Cisco Password Cracking and Decrypting Guide
In this guide we will go through Cisco password types that can be found in Cisco IOS-based network devices. We will cover all common Cisco password types (0, 4, 5, 7, 8 and 9) and provide instructions on how to decrypt them or crack them using popular open-source password crackers such as John the Ripper or Hashcat.
Introduction
During penetration tests, it is not uncommon to come across a configuration file of a Cisco network device. It may be a configuration backup found laying somewhere on some computer in the network. It may be a console log output (e.g. from PuTTY) containing Cisco configuration snippets. Or we may just flat out break into some Cisco device configured with default credentials.
The first thing attackers do after they gain access to a Cisco device is that they pull current configuration from the device either by running show running or show running-config command. The attackers are typically looking for sensitive information such as stored credentials, SNMP community strings, network configuration details and so on.
Credentials are naturally the most interesting thing to look for and over the years Cisco has developed number of different methods for storing passwords in their devices. Hence the name Cisco password type.
Common Cisco password types
In the following sections, we will go through all these password types by order from the least secure (most easiest to crack) to the most secure (hardest to crack):
| Cisco Password | Crackability | Best speed | John the Ripper | Hashcat |
| Type 0 | instant | instant | n/a | n/a |
| Type 7 | instant | instant | n/a | n/a |
| Type 4 | easy | 26.4 million per second | --format=Raw-SHA256 |
-m 5700 |
| Type 5 | medium | 1.2 million per second | --format=md5crypt |
-m 500 |
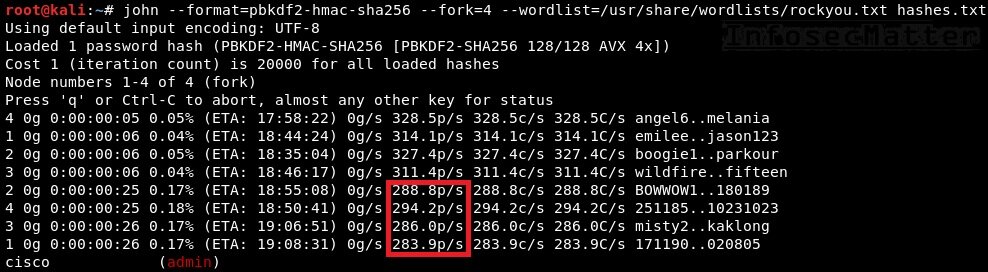
| Type 8 | hard | 11.6 thousand per second | --format=pbkdf2-hmac-sha256 |
-m 9200 |
| Type 9 | very hard | 1.8 thousand per second | --format=scrypt |
-m 9300 |
Disclaimer: All examples and speed measurements in this article were produced on a standard modern laptop equipped with a GPU and 4 CPU cores.
Let’s jump right to it.Cisco type 0 password
Cisco password type 0 is basically clear text password. There is no encryption nor obfuscation. It is the oldest and the most insecure method of storing passwords in Cisco devices. It should never be used.
The following example shows type 0 password found in a Cisco configuration:
username admin privilege 15 password 0 P@ssw0rdAs you can see, there is really nothing to crack or decrypt. We can clearly see that the admin user has a password of P@ssw0rd.
Cisco type 7 password
This password type uses Vigenère cipher which is essentially a simple alphabetical substitution encryption. The algorithm is reversible and thus it can be deciphered instantly into a plain text without any need for cracking.
The following example shows type 7 password found in a Cisco configuration:
username admin privilege 15 password 7 0236244818115F3348Decrypt Cisco type 7 password
There are number of freely available tools for decrypting type 7 password. Here are some examples:
- https://www.question-defense.com/2011/08/17/perl-script-to-decode-cisco-type-7-password-hash
- https://gist.github.com/jayswan/1927995
- https://github.com/theevilbit/ciscot7
For instance, to decrypt the above type 7 password using Ciscot7 Python script, simply run:
wget https://raw.githubusercontent.com/theevilbit/ciscot7/master/ciscot7.py
python ciscot7.py -d -p 0236244818115F3348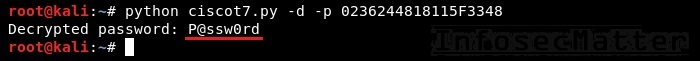
We can instantly see that the password is P@ssw0rd.
There are also numerous decrypters online for this type of password. But we strongly discourage using any them in order to avoid disclosing sensitive customer information (credentials) to a third party.
Cisco type 4 password
This password type was designed around 2013 and the original plan was to use PBKDF2 (Password-Based Key Derivation Function version 2) algorithm. But due to an implementation issue, it somehow ended up being a mere single iteration of SHA256 without salt.
The following example shows type 4 password found in a Cisco configuration:
username admin secret 4 ds4zcEBHQMiiscBff5JmSaUctdI8fVdmGU18HAtxOCwDecrypt Cisco type 4 passwords with John
John the Ripper recognizes this password type as Raw-SHA256. To crack it, we have to first convert it to the following john friendly format and save it in a file:
admin:ds4zcEBHQMiiscBff5JmSaUctdI8fVdmGU18HAtxOCwThen we can crack it like this using a dictionary, for example:
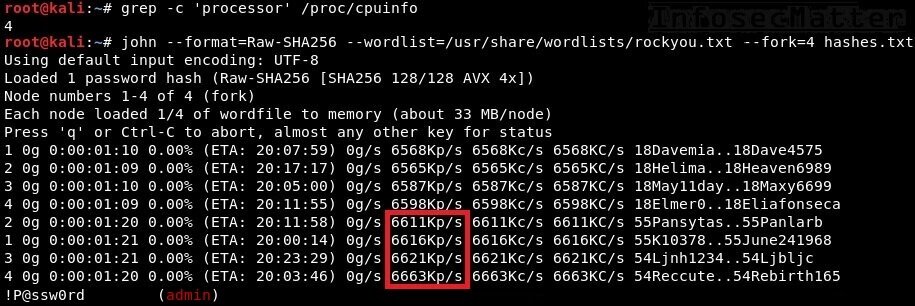
john --format=Raw-SHA256 --wordlist=/usr/share/wordlists/rockyou.txt --fork 4 hashes.txtNote that since we have 4 CPU cores, we can run john in 4 instances using --fork parameter:
From the above screenshot we can see that the average speed is around 26.4 million password attempts per second.
Decrypt Cisco type 4 passwords with Hashcat
Hashcat recognizes this password type as hash mode 5700. To crack it, we can keep using the same john friendly format Then we can crack it like this using a dictionary, for example:
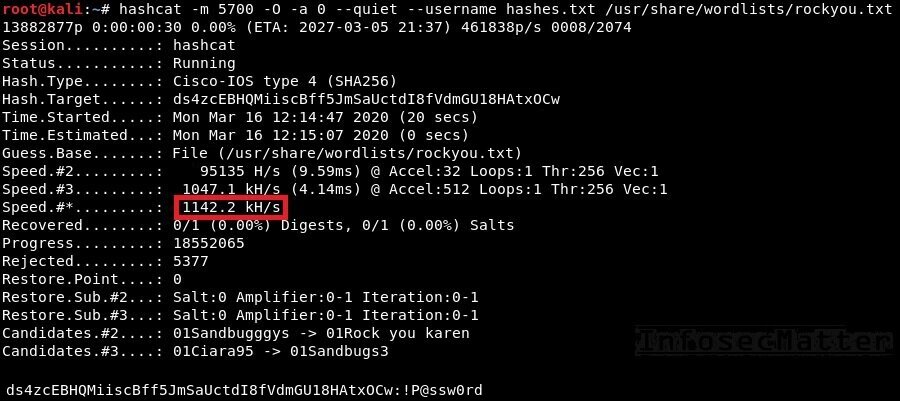
hashcat -m 5700 --username -O -a 0 hashes.txt /usr/share/wordlists/rockyou.txtNote that by using the -O parameter (optimized kernels), we will greatly increase the speed. But it will also limit the password length to 31 characters.
From the above screenshot we can see that the average speed is around 1.14 million password attempts per second. Seems like cracking this hash with john is much faster in our case.
Cisco type 5 password
This password type was introduced around 1992 and it is essentially a 1,000 iteration of MD5 hash with salt. The salt is 4 characters long (32 bits). For modern computers this is not difficult enough and thus in many cases it can be successfully cracked.
The following example shows type 5 password found in a Cisco configuration:
username admin secret 5 $1$jUfy$2TVVXJ8sy.KO8ZhAKfIHt/Decrypt Cisco type 5 passwords with John
John the Ripper recognizes this password type as md5crypt. To crack it, we have to again first convert it to the following john friendly format and save it in a file:
admin:$1$jUfy$2TVVXJ8sy.KO8ZhAKfIHt/Then we can crack it like this using a dictionary, for example:
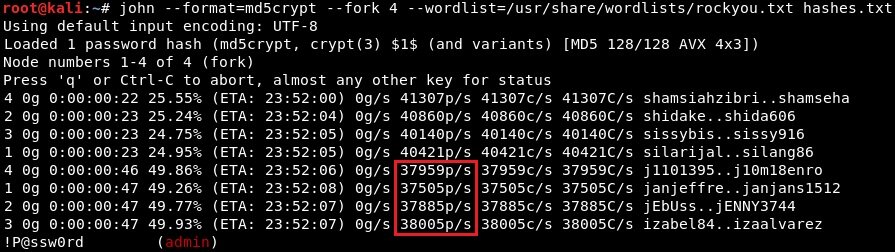
john --format=md5crypt --fork=4 --wordlist=/usr/share/wordlists/rockyou.txt hashes.txtFrom the above screenshot we can see that the average speed is around 155 thousand password attempts per second.
Decrypt Cisco type 5 passwords with Hashcat
Hashcat recognizes this password type as hash mode 500. To crack it, we can keep using the same john friendly format. Then we can crack it like this using a dictionary, for example:
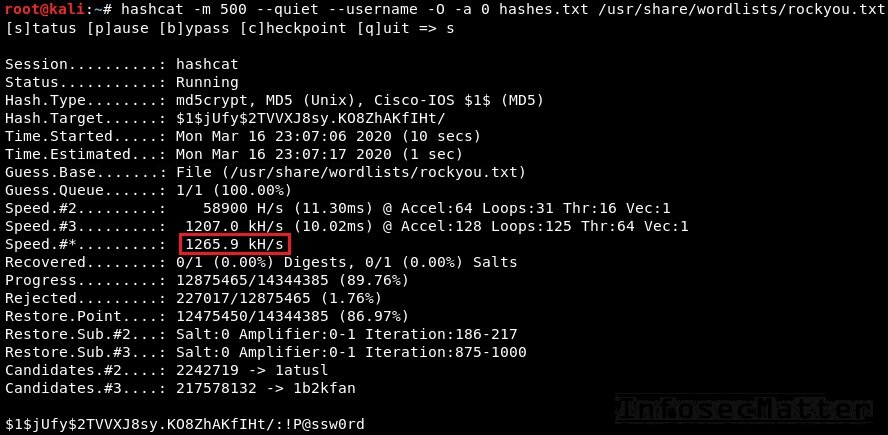
hashcat -m 500 --username -O -a 0 hashes.txt /usr/share/wordlists/rockyou.txtNote that by using the -O parameter (optimized kernels), we will greatly increase the speed. But it will also limit the password length to 31 characters.
From the above screenshot we can see that the average speed is around 1.2 million password attempts per second. Much better than john in our case.
Cisco type 8 password
This password type is a proper implementation of the failed password type 4. This time it really uses the PBKDF2 algorithm and 10 character salt (80 bits). Essentially it is 20,000 iterations of SHA256 and this makes it much harder to crack in comparison with the previous password types.
The following example shows type 8 password found in a Cisco configuration:
username admin secret 8 $8$dsYGNam3K1SIJO$7nv/35M/qr6t.dVc7UY9zrJDWRVqncHub1PE9UlMQFsDecrypt Cisco type 8 passwords with John
John the Ripper recognizes this password type as pbkdf2-hmac-sha256. To crack it, we have to again first convert it to the following john friendly format and save it in a file:
admin:$8$dsYGNam3K1SIJO$7nv/35M/qr6t.dVc7UY9zrJDWRVqncHub1PE9UlMQFsThen we can crack it like this using a dictionary, for example:
john --format=pbkdf2-hmac-sha256 --fork=4 --wordlist=/usr/share/wordlists/rockyou.txt hashes.txtFrom the above screenshot we can see that the average speed is around 1,200 password attempts per second. Not much.
Decrypt Cisco type 8 passwords with Hashcat
Hashcat recognizes this password type as hash mode 9200. To crack it, we can keep using the same john friendly format. Then we can crack it like this using a dictionary, for example:
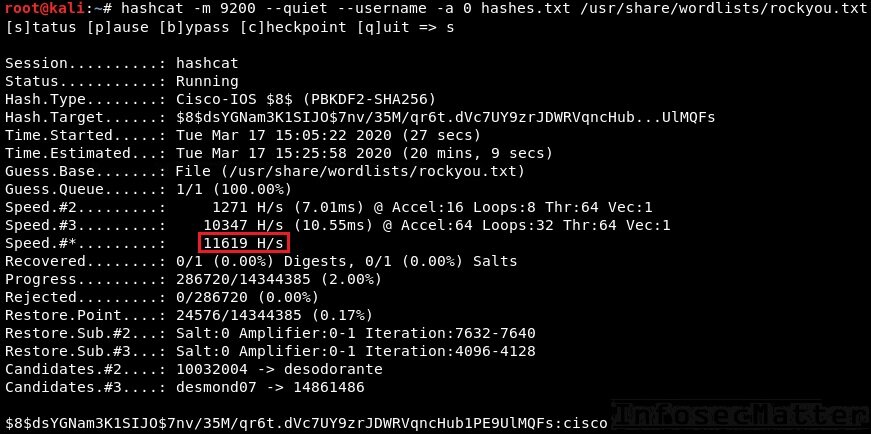
hashcat -m 9200 --username -a 0 hashes.txt /usr/share/wordlists/rockyou.txtFrom the above screenshot we can see that the average speed is around 11,600 password attempts per second. It’s definitely faster than john in our case, but in overall it’s not very fast.
Cisco type 9 password
This password type uses Scrypt algorithm. Scrypt was specifically designed to make cracking very difficult even on large-scale cracking rigs with many GPUs or hardware ASICs. This is due to the fact that Scrypt requires large amount of memory to perform its function.
The following example shows type 9 password found in a Cisco configuration:
username admin secret 9 $9$nhEmQVczB7dqsO$X.HsgL6x1il0RxkOSSvyQYwucySCt7qFm4v7pqCxkKMDecrypt Cisco type 9 passwords with John
John the Ripper recognizes this password type as scrypt. To crack it, we have to again first convert it to the following john friendly format and save it in a file:
admin:$9$nhEmQVczB7dqsO$X.HsgL6x1il0RxkOSSvyQYwucySCt7qFm4v7pqCxkKMThen we can crack it like this using a dictionary, for example:
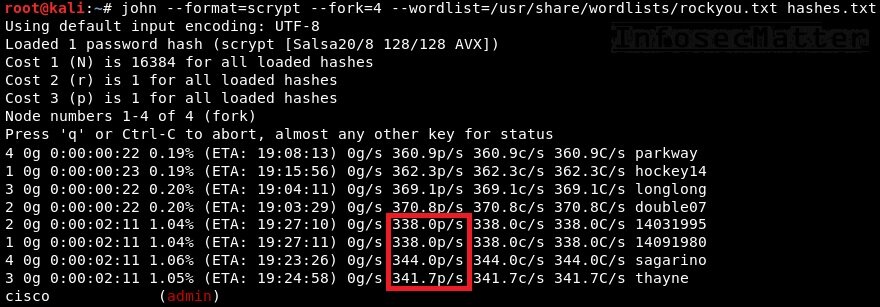
john --format=scrypt --fork=4 --wordlist=/usr/share/wordlists/rockyou.txt hashes.txtFrom the above screenshot we can see that the average speed is around 1,400 password attempts per second. Not much.
Decrypt Cisco type 9 passwords with Hashcat
Hashcat recognizes this password type as hash mode 9300. To crack it, we can keep using the same john friendly format. Then we can crack it like this using a dictionary, for example:
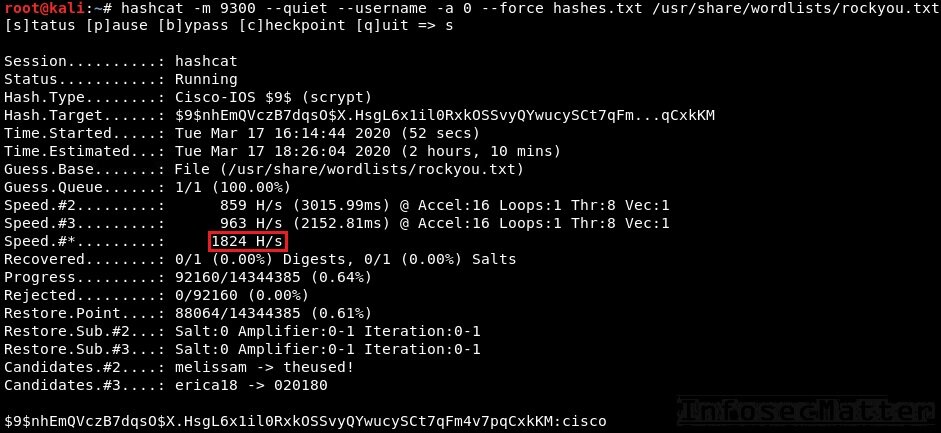
hashcat -m 9300 --username -a 0 --force hashes.txt /usr/share/wordlists/rockyou.txtNote that we have to provide --force parameter since the hash-mode 9300 is marked as unstable for our particular device.
From the above screenshot we can see that the average speed is around 1,800 password attempts per second. Not much either.
Cracking tips
Use KoreLogic custom rules
John the Ripper contains very useful ruleset for generating passwords called KoreLogic. This ruleset originated in DEFCON 2010 contest and it is a great way of generating passwords from patterns or when traditional dictionary attack fails.
To make use of it, simply create a dictionary with patterns like this e.g.:
infosec
infosecmatter
infosec matterSave it into patterns.txt file. Then simply run john like this:
john --wordlist=patterns.txt --rules=korelogic ...Chain John the Ripper with Hashcat
Although there has been some efforts to convert the aforementioned KoreLogic rules into Hashcat, the result is only partial. Fortunately, we can chain together John the Ripper with Hashcat to make it use KoreLogic rules in full.
Simply generate the passwords using John the Ripper on the stdout and feed them into Hashcat using pipe like this:
john --wordlist=patterns.txt --rules=korelogic --stdout | hashcat ...The same method can be used for any ruleset that we have created in the john format.
Hopefully you can crack some Cisco hashes with these tips.