[puck@parrot-lt]─[/opt] └──╼ $alias patator='docker run -it --rm --name m4ch1n3s/patator' ┌─[puck@parrot-lt]─[/opt] └──╼ $patator "docker run" requires at least 1 argument. See 'docker run --help'. Usage: docker run [OPTIONS] IMAGE [COMMAND] [ARG...] Run a command in a new container ┌─[✗]─[puck@parrot-lt]─[/opt] └──╼ $
.
┌─[✗]─[puck@parrot-lt]─[/opt]
└──╼ $docker pull mikesplain/openvas
# latest (9)
docker run -d -p 443:443 --name openvas mikesplain/openvas
# 9
docker run -d -p 443:443 --name openvas mikesplain/openvas:9
With the Image ID, you can remove the docker image in the following manner:
docker rmi image_name_or_id --force# Force-stop the container docker container rm --force <container ID> # Delete the image docker image rm <image ID>
.